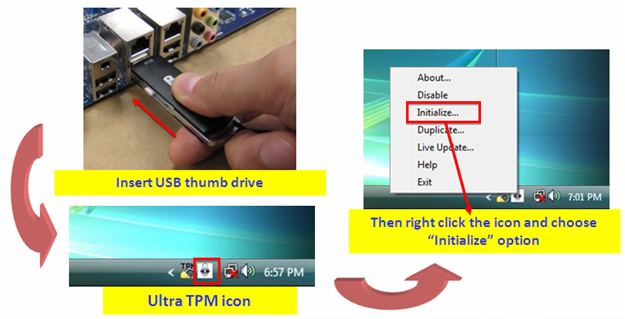
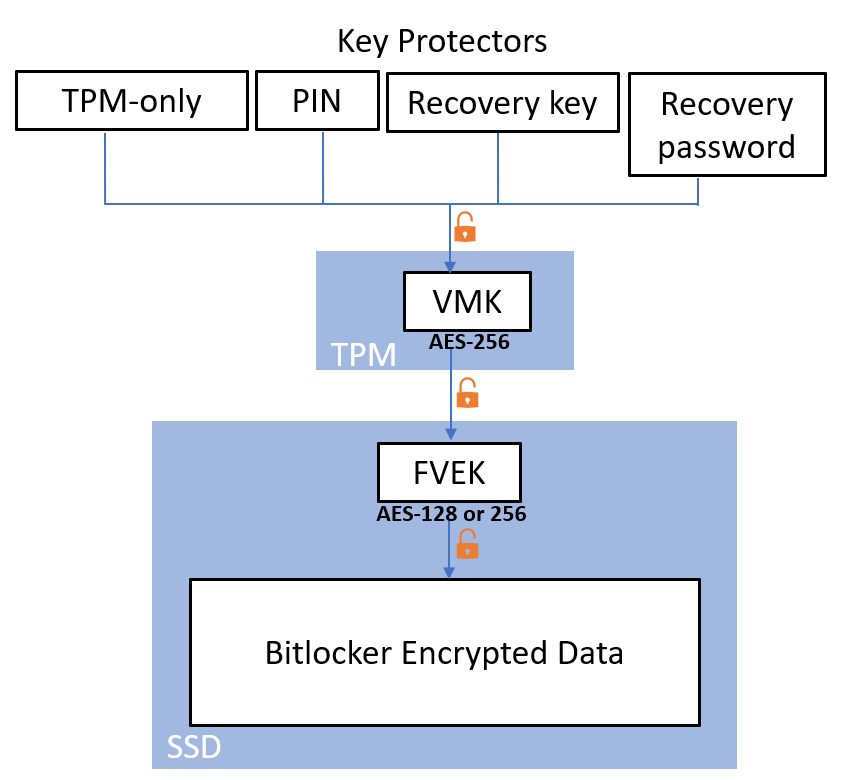
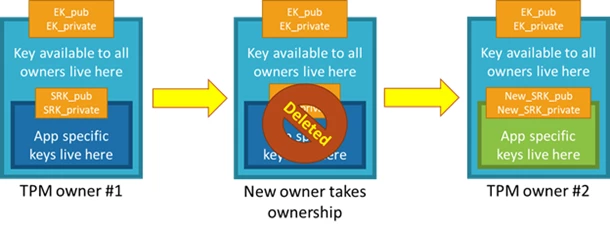
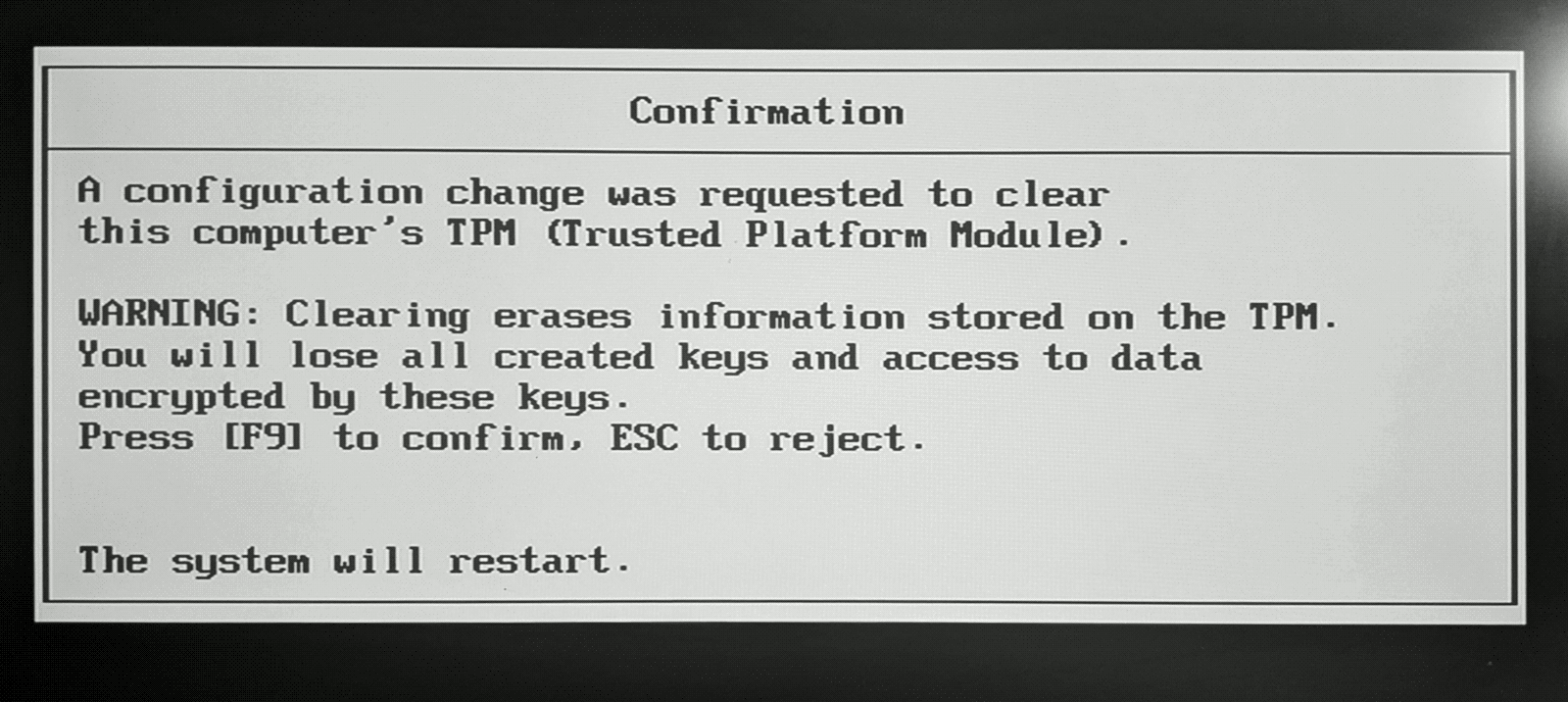
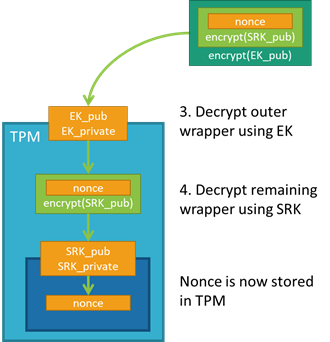
