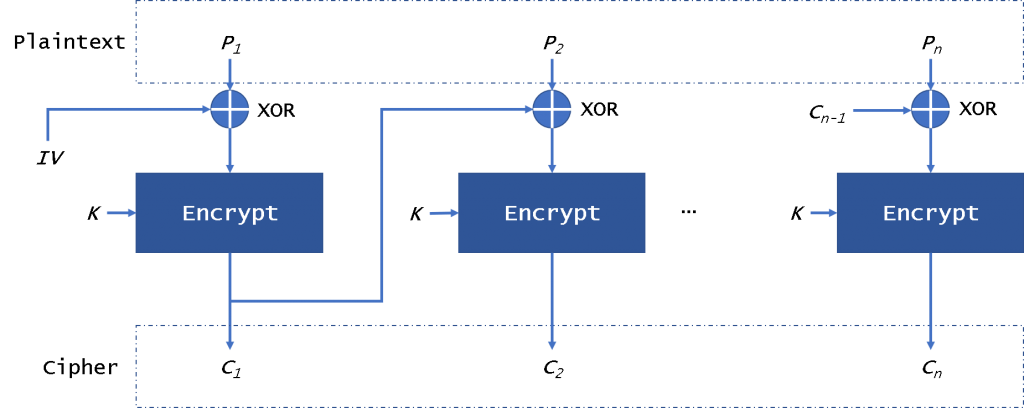
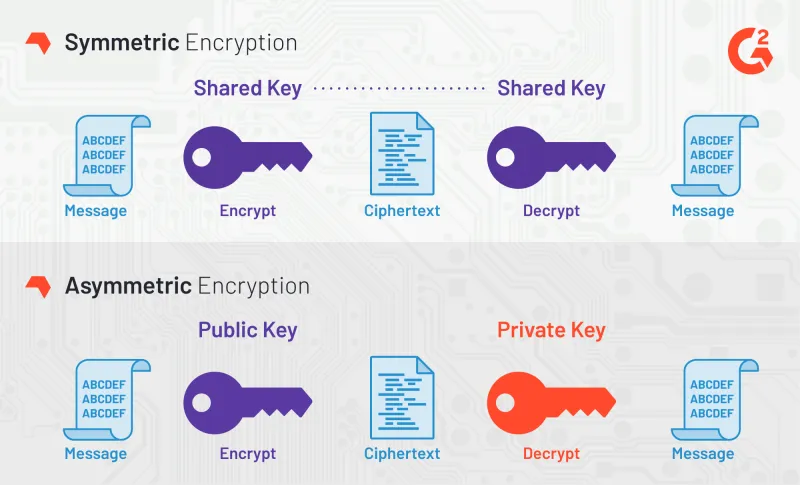
Representative binary bitmap of cryptographic keys Digitized security... | Download Scientific Diagram

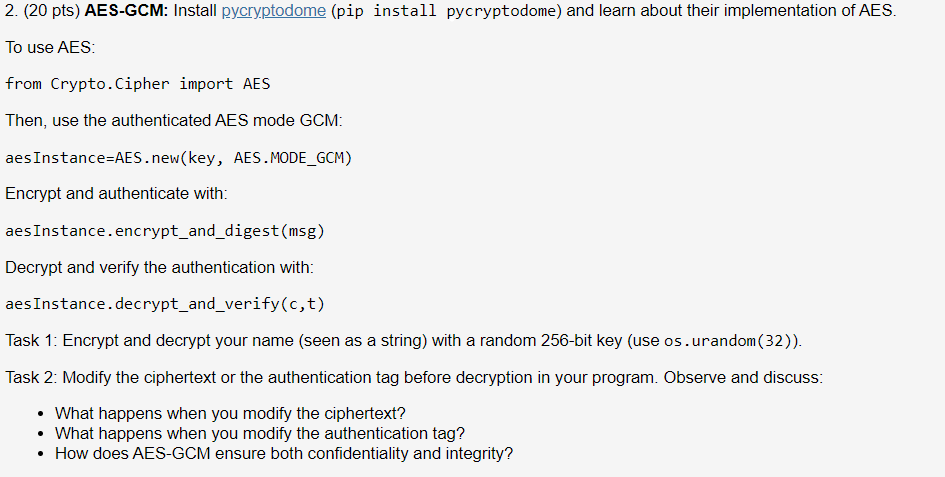
Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)

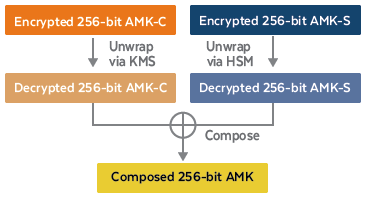
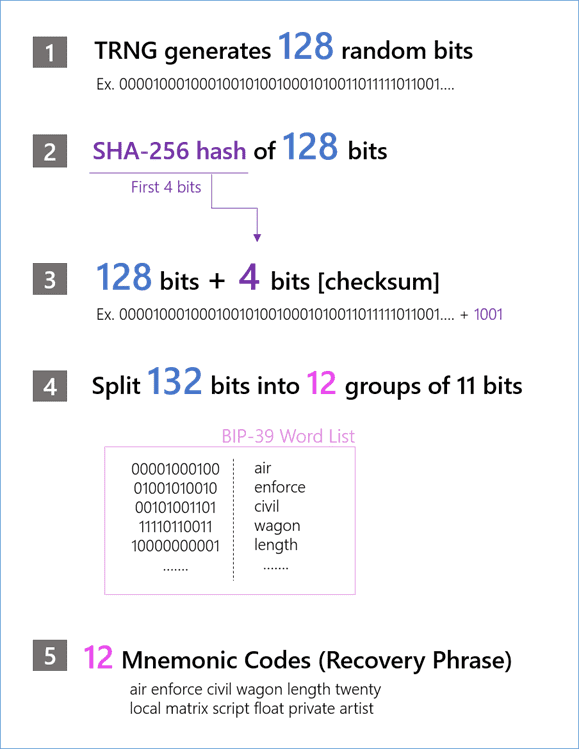
Stage 1 -A True Random Number Generation (TRNG) process can create a... | Download Scientific Diagram
Stage 2 -The 256 bit binary Master seed from which a vast amount of... | Download Scientific Diagram