Implementing Diffie-Hellman key exchange method on logical key hierarchy for secure broadcast transmission | Semantic Scholar

Enhanced Strict Binary Logical Key Hierarchy Algorithm for Secure Group Communication | SpringerLink

Enhanced Strict Binary Logical Key Hierarchy Algorithm for Secure Group Communication | SpringerLink

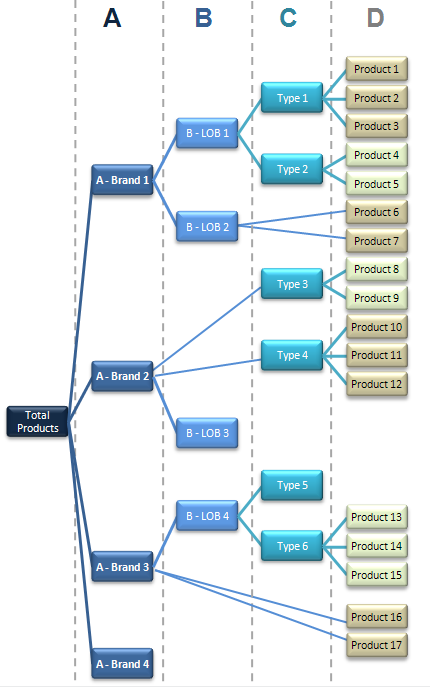
1: Logical Key Hierarchy For a join, a leaf node is added to the Key... | Download Scientific Diagram

Implementation Logical Key Hierarchy to a Nosql Database in Cloud Computing | Data Science and Applications