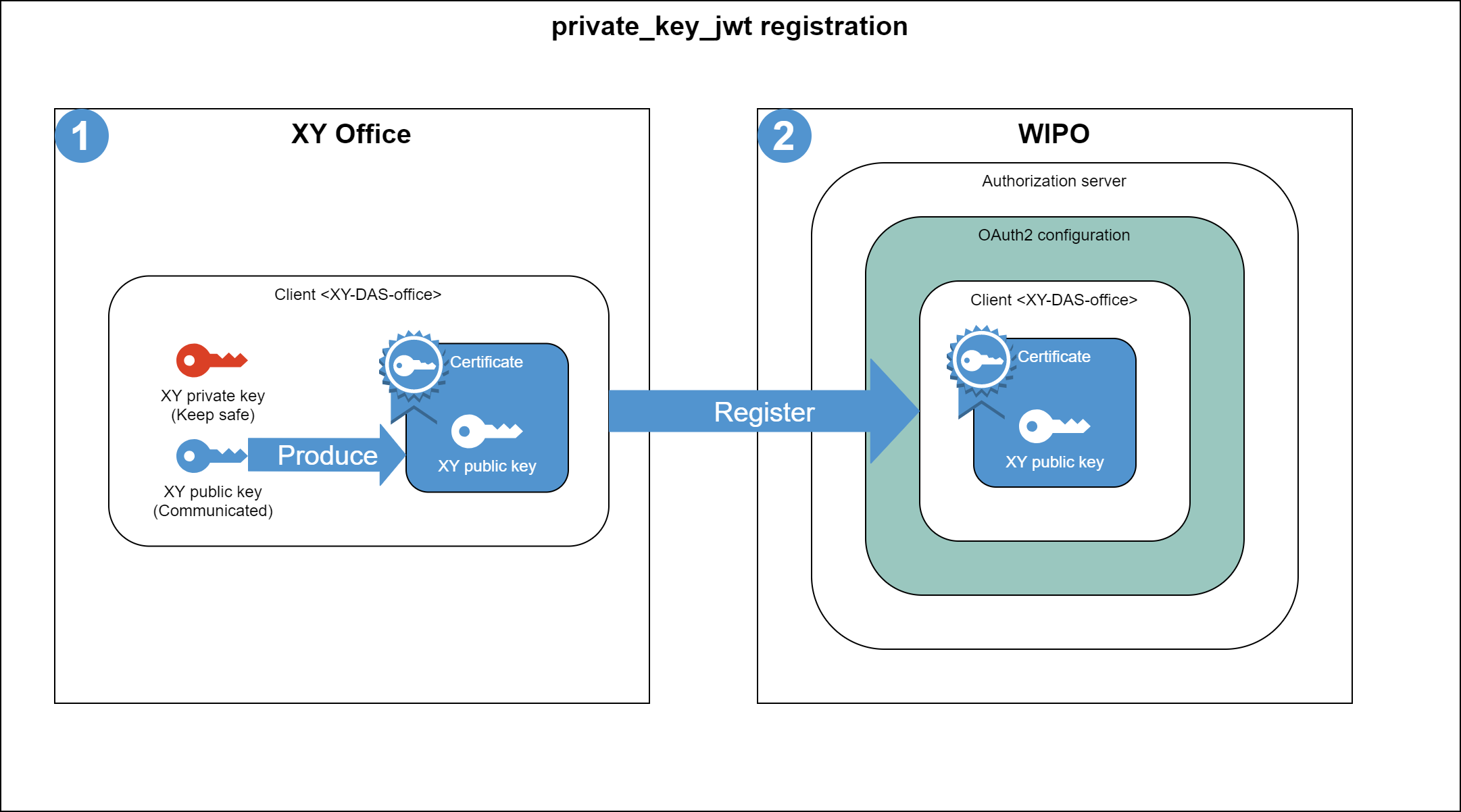
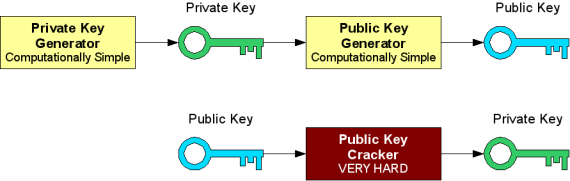
A tour of Verifiable Secret Sharing schemes and Distributed Key Generation protocols. | by Ignacio Manzur Tomasini | Nethermind.eth | Medium

