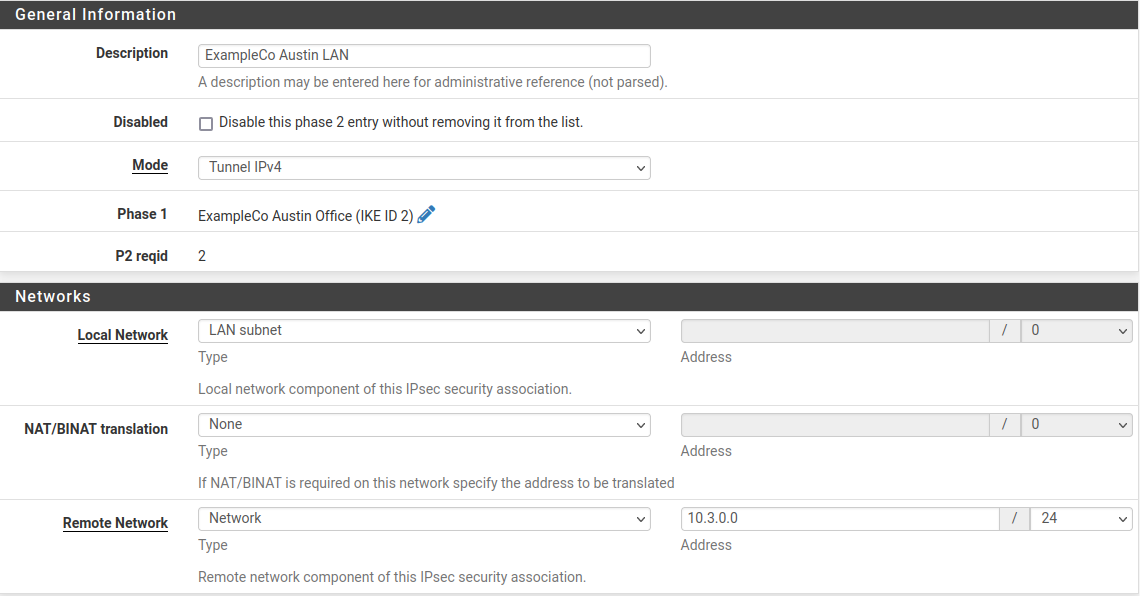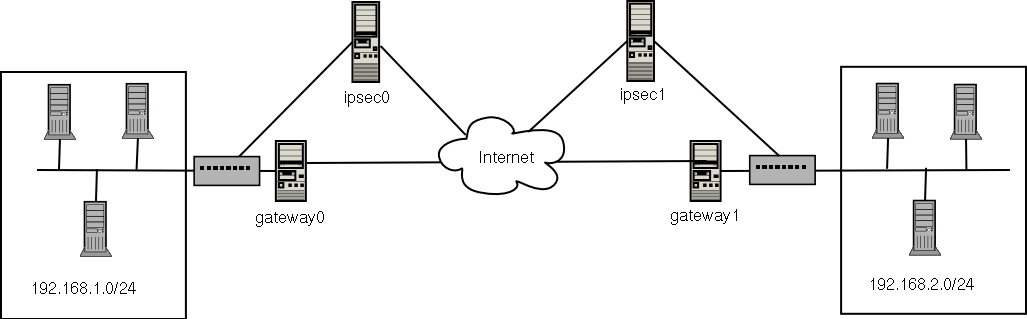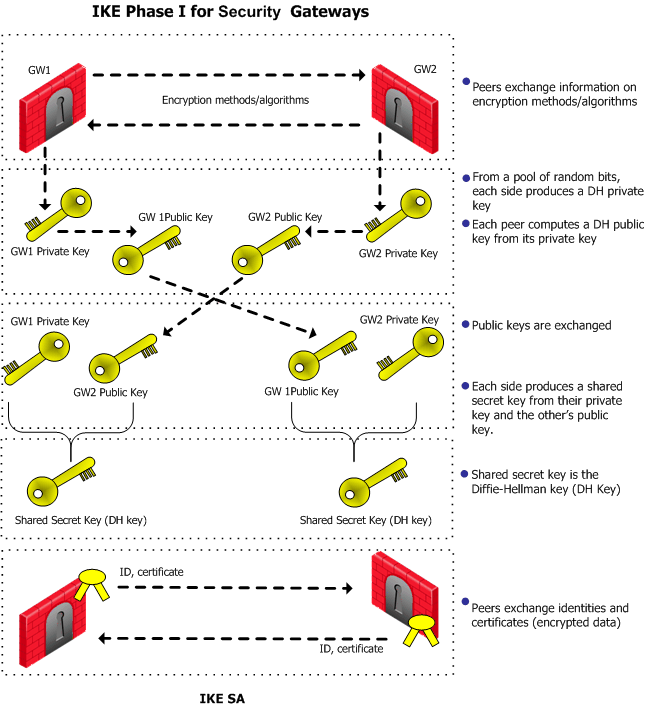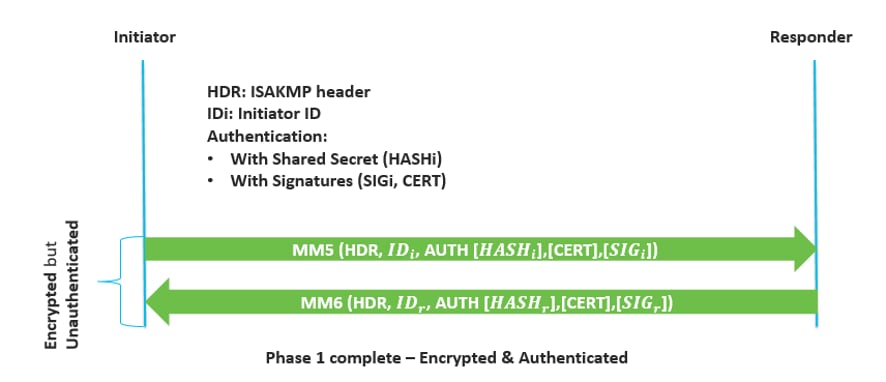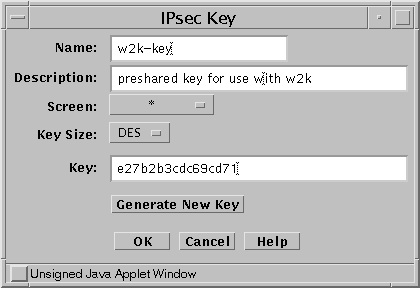