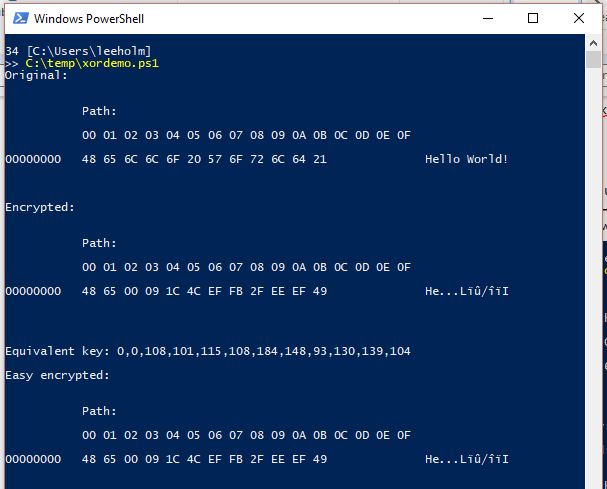
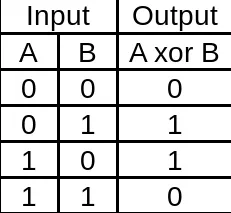
GitHub - vineetkia/XOR-ENCRYPTiON-CPP: XOR-Cryptography Method To Encrypt Data ( String ) Using A Unique KEY Using C++

Unlocking the Power of XOR: A Blockchain Architect's Personal Journey with Cryptography's Secret Weapon

AES key expansion: simple XOR operation for all but the first word in... | Download Scientific Diagram
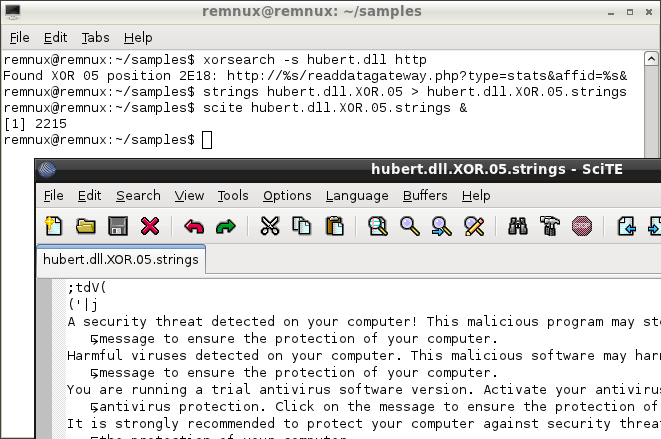


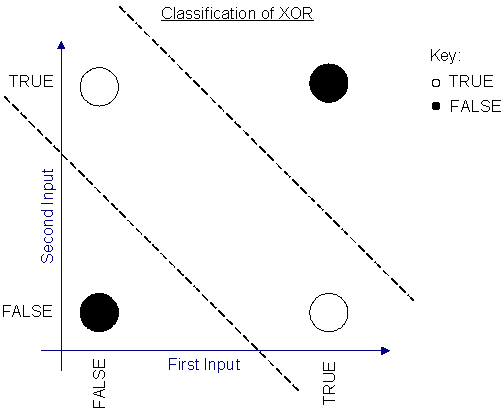






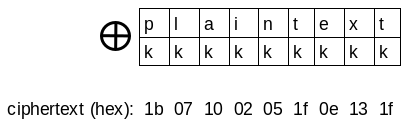


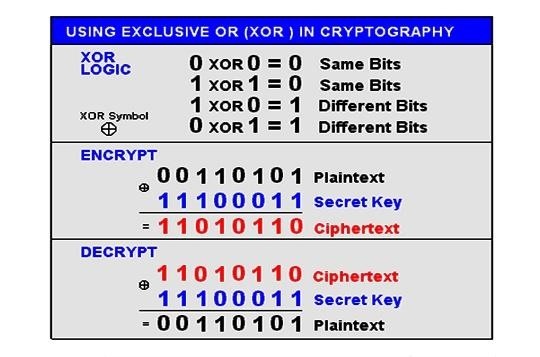
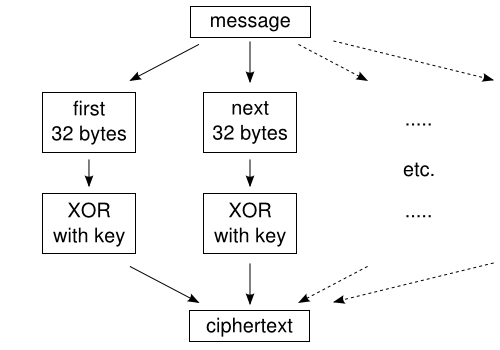
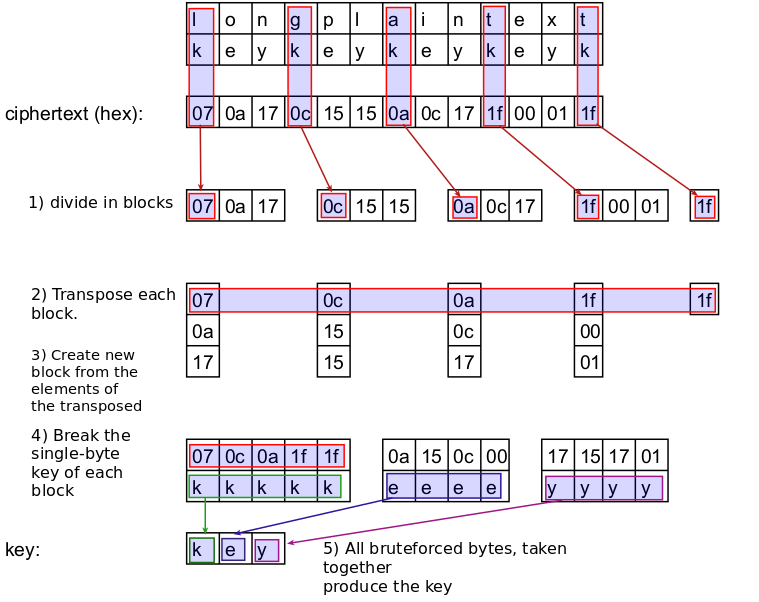

![1.3.1 Single Byte XOR - Learning Malware Analysis [Book] 1.3.1 Single Byte XOR - Learning Malware Analysis [Book]](https://www.oreilly.com/api/v2/epubs/9781788392501/files/assets/9cb52b5d-564e-4ecc-8cc8-d7e4b725d664.png)