
A related-key boomerang attack on AES-192. The bottom characteristic is... | Download Scientific Diagram

Characteristics for the related-key boomerang attack on 7-round Khazad... | Download Scientific Diagram
![PDF] Related-Key Boomerang and Rectangle Attacks: Theory and Experimental Analysis | Semantic Scholar PDF] Related-Key Boomerang and Rectangle Attacks: Theory and Experimental Analysis | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/de00a00da3482fbc250364868d2cbd268ed3bb84/5-Figure1-1.png)
PDF] Related-Key Boomerang and Rectangle Attacks: Theory and Experimental Analysis | Semantic Scholar

PPT - The related key attack on the full GOST 28147-89 block cipher with four or two related keys PowerPoint Presentation - ID:2480300

Generalized related-key rectangle attacks on block ciphers with linear key schedule: applications to SKINNY and GIFT | Designs, Codes and Cryptography


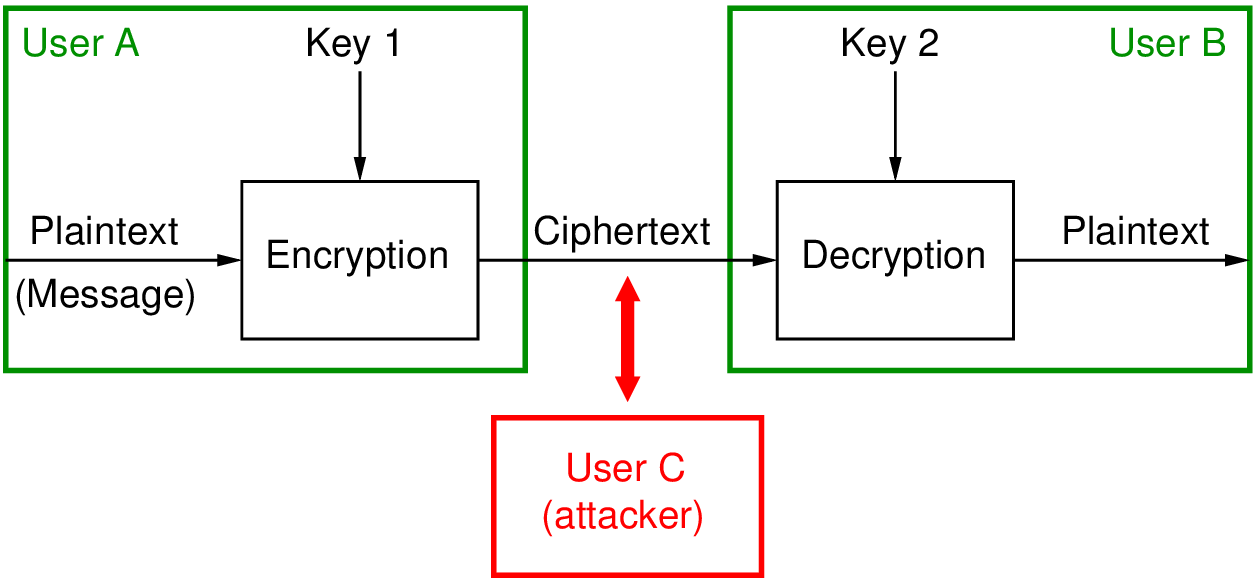

![PDF] A quantum related-key attack based on Bernstein-Vazirani algorithm | Semantic Scholar PDF] A quantum related-key attack based on Bernstein-Vazirani algorithm | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/fc16e68ed2840255ecad5c758d77b65e90967023/4-Figure1-1.png)
![PDF] A chosen key attack against the secret S-boxes of GOST | Semantic Scholar PDF] A chosen key attack against the secret S-boxes of GOST | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6576224b8438e79bafc85bfb7da561dfa12bc822/3-Figure1-1.png)


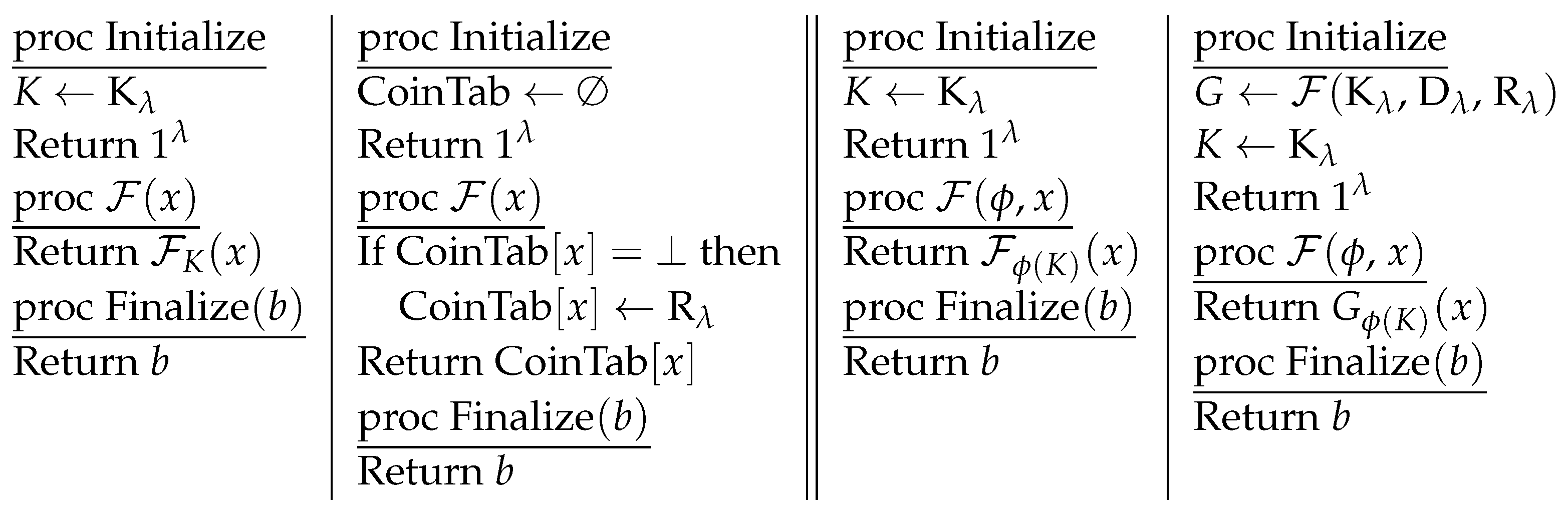
![PDF] Semantic Security under Related-Key Attacks and Applications | Semantic Scholar PDF] Semantic Security under Related-Key Attacks and Applications | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/03a055a84de8a2f58bac8ce7101fbfacb1cfb17c/15-Figure1-1.png)








