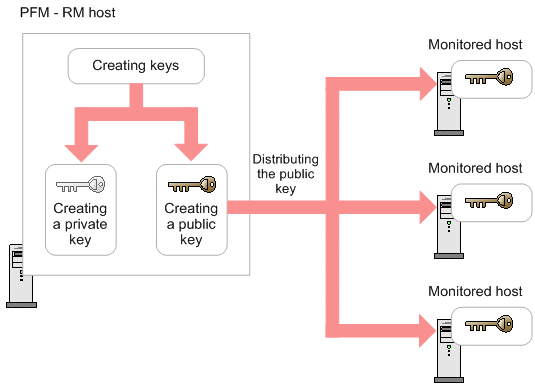
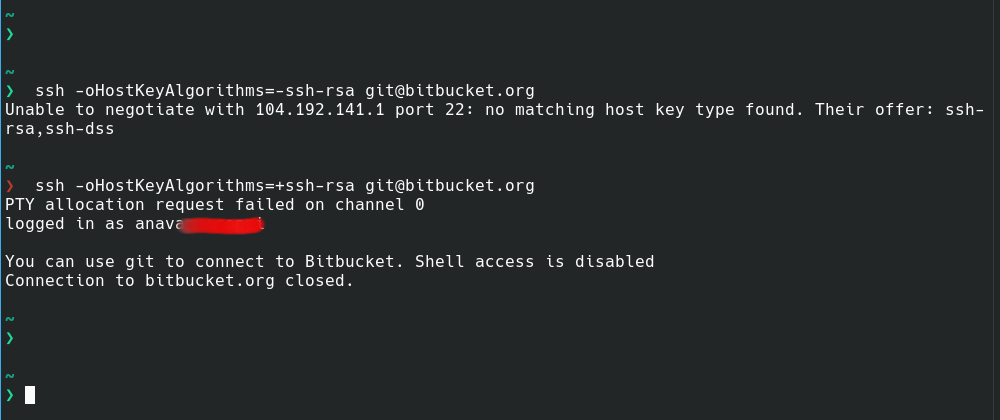
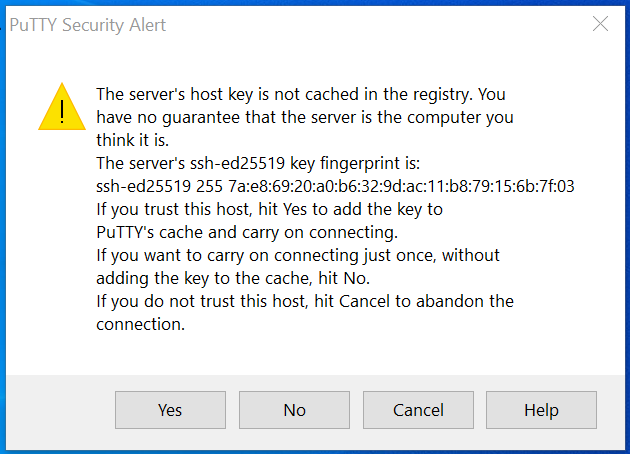
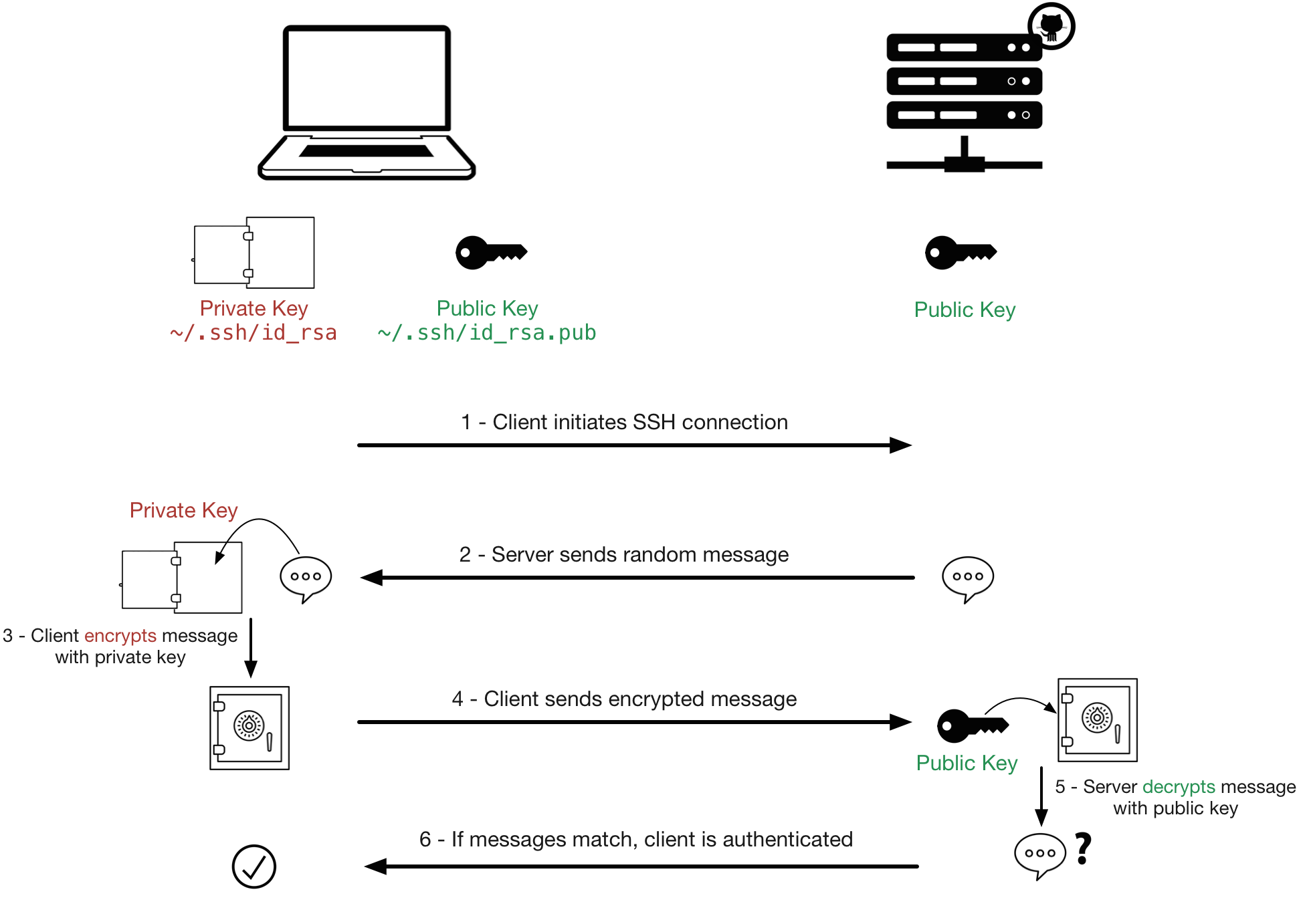
