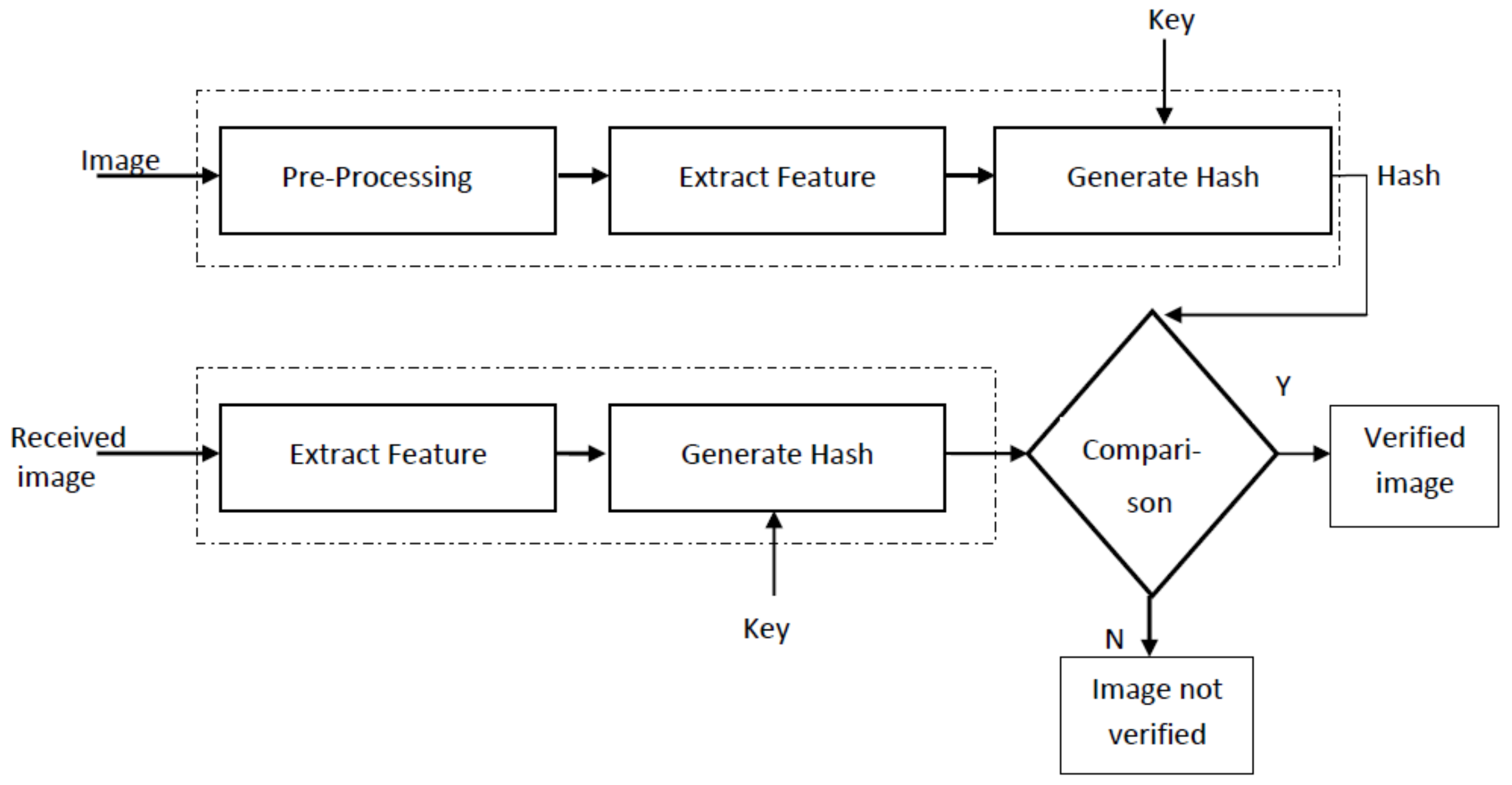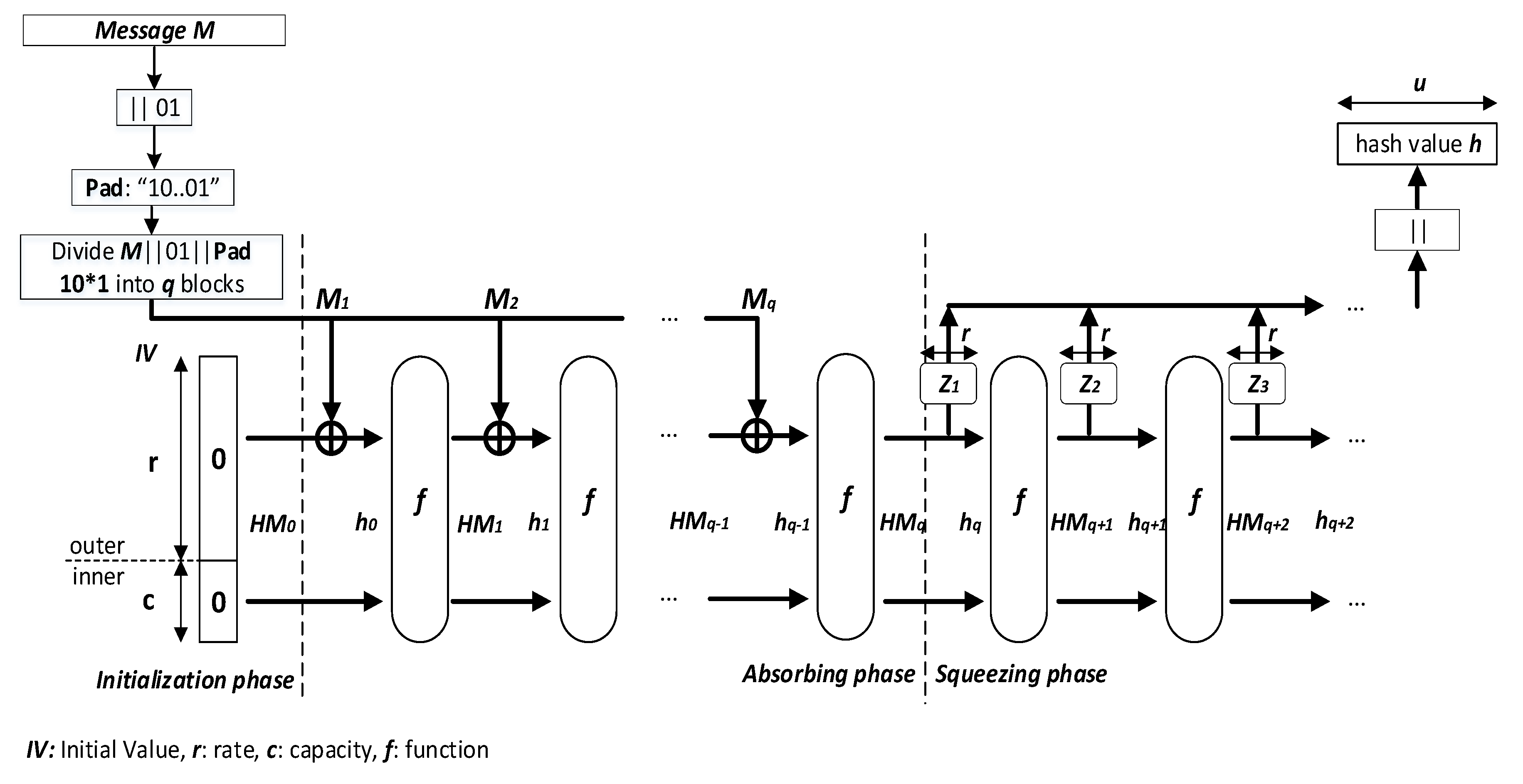
Entropy | Free Full-Text | Designing Two Secure Keyed Hash Functions Based on Sponge