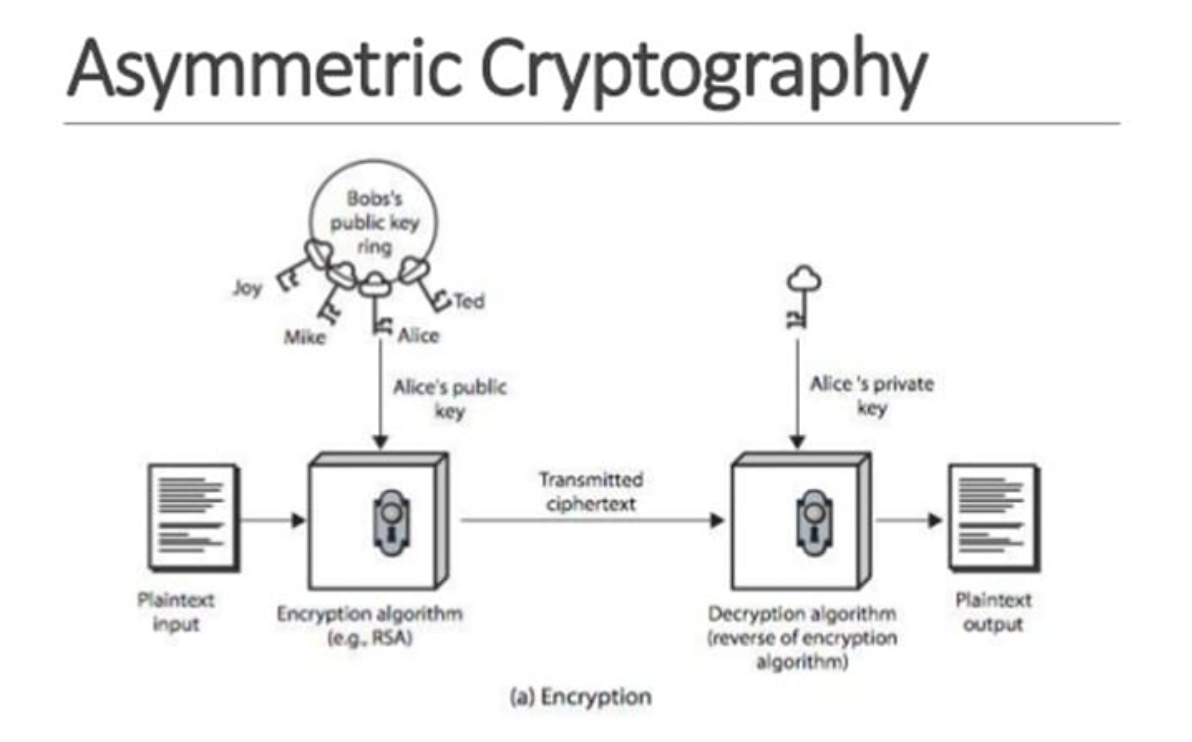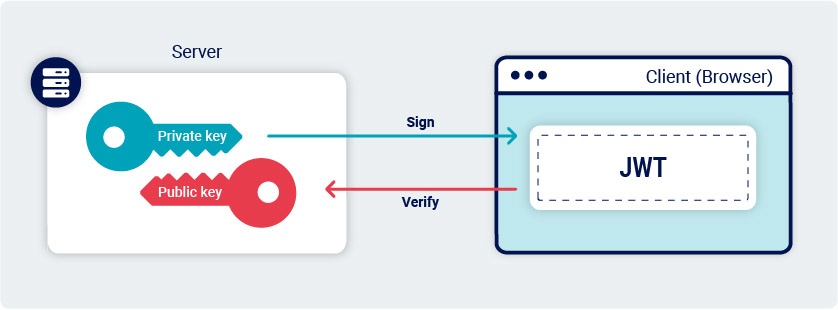
JSON Web Token (JWT): An Overview – Siddha Development Research and