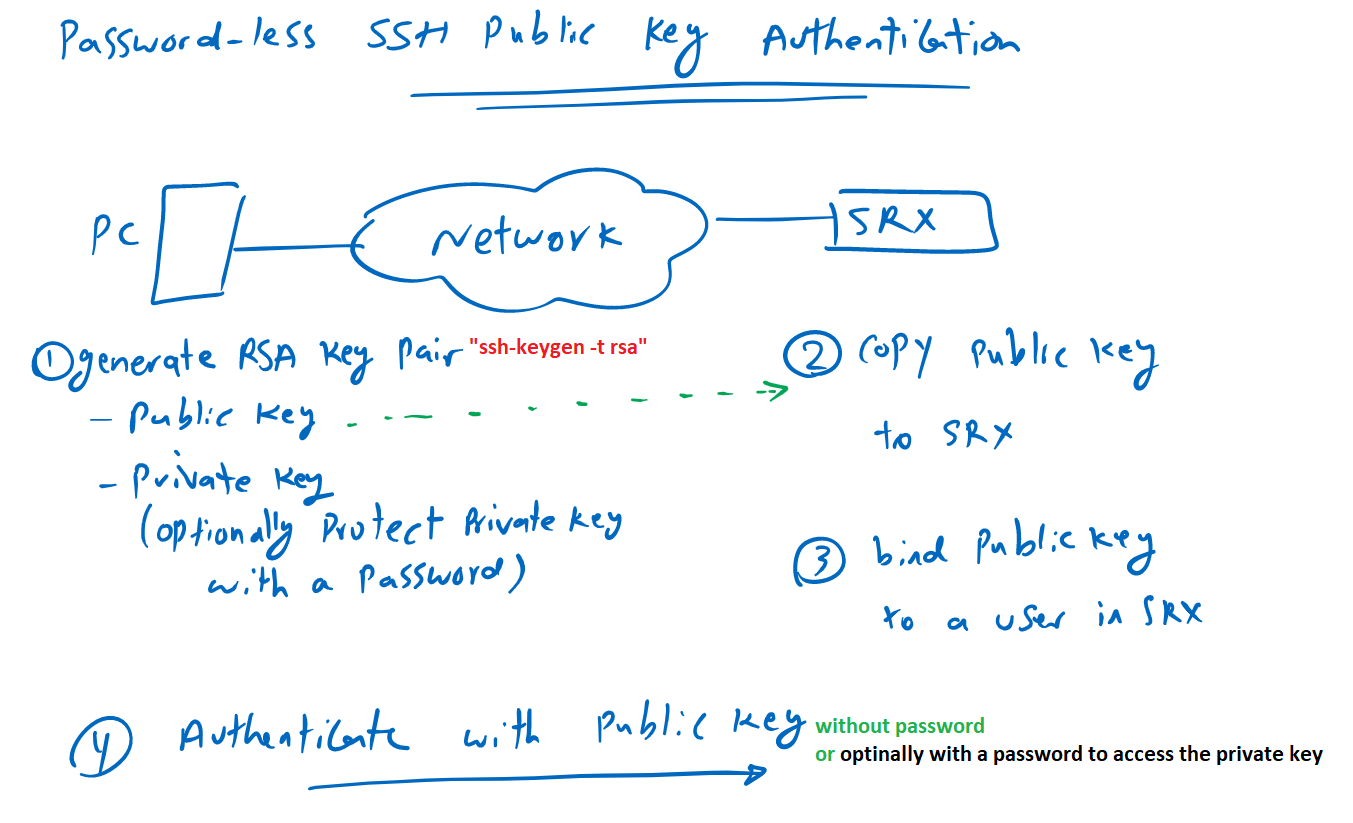
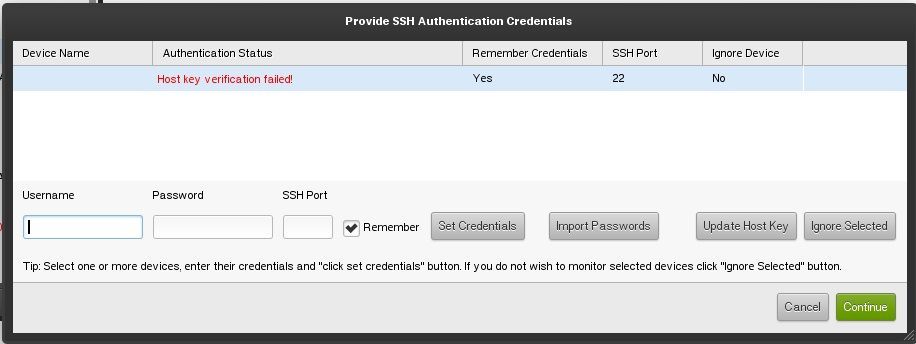
Backups to an SSH destination with SSH key auth - more questions - Help! (Home for newbies) - Virtualmin Community
Enable gpg-key and ssh-key to ignore duplicate keys to better support automation scenarios · Issue #5085 · cli/cli · GitHub
ssh-agent is ignored when with "IdentitiesOnly yes" config file setting · Issue #1550 · PowerShell/Win32-OpenSSH · GitHub
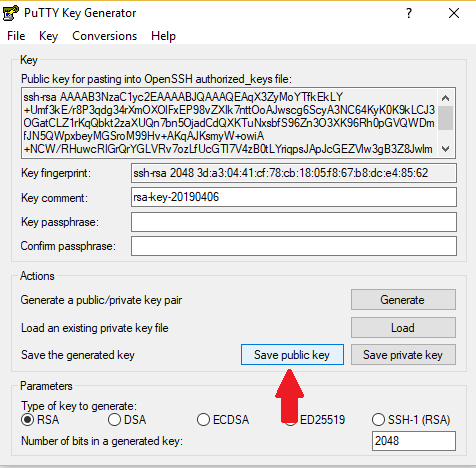
Generating SSH Keys for SFTP/SSH (FileZilla, Cyberduck, Dreamweaver, etc.) | Information Technology and Computing Support | Oregon State University