Construction and the Chaotic Neural Network

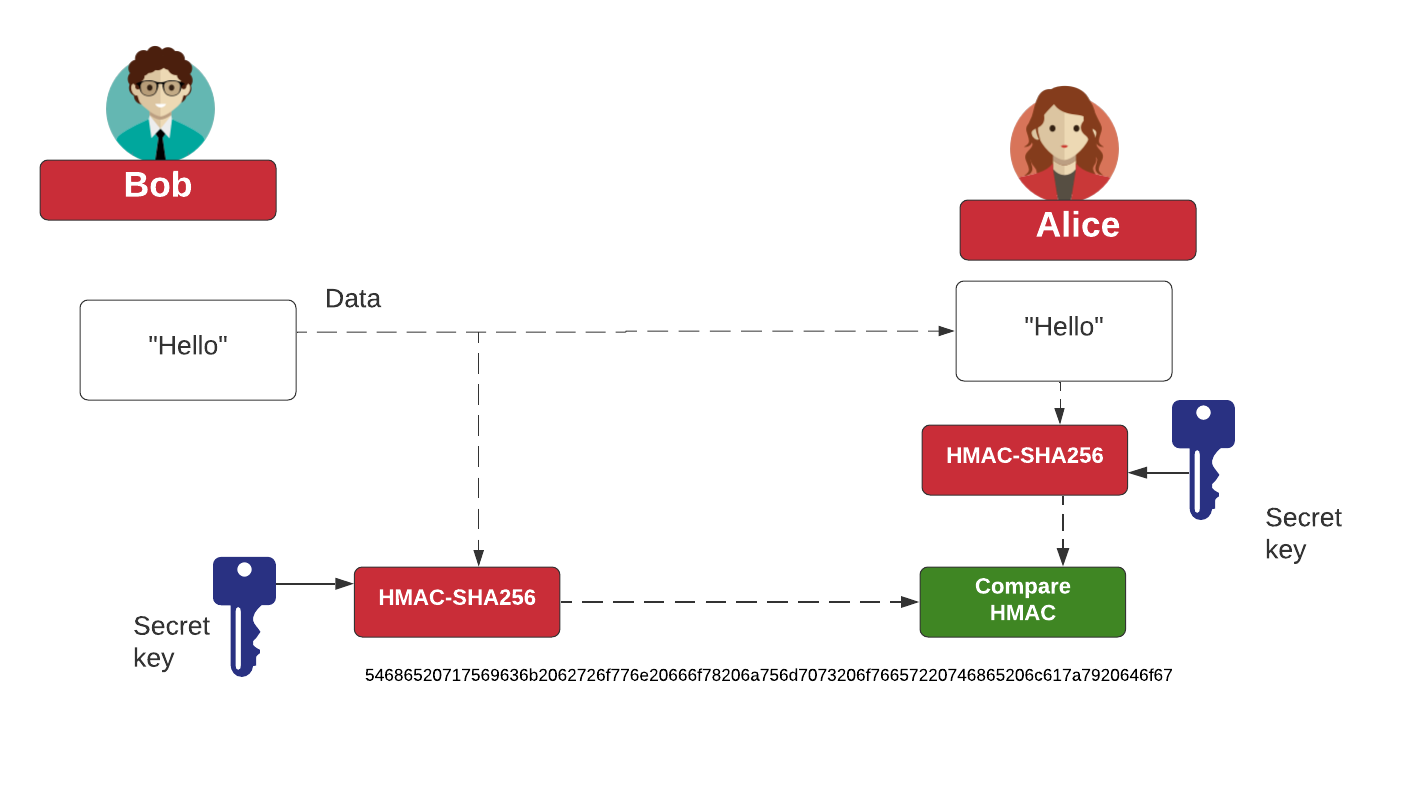
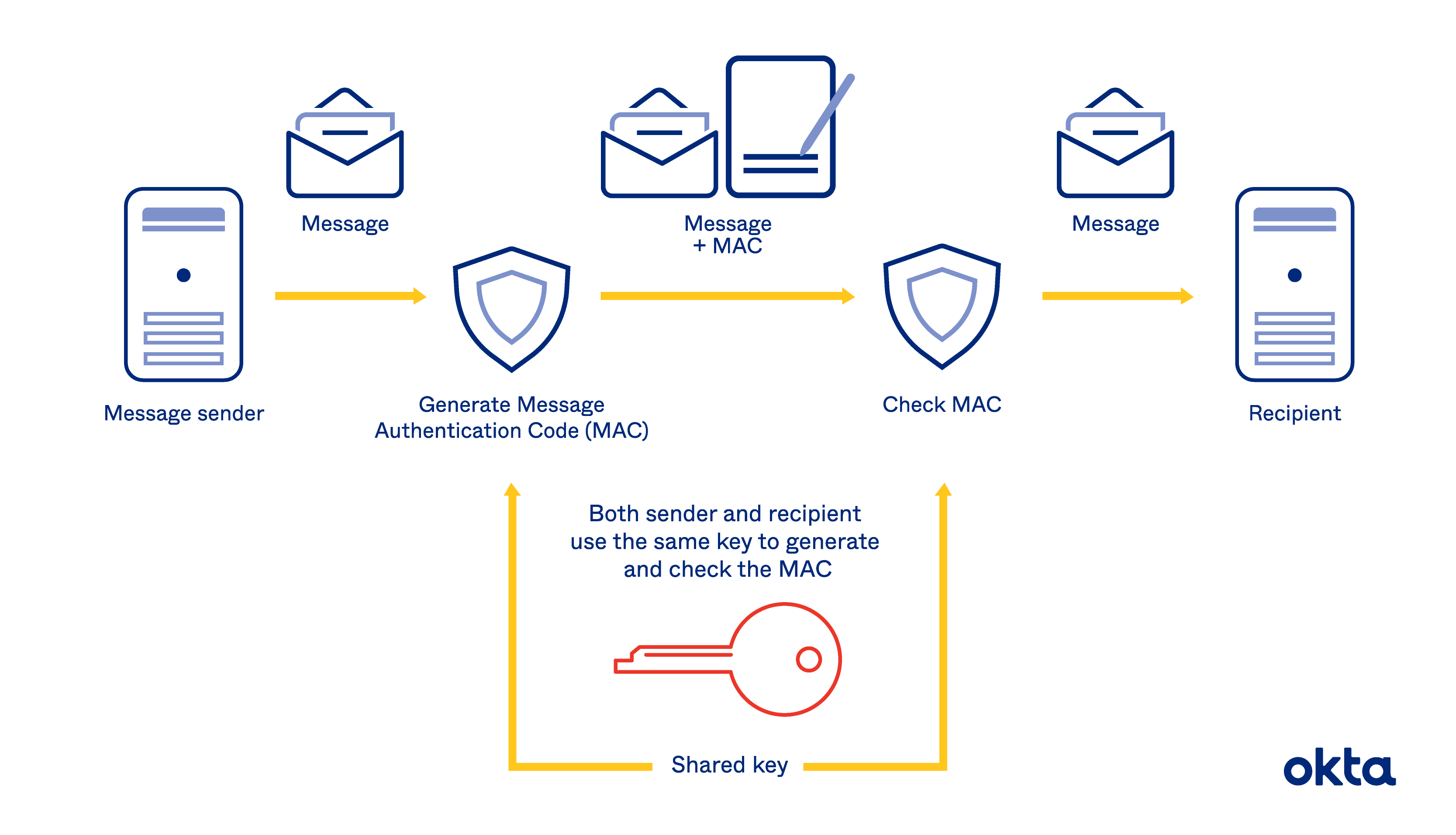
Fireship on X: "HMAC is a keyed