Personal authentication and cryptographic key generation based on electroencephalographic signals - ScienceDirect
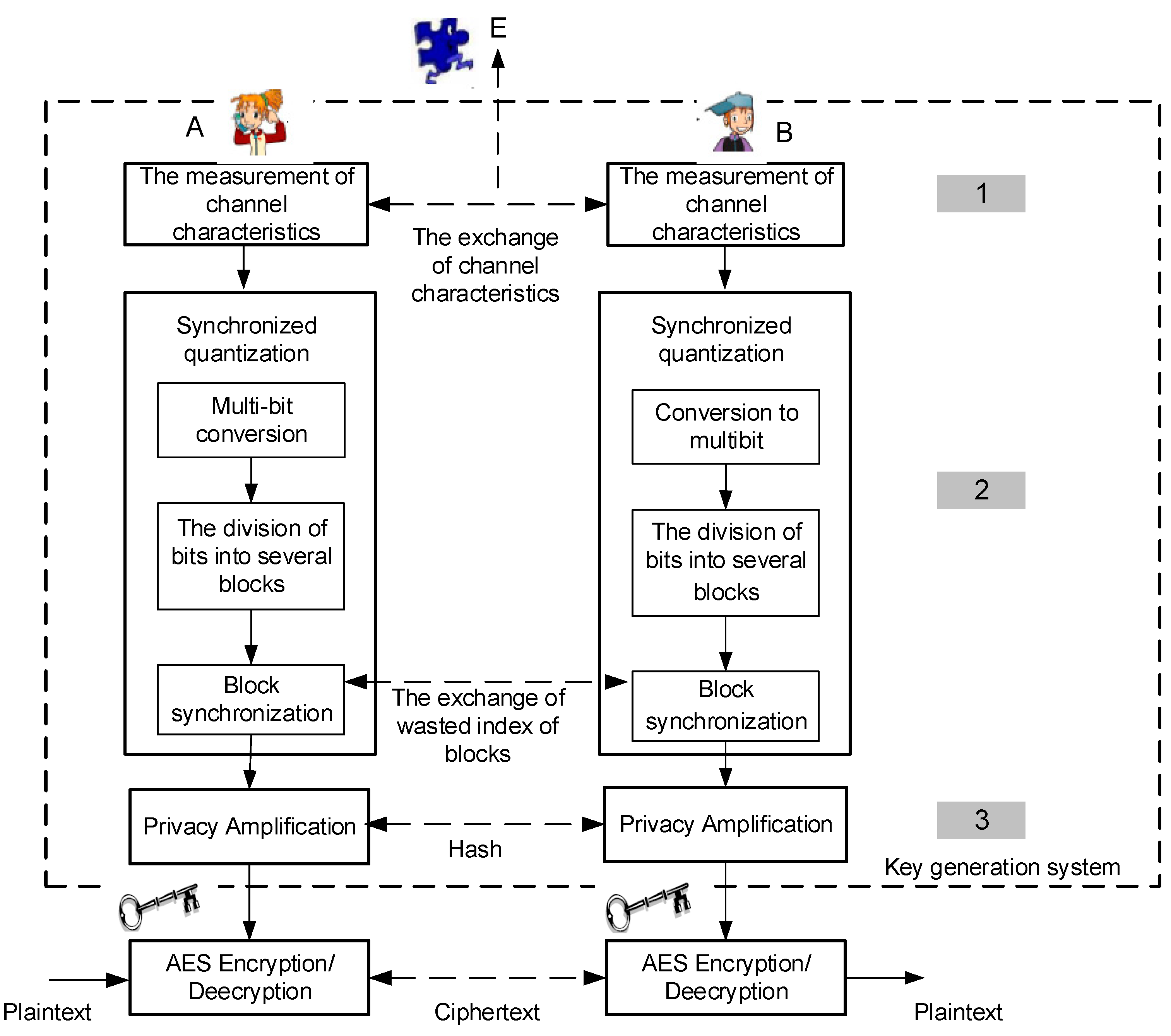
Sensors | Free Full-Text | An Efficient Key Generation for the Internet of Things Based Synchronized Quantization

Generation of Cryptographic Keys from Personal Biometrics: An Illustration Based on Fingerprints | IntechOpen

Applied Sciences | Free Full-Text | A Secure Biometric Key Generation Mechanism via Deep Learning and Its Application