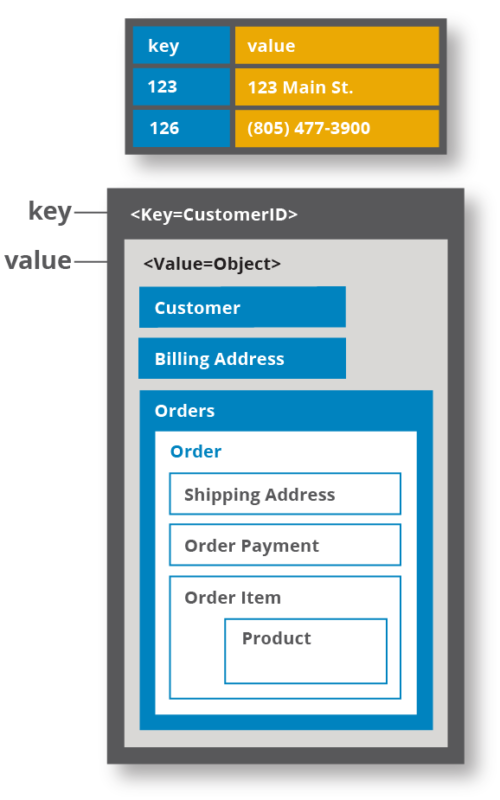
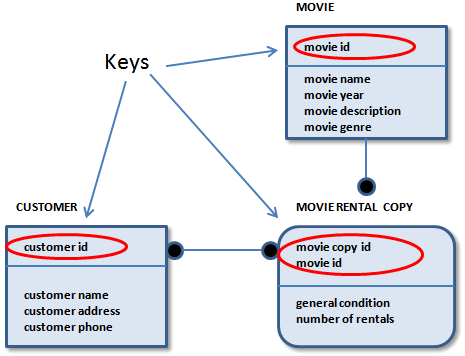
AWS Encryption SDK: How to Decide if Data Key Caching Is Right for Your Application | AWS Security Blog
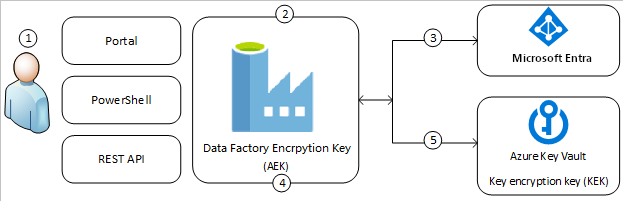
Verschlüsseln von Azure Data Factory mit vom Kunden verwalteten Schlüsseln - Azure Data Factory | Microsoft Learn

Wallpaper Illustration and background of cyber security data protection shield, with key lock security system, technology digital. Front view. Concept of database security software. Generative AI Stock-Illustration | Adobe Stock

Cyber security, computer data encryption and internet protection background with stream of binary data, code and digital key. Personal information safety, digital data secure access with password key Stock-Vektorgrafik | Adobe Stock