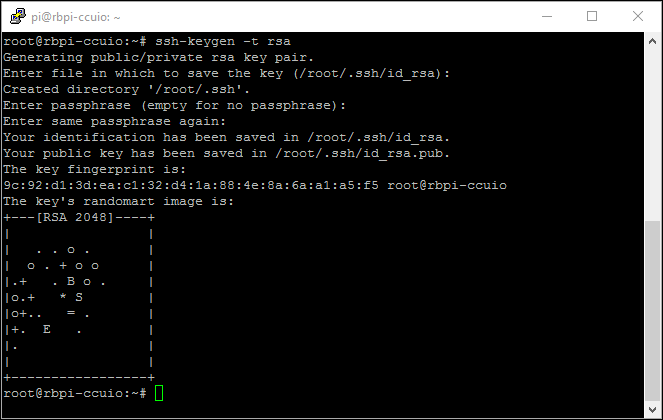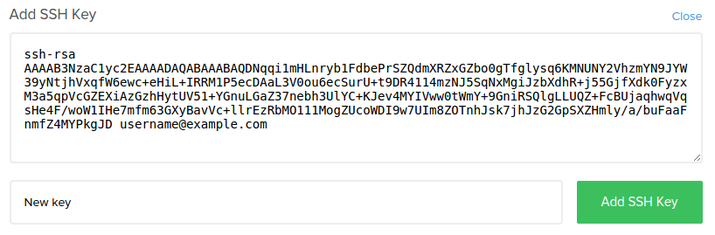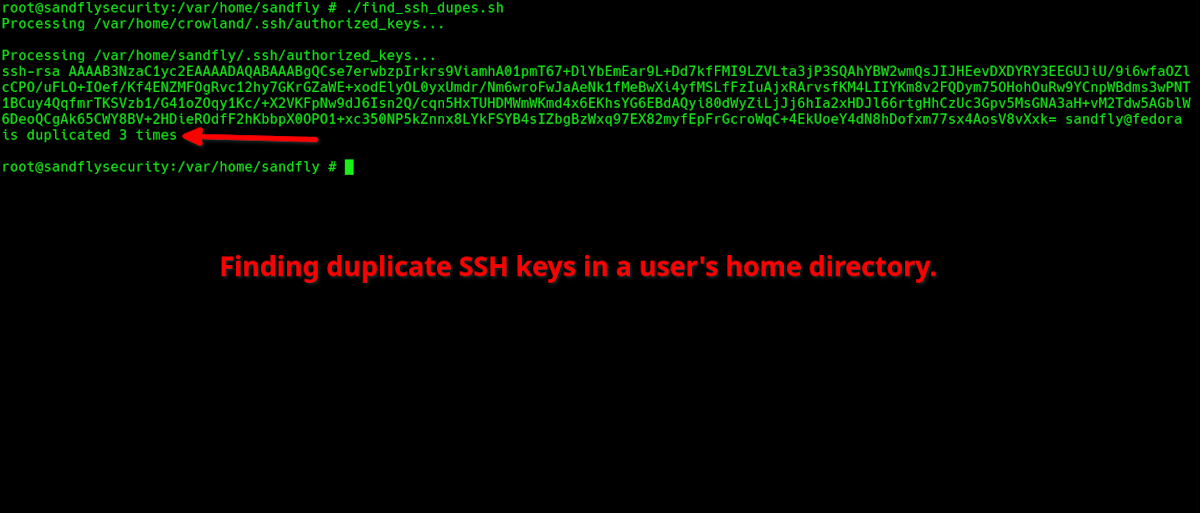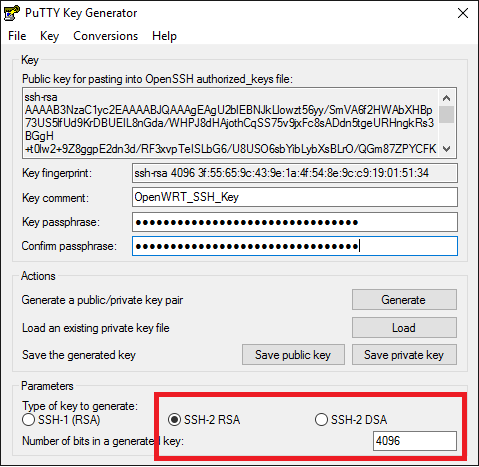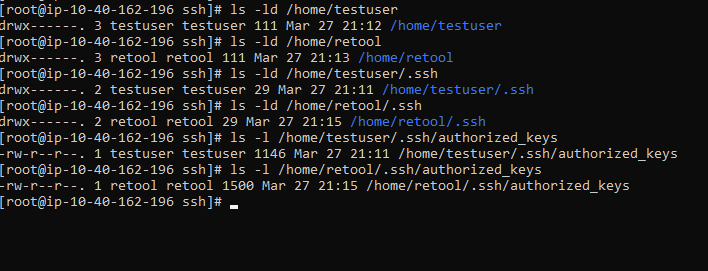
SSH Tunneling error - "All configured authentication methods failed" - Queries and Resources - Retool Forum
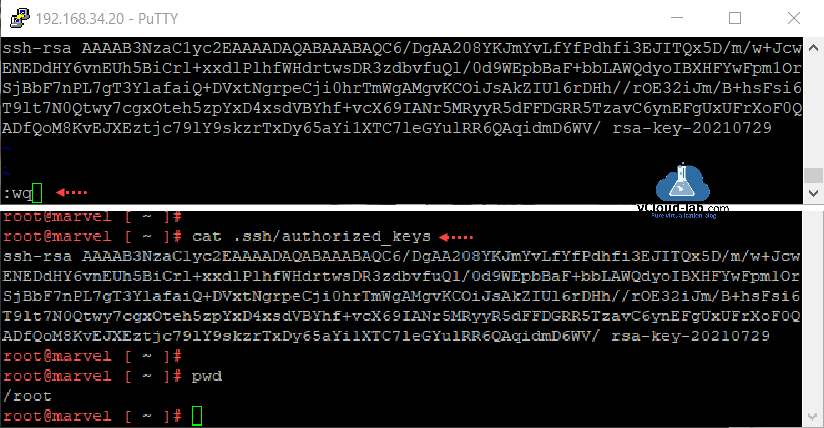
vCenter Server Public Key Authentication configuration SSH error received disconnect Too many authentication failures | vGeek - Tales from real IT system Administration environment

amazon web services - How to replace /root/.ssh/authorized_keys with cloud-config on EC2? - Stack Overflow