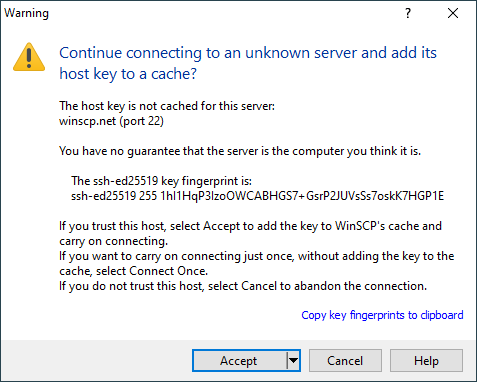
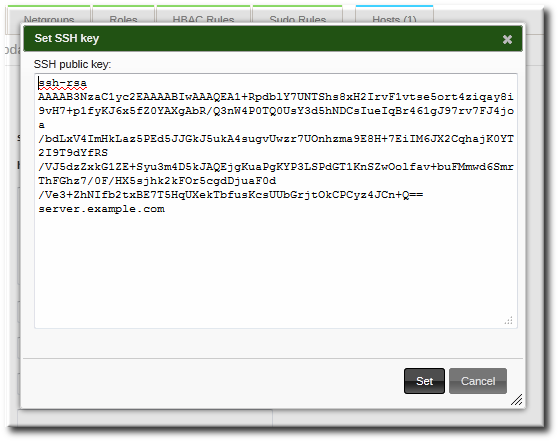
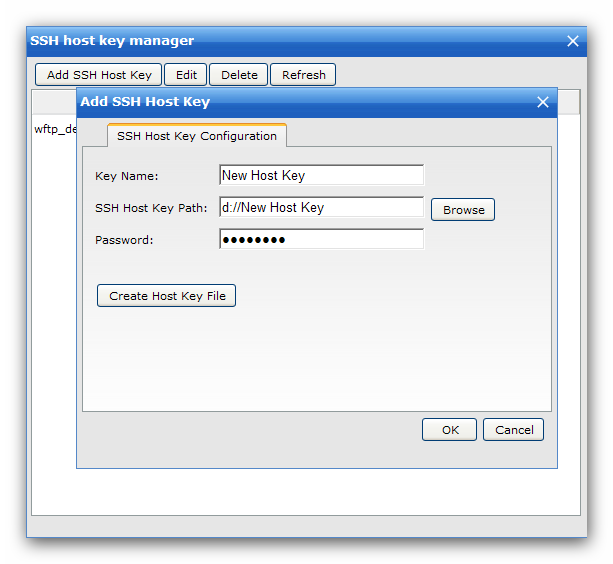
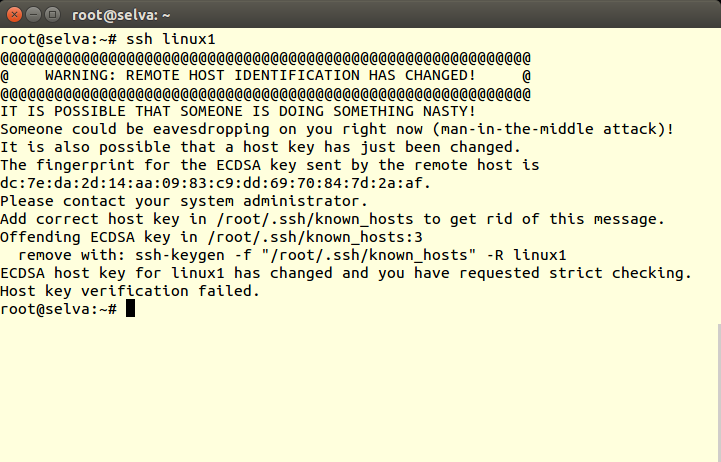