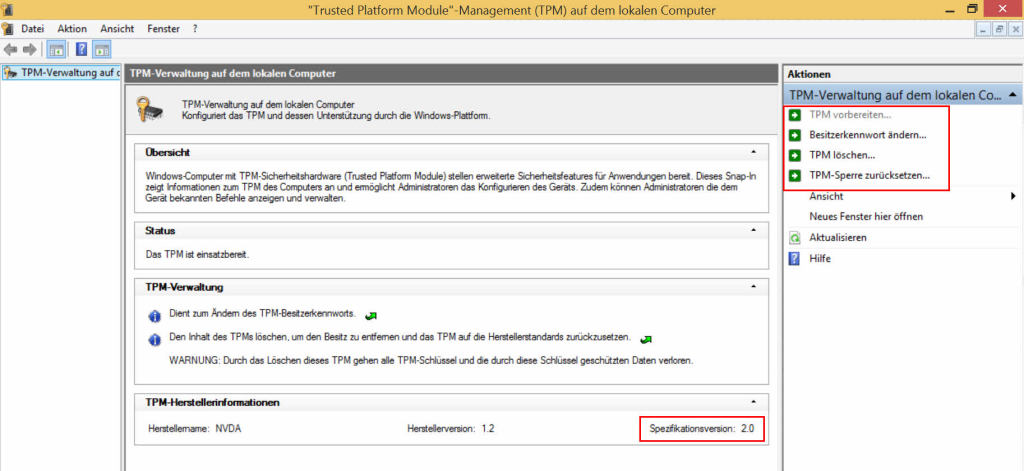
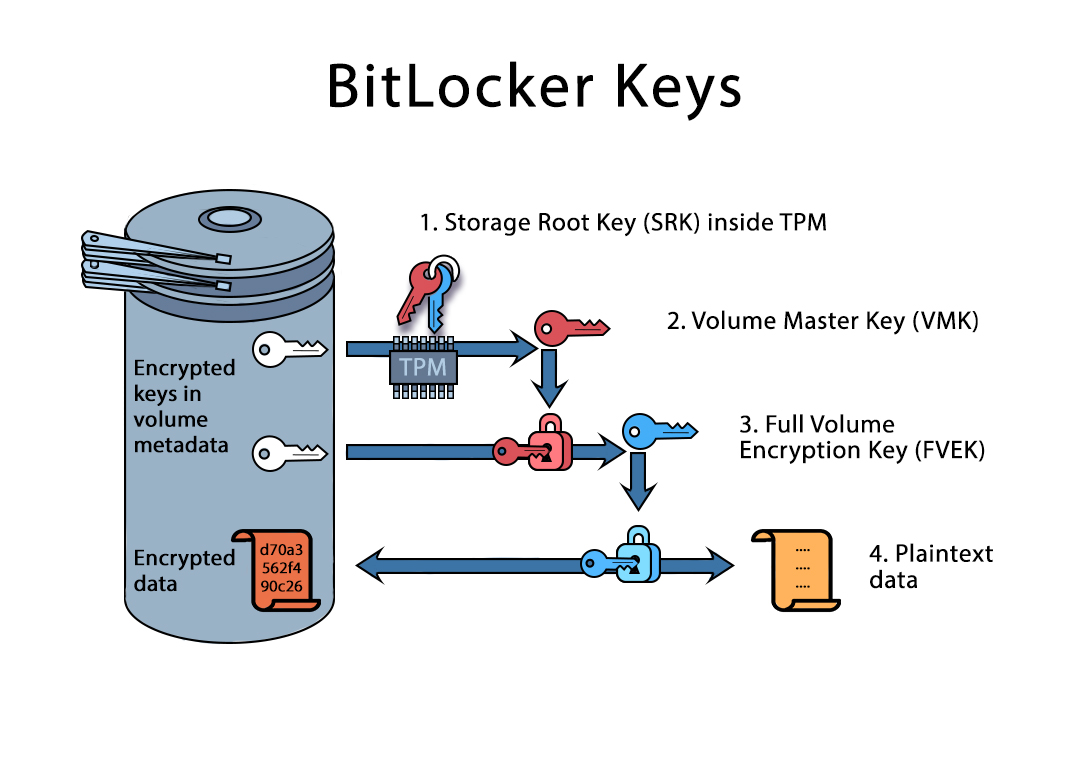
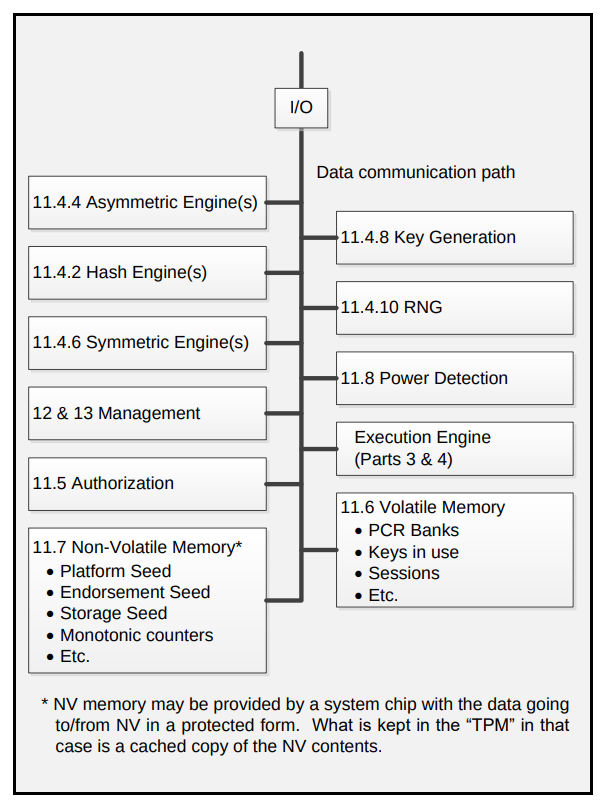
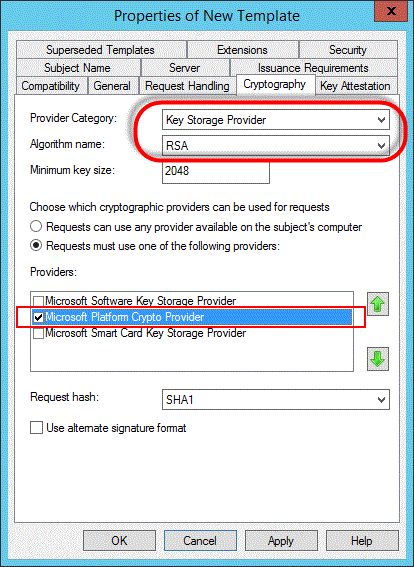
