
Nano How 1: Seeds and Keys. What are seeds, private and public… | by Guilherme Lawless | Nano Education | Medium
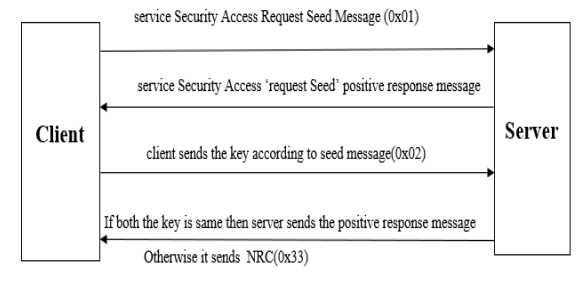
Enhancing Security in UDS Seed-Key Exchange: Best Practices and Implementation Strategies | by Muhammet Kalaycı | Medium

Enhancing Security in UDS Seed-Key Exchange: Best Practices and Implementation Strategies | by Muhammet Kalaycı | Medium
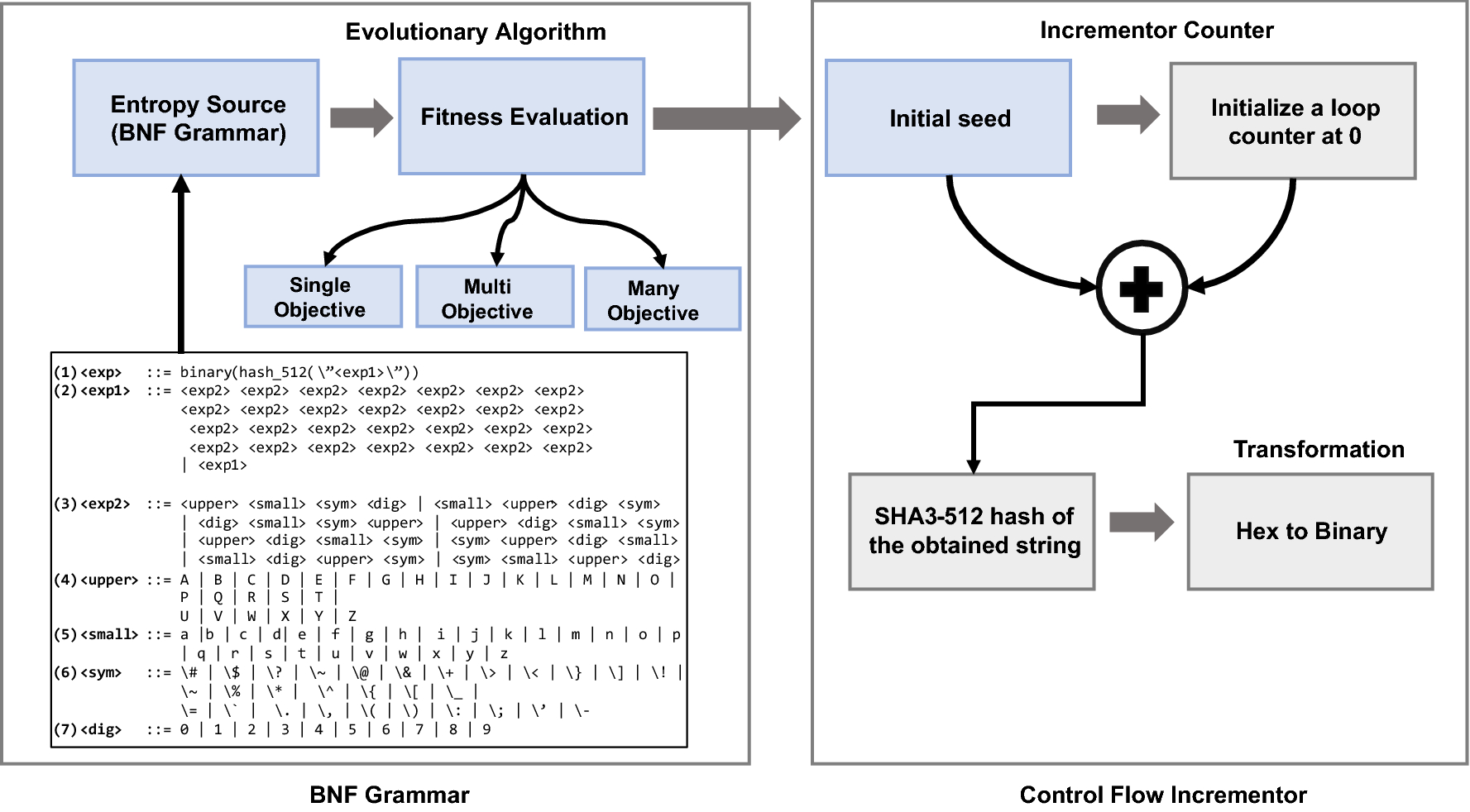
Design of a cryptographically secure pseudo random number generator with grammatical evolution | Scientific Reports
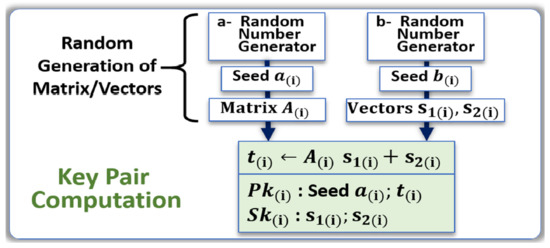
Applied Sciences | Free Full-Text | Post Quantum Cryptographic Keys Generated with Physical Unclonable Functions