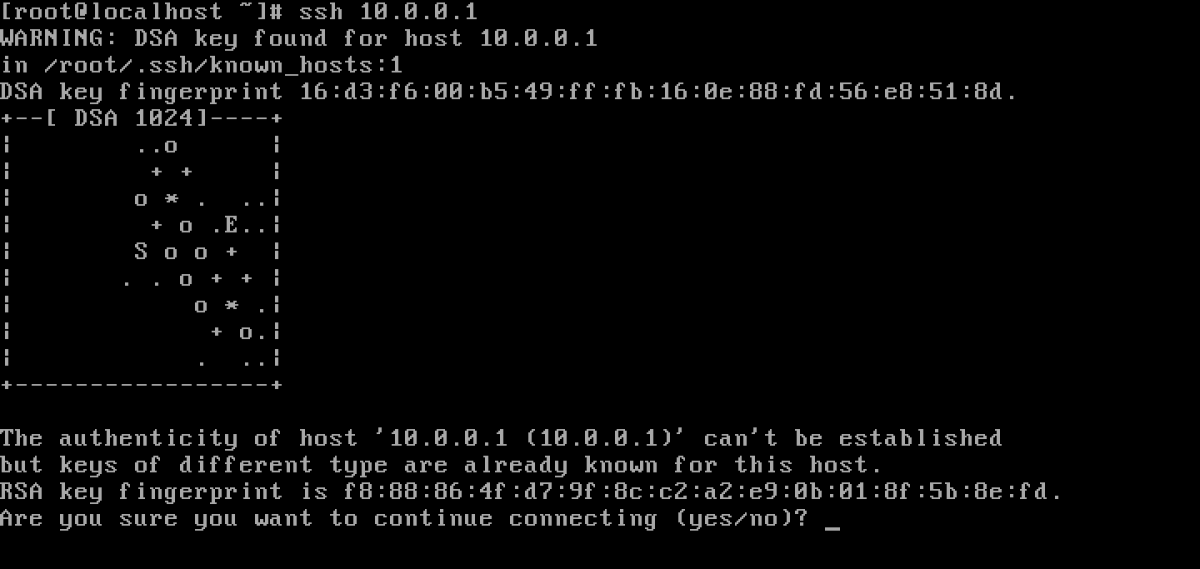
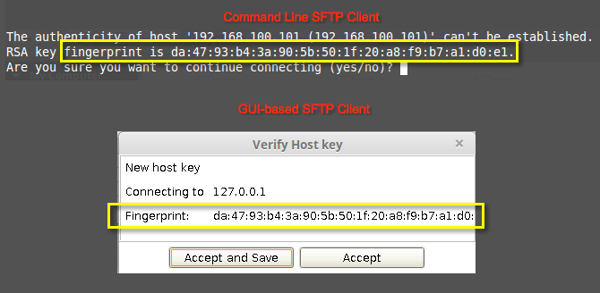
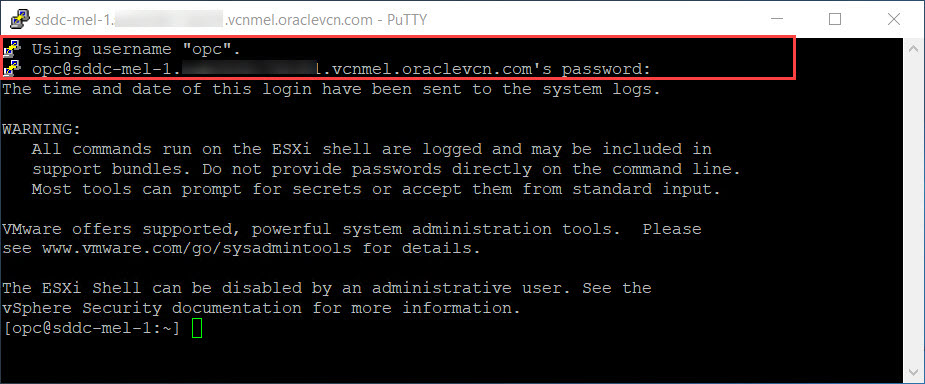