Data firewall trusted platform module (TPM) key tree. SRK: storage root... | Download Scientific Diagram

TPM 2.0 Modul, 14 Pin LPC Interface Encryption Security Module Encryption Key Stable Performance TPM Module for MSI 14Pin LPC TPM 2.0: Amazon.de: Computer & Zubehör

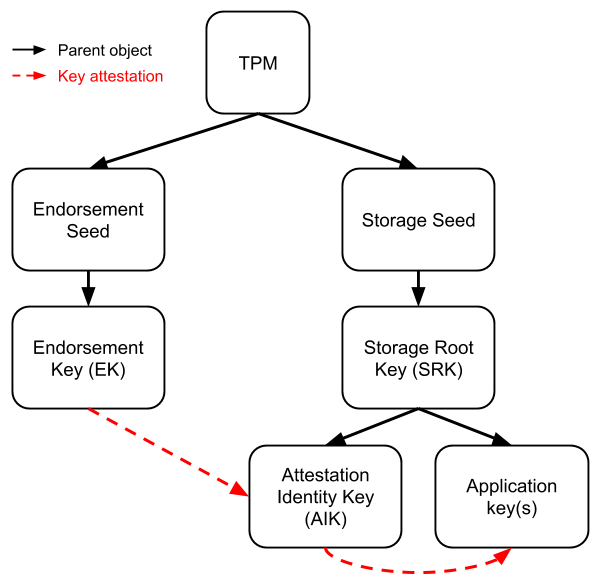
TKM Key Hierarchy Having in mind that TPM protected keys are bound to a... | Download Scientific Diagram