hash - like a hash with a password. To create a HMAC you need to have the key, therefore allowing you to verify both the

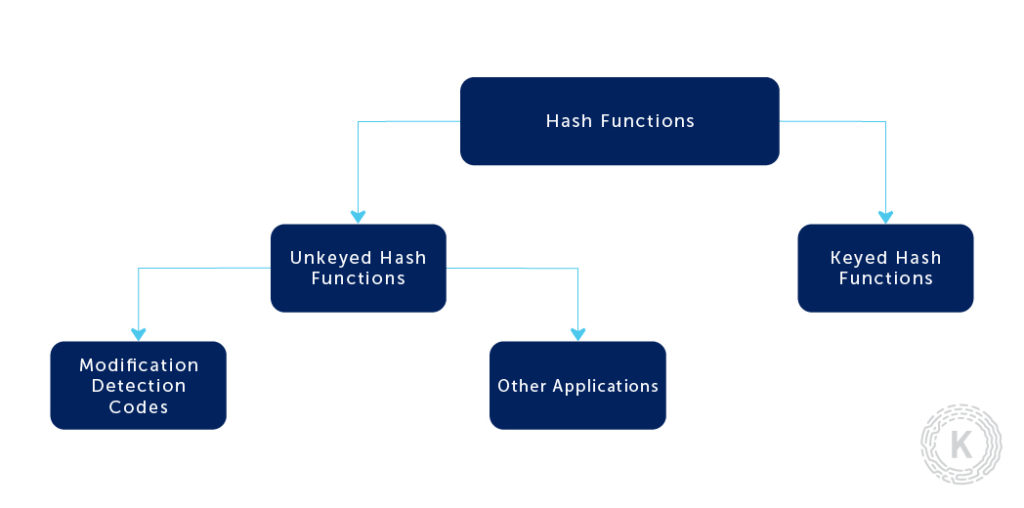
13.3 Keyed Hashing Algorithms Explained :: Chapter 13. Hashing Algorithms :: Part III: .NET Cryptography :: .NET Programming security :: Programming :: eTutorials.org