Consultancy (SDRC) – Enabling Social Change
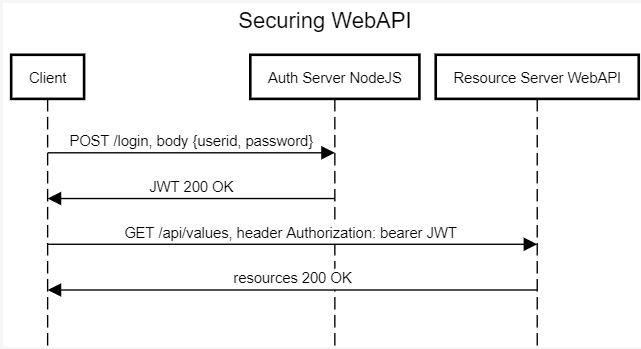
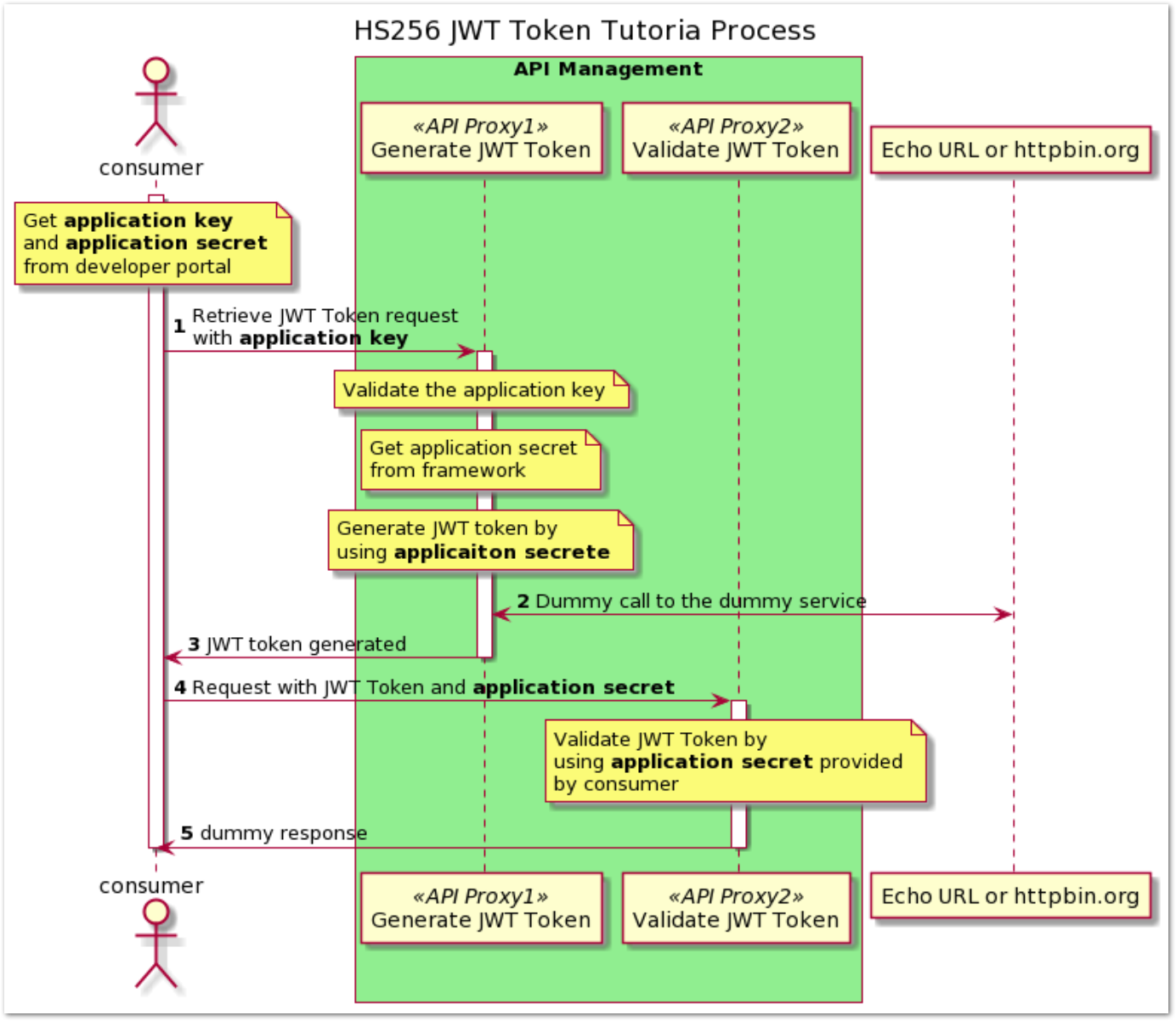
Istio & JWT: Step by Step Guide