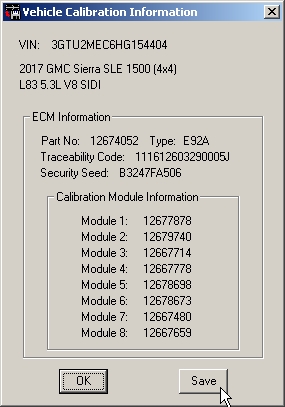


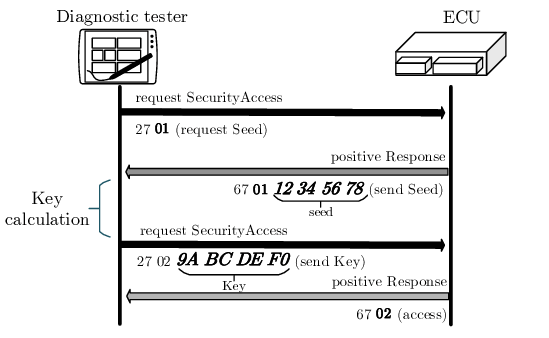

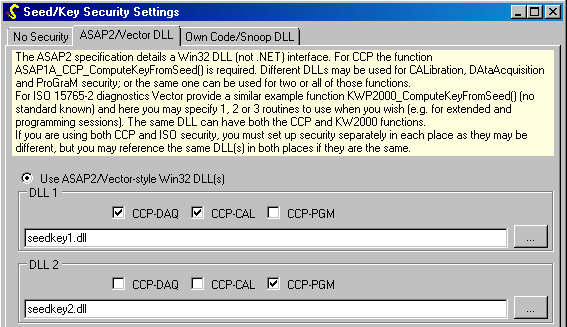



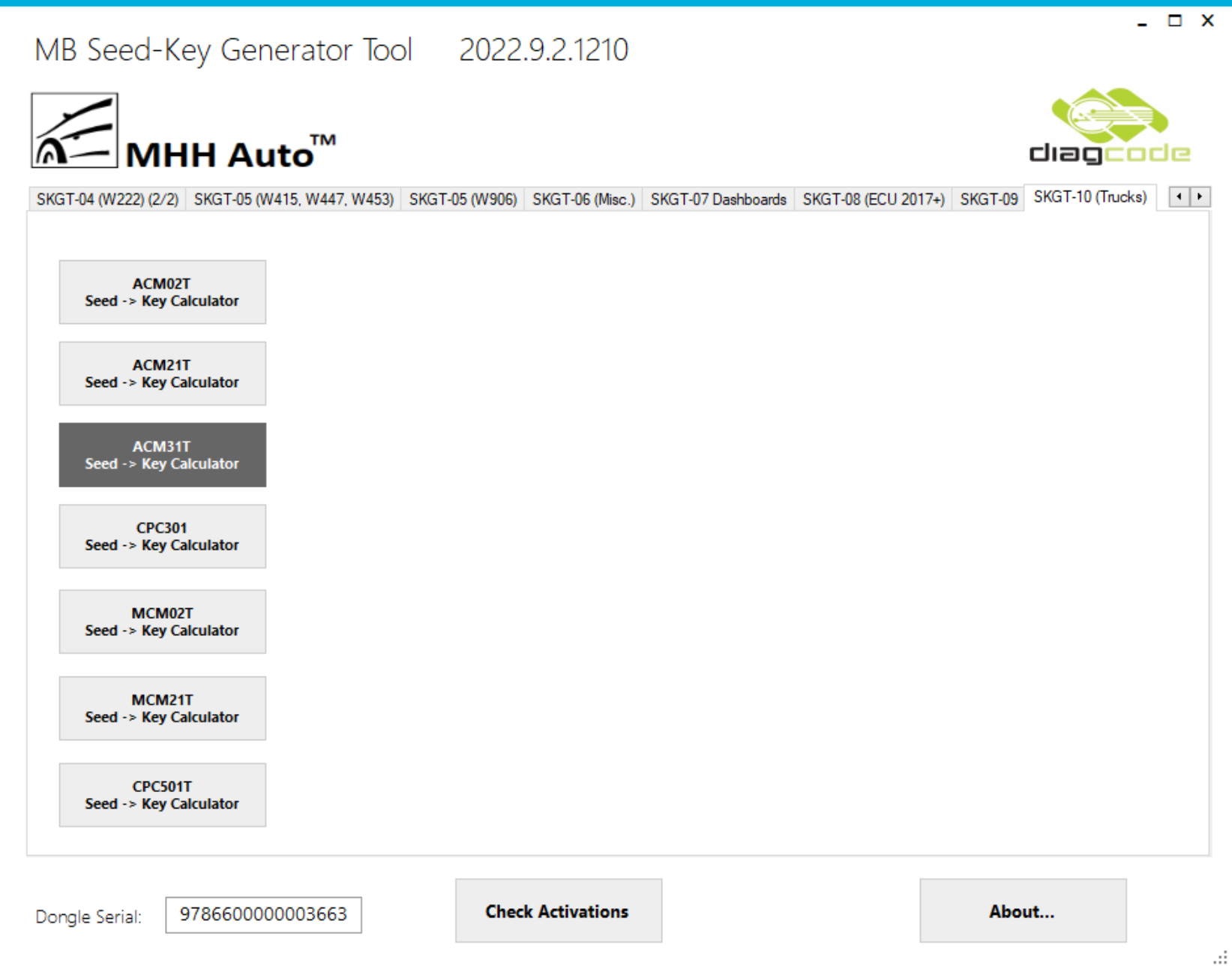


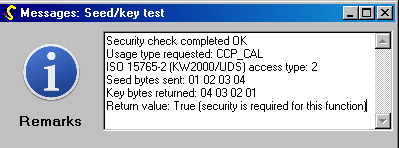





![manual:security [OpenBLT Bootloader] manual:security [OpenBLT Bootloader]](https://www.feaser.com/openblt/lib/exe/fetch.php?media=manual:microboot_xcp_seedkey_protection.png)