Mercedes ECU Unlock via NEW SEED KEY Calculator 3.0 & Coding in Vediamo / Tips For Encoding Vediamo - YouTube

SEED Encryption: A Highly Secure Method for Protecting Sensitive Data | 2023 | by Karthikeyan Nagaraj | Medium
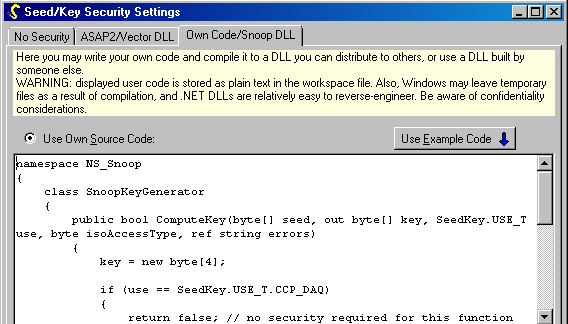
What is a Seed-Key Exchange? Shortcomings of Current Seed-Key Exchanges Cracking an ECU's Seed-Key Exchange Experimental Hardw

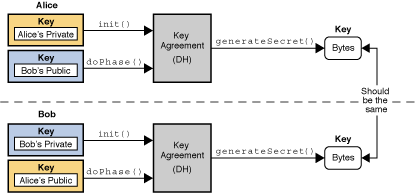
Nano How 1: Seeds and Keys. What are seeds, private and public… | by Guilherme Lawless | Nano Education | Medium
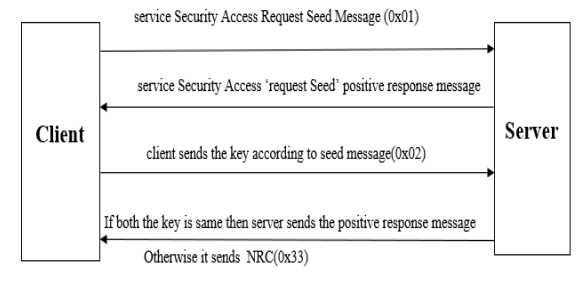
Enhancing Security in UDS Seed-Key Exchange: Best Practices and Implementation Strategies | by Muhammet Kalaycı | Medium

A lightweight block encryption algorithm for narrowband internet of things | Peer-to-Peer Networking and Applications


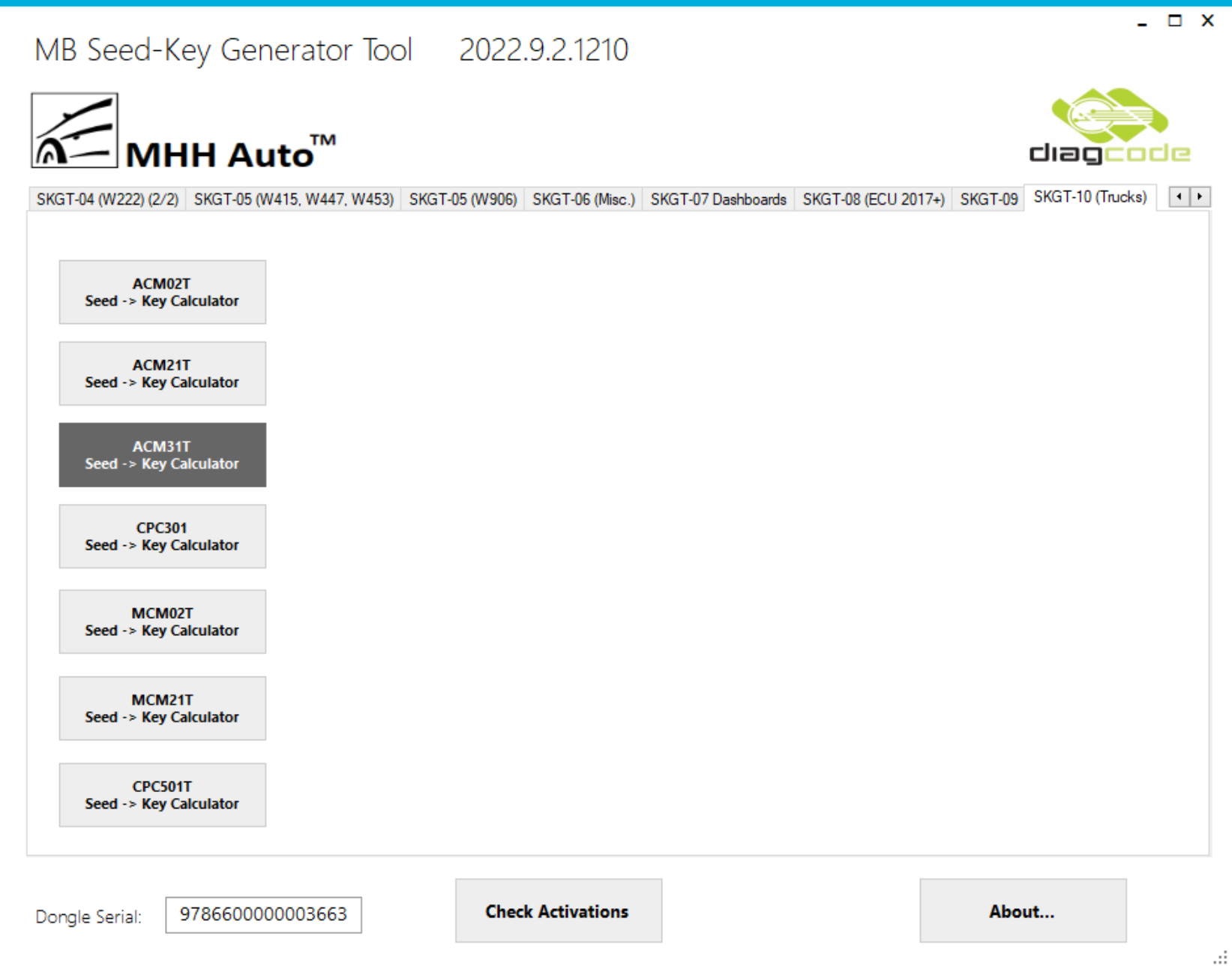

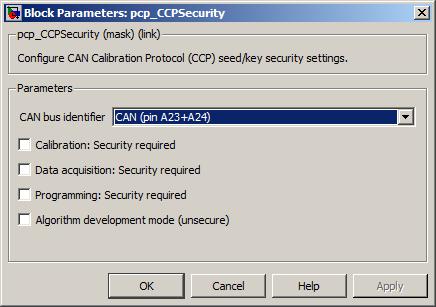
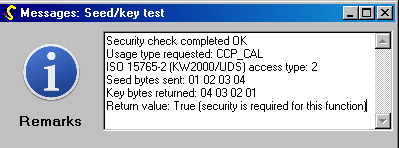
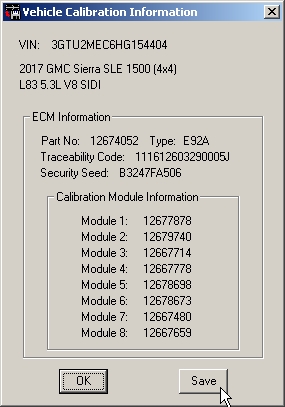

![manual:security [OpenBLT Bootloader] manual:security [OpenBLT Bootloader]](https://www.feaser.com/openblt/lib/exe/fetch.php?media=manual:microboot_xcp_seedkey_protection.png)