for Micro-Services AuthN and AuthZ | by Ferdous Shourove | Medium | intelligentmachines

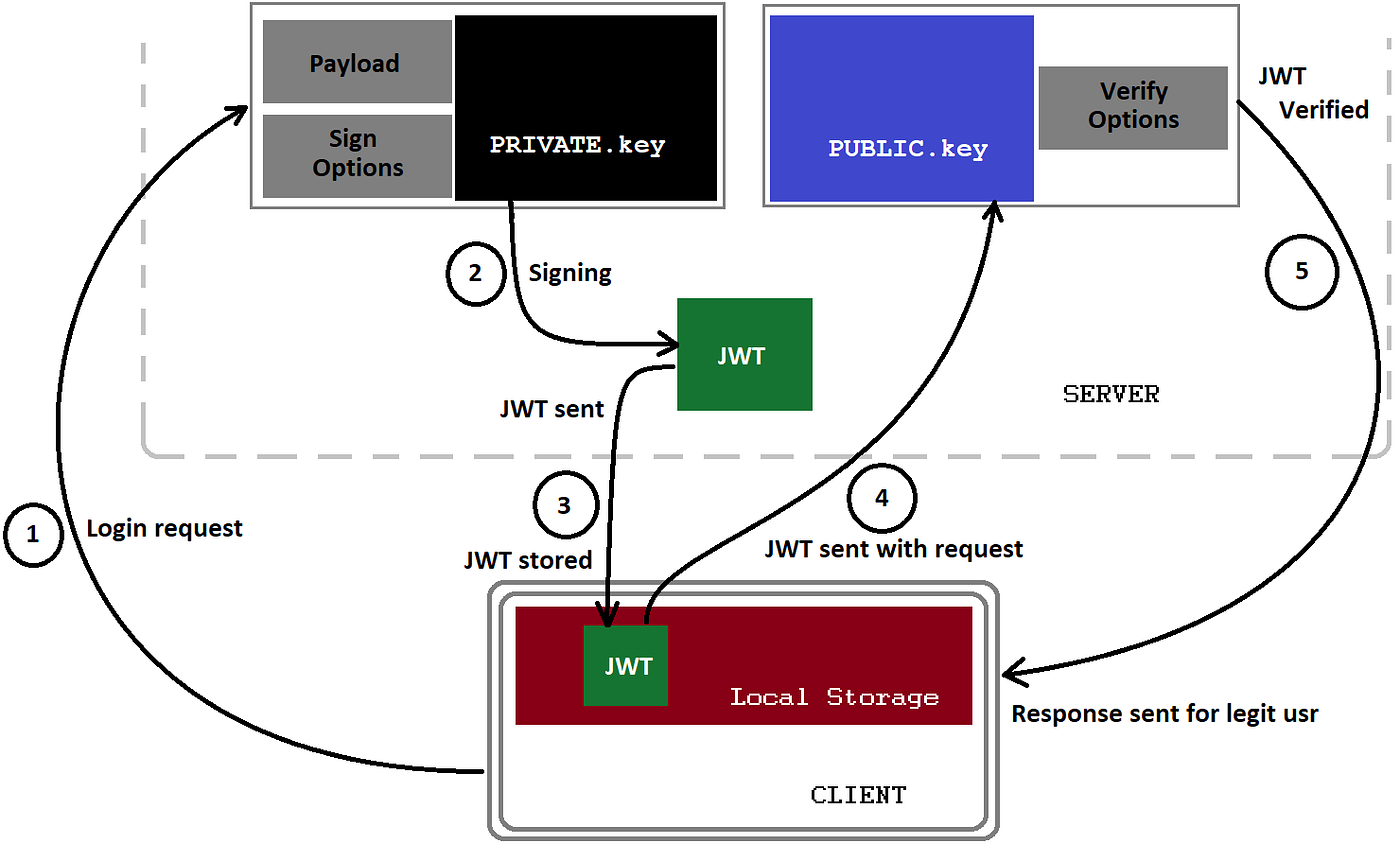
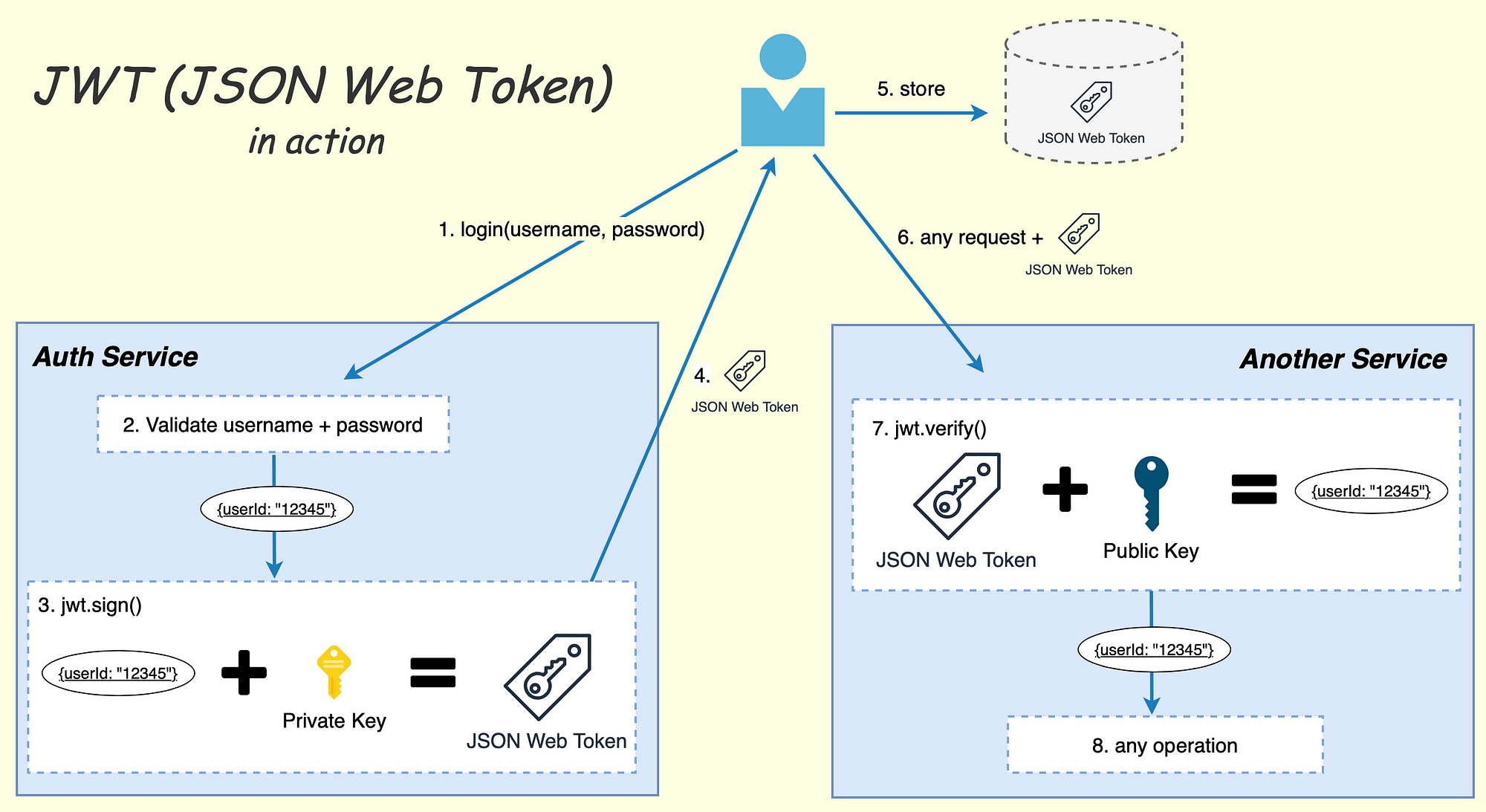