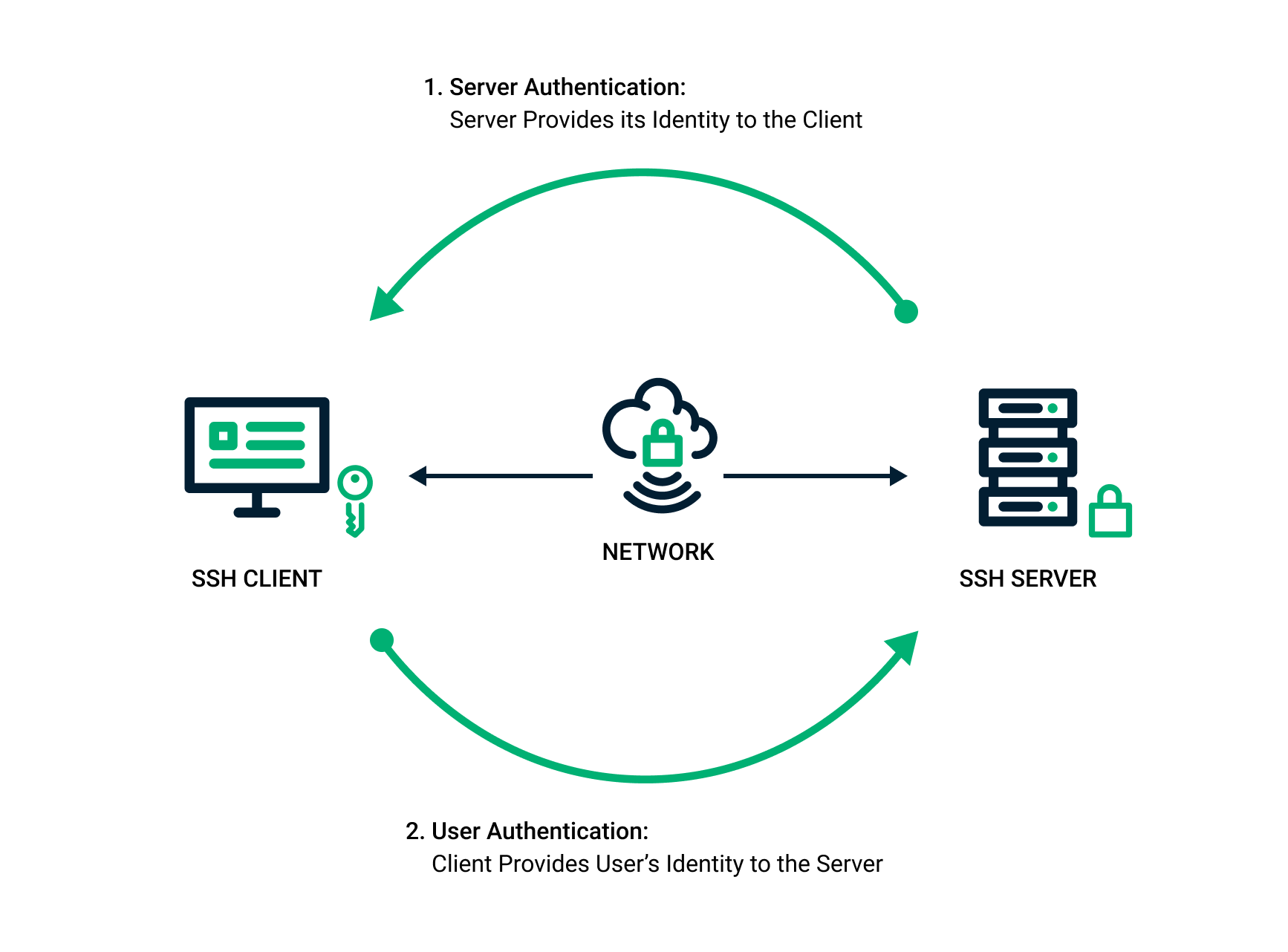
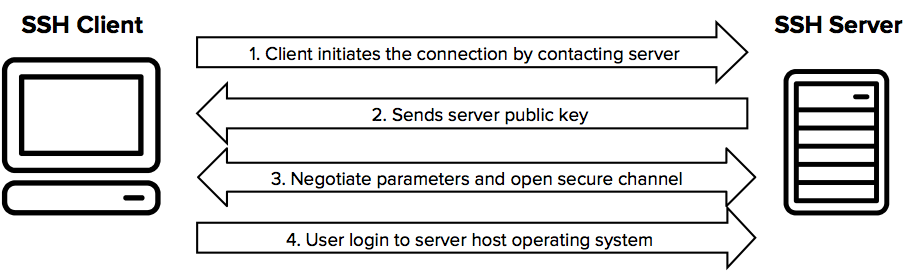
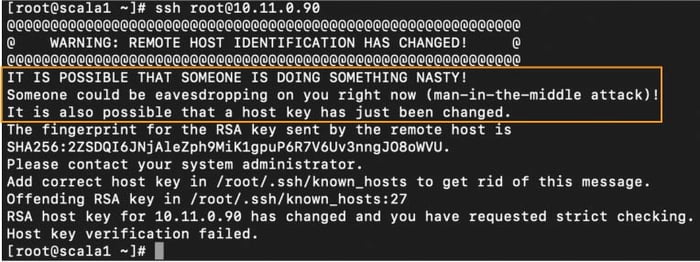
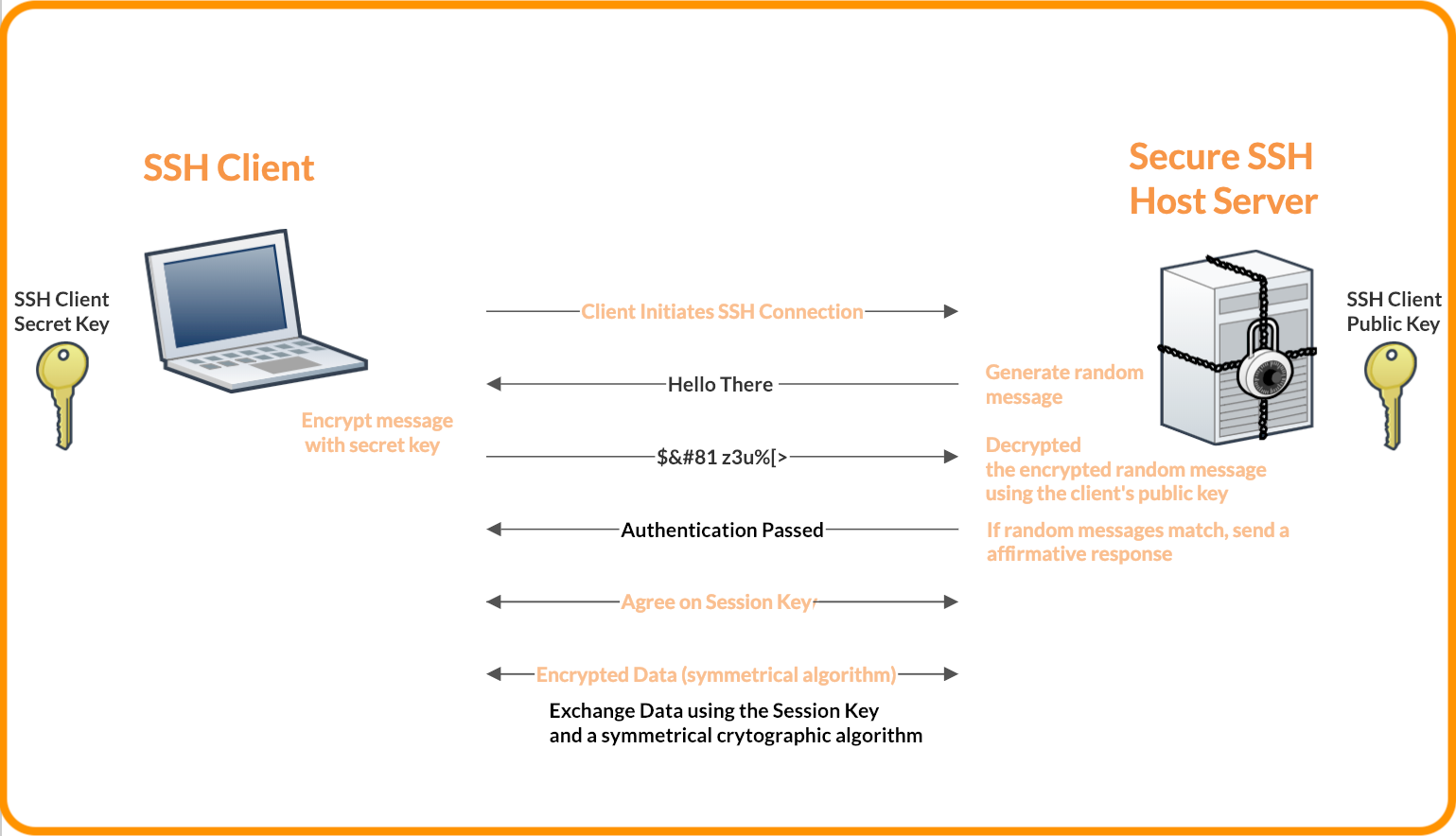