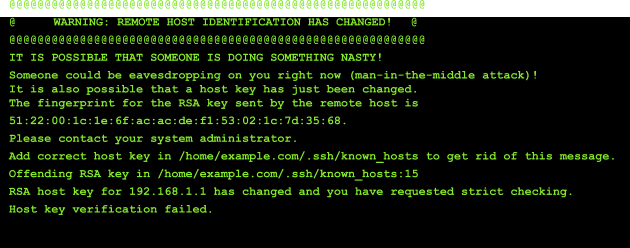





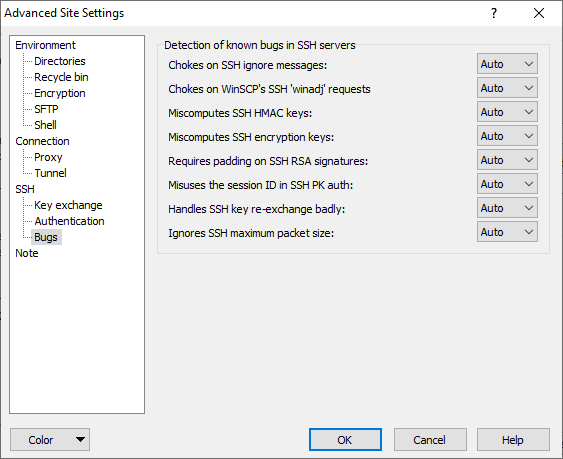



![NBug] SSH key file could not be found · Issue #10650 · gitextensions/gitextensions · GitHub NBug] SSH key file could not be found · Issue #10650 · gitextensions/gitextensions · GitHub](https://user-images.githubusercontent.com/60372864/212601693-8c30ec90-6eb9-4e5b-adb7-51e160a04c43.png)