JSON Web Token (JWT) — The right way of implementing, with Node.js | by Siddhartha Chowdhury | Medium

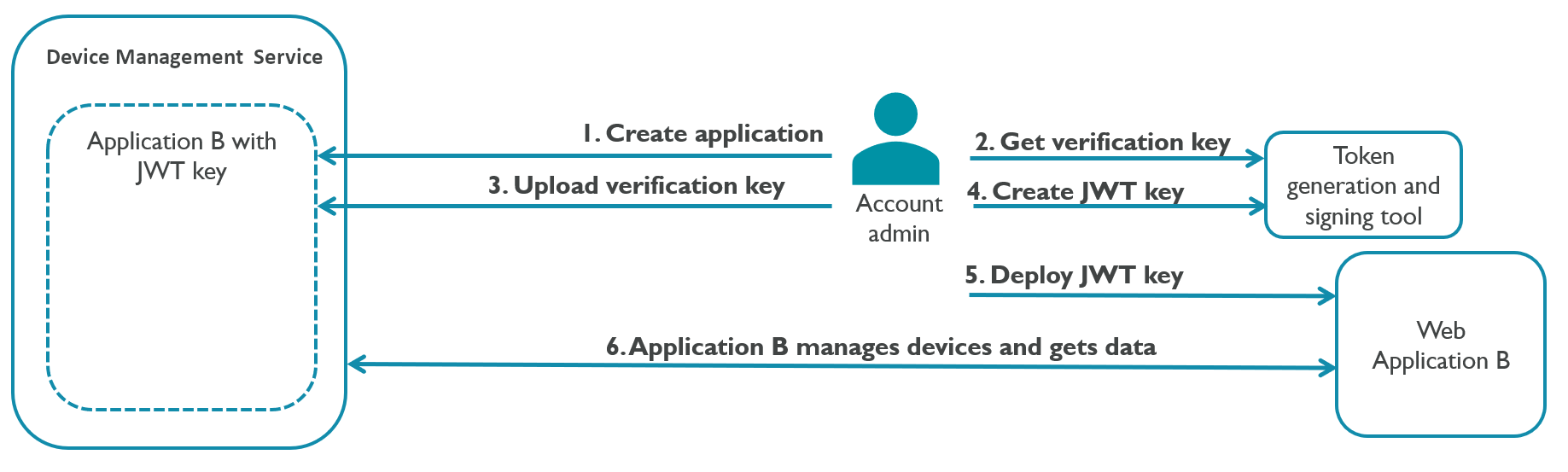
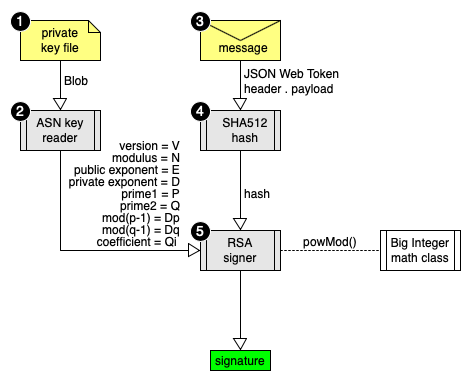
openid connect - What public key to use when verifying JWT.io signature OneLogin ID Token - Stack Overflow