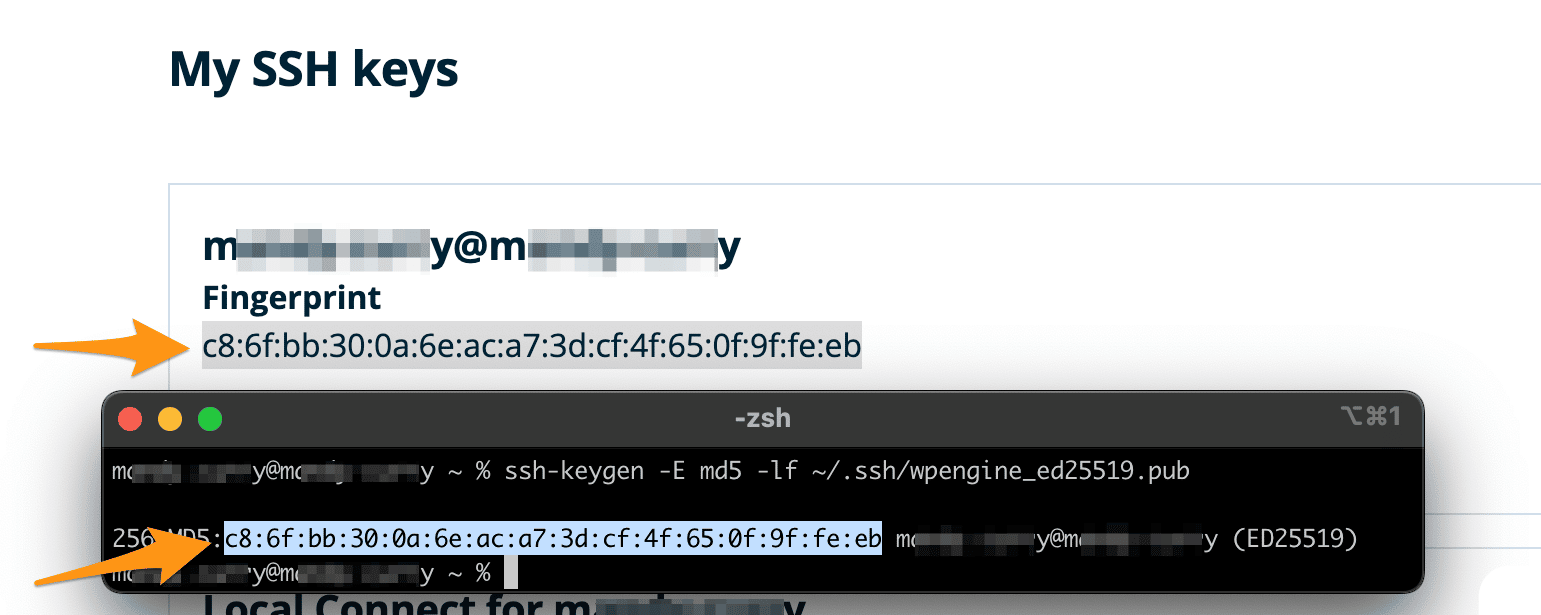
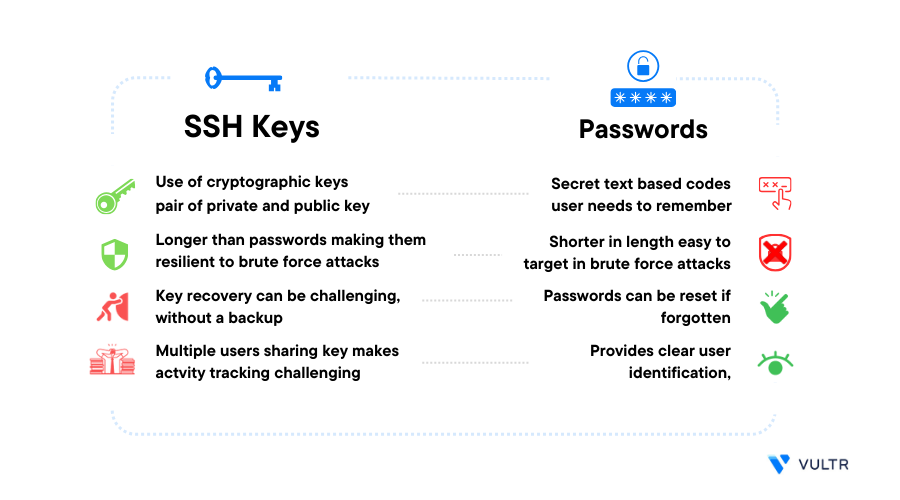
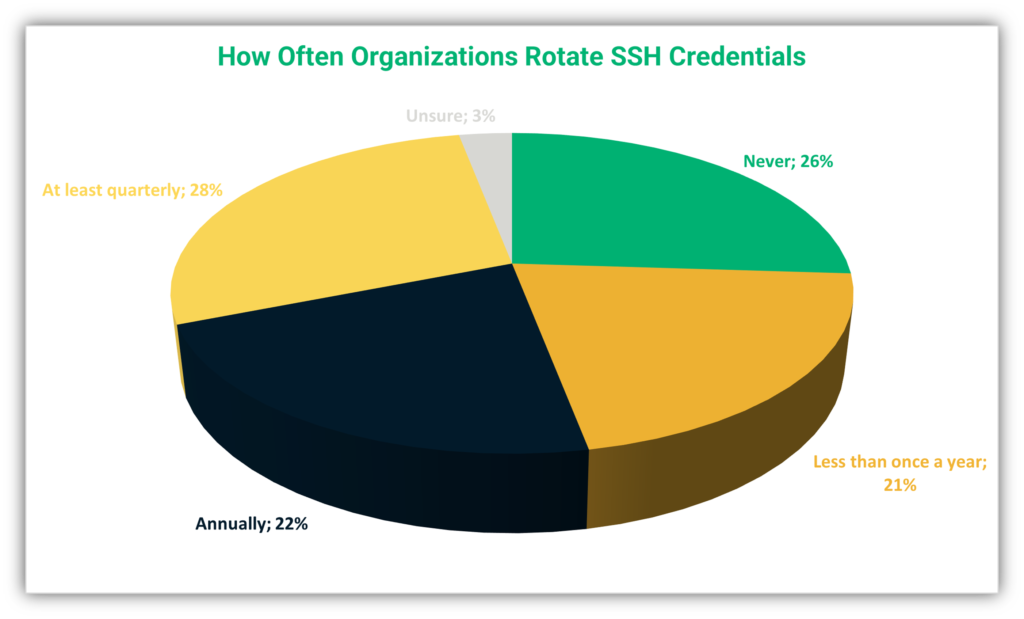
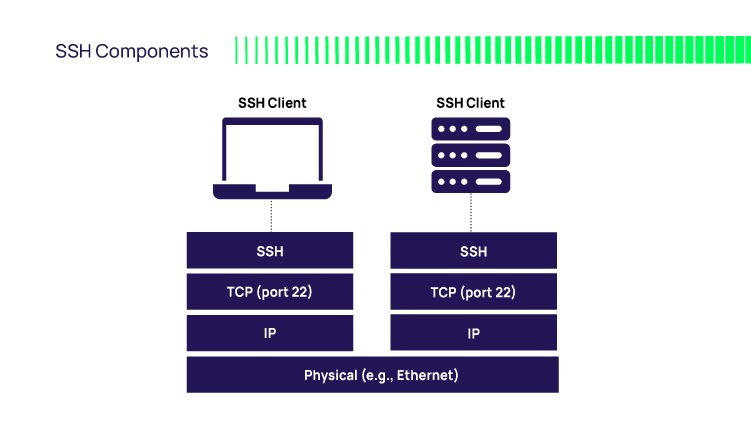
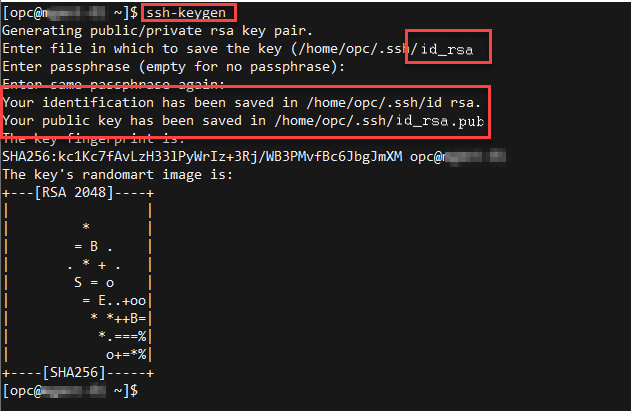
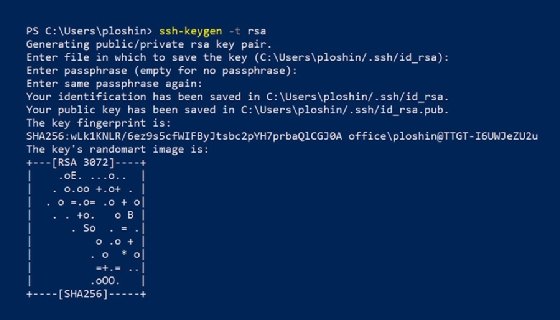
How to Generate SSH Key Pairs with Best Practices — Sharpen Your Basic CLI Commands | by Luis Torres | Medium

privacy - Best Practice: ”separate ssh-key per host and user“ vs. ”one ssh- key for all hosts“ - Information Security Stack Exchange







![How to SSH Through Bastion With Key [Tutorial] How to SSH Through Bastion With Key [Tutorial]](https://www.strongdm.com/hubfs/Imported_Blog_Media/605d2d6a167a08c89f896241_StrongDM2-SSH-through-bastion-server-with-key-2.jpg#keepProtocol)