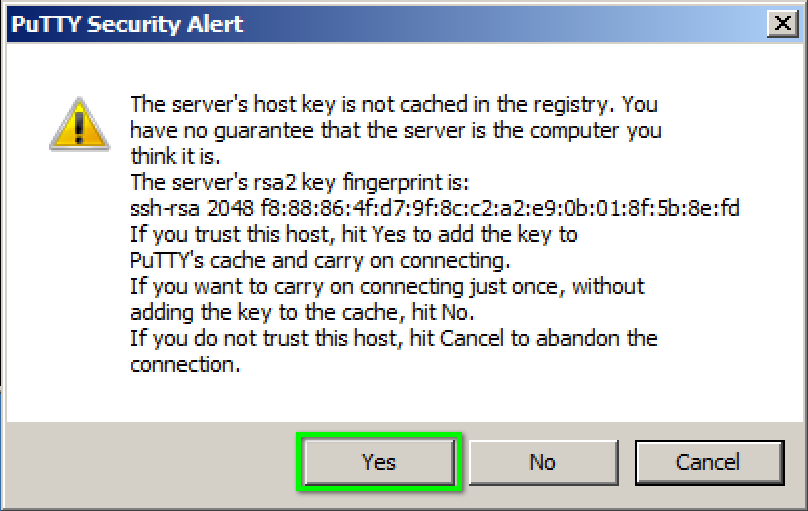
SSH keys are simply known as secure shells; it works like a cryptographic protocol which is used for public key cryptography to o… | Key, Secure shell, Cryptography

What can i do with the ssh host key i got from this nmap scan. (Hack the box) - Information Security Stack Exchange