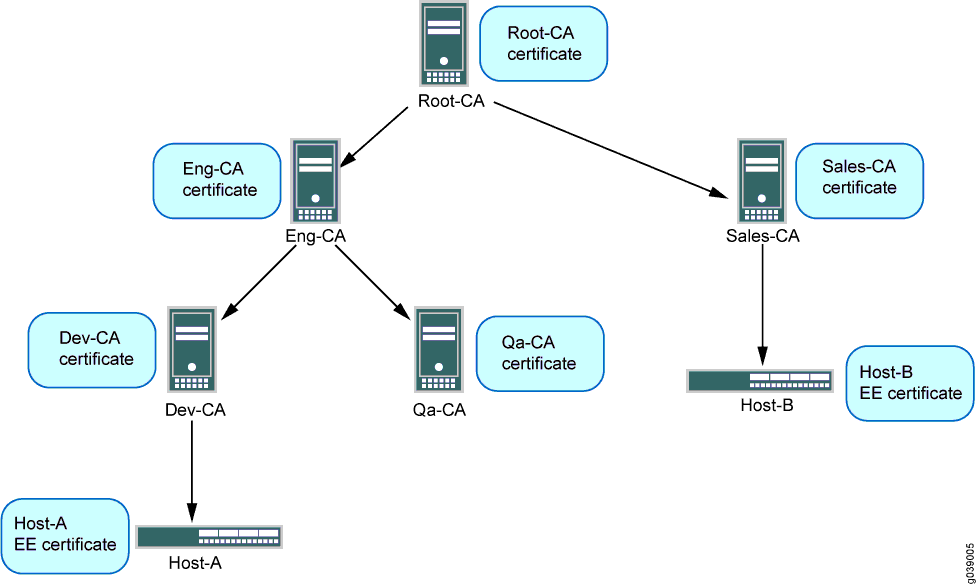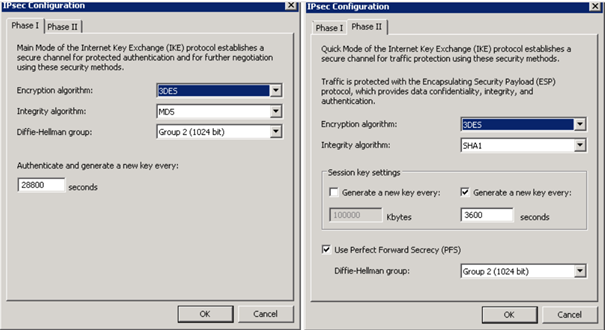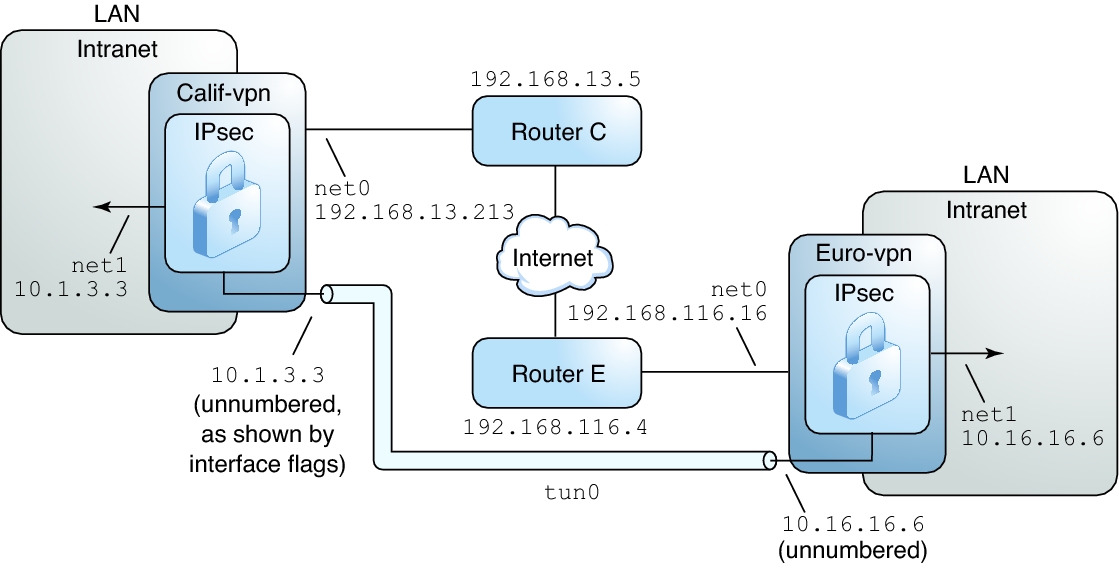
Description of the Network Topology for the IPsec Tasks to Protect a VPN - Securing the Network in Oracle® Solaris 11.2

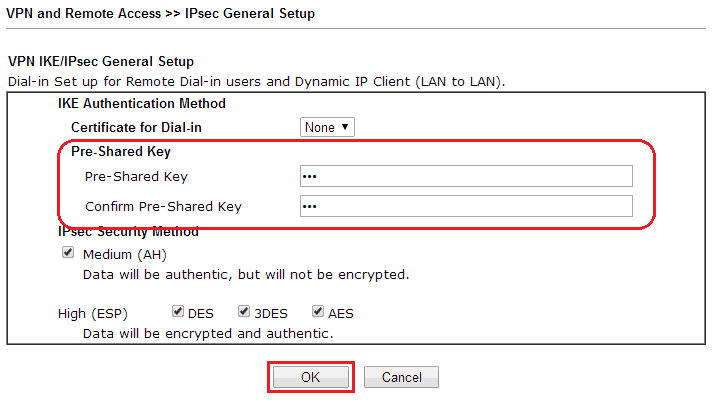
networking - Where to add the Pre-Shared Key for the Server Authentication with Network Manager for L2TP/IPSEC? - Ask Ubuntu

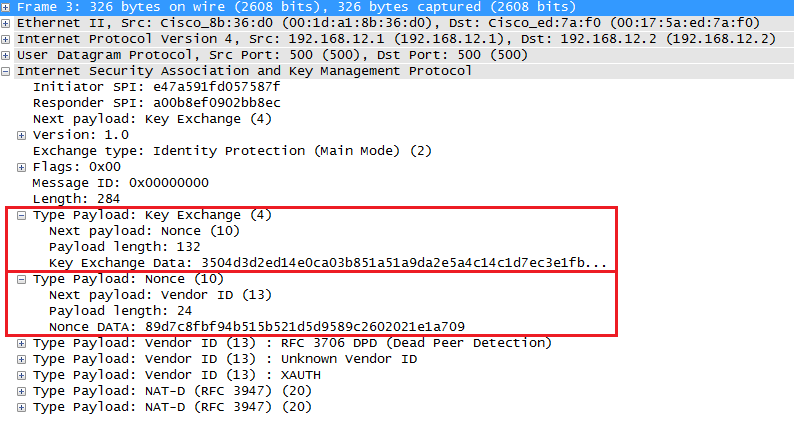
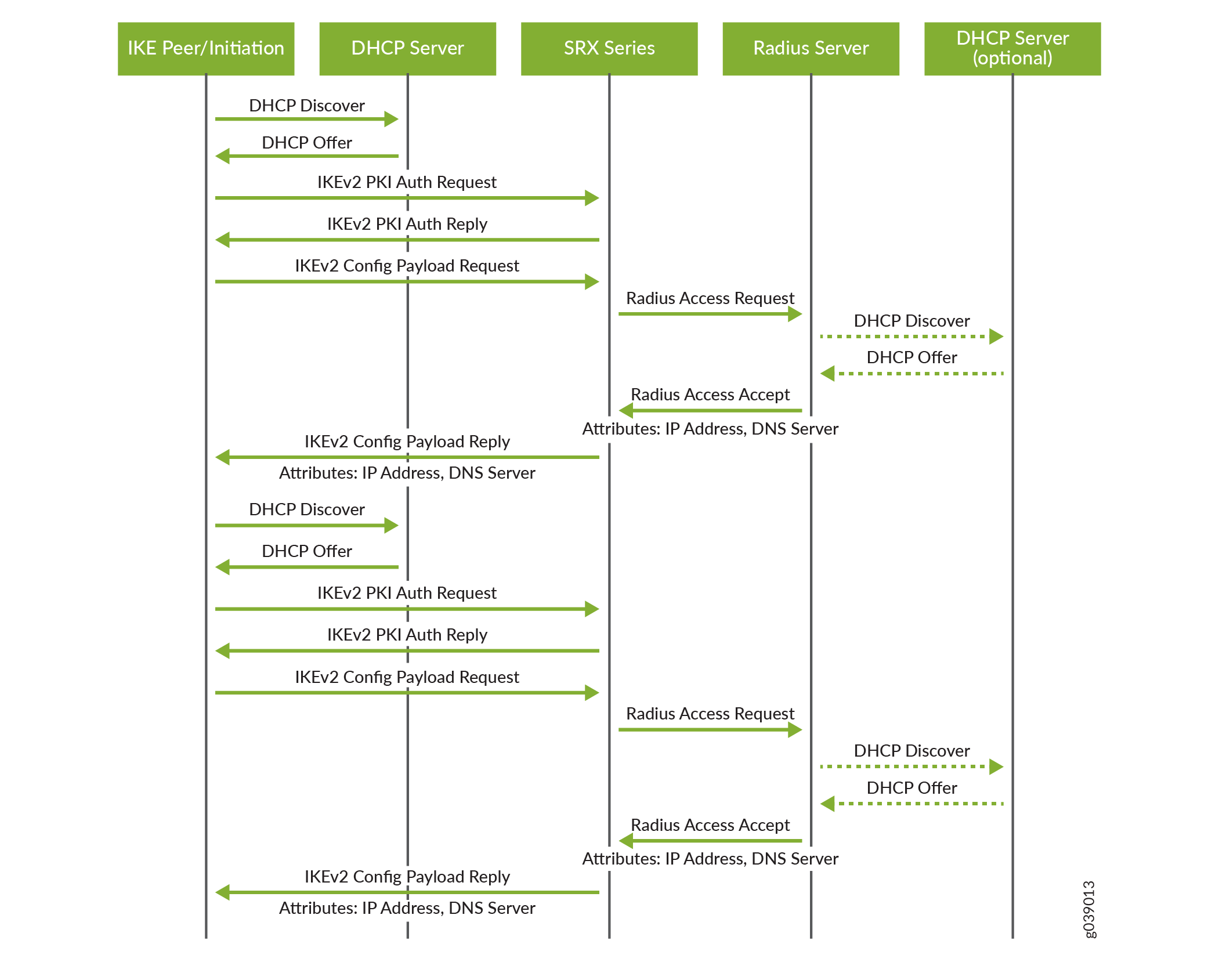
Regular IPSec session based on IKEv2. An encrypted message m is denoted... | Download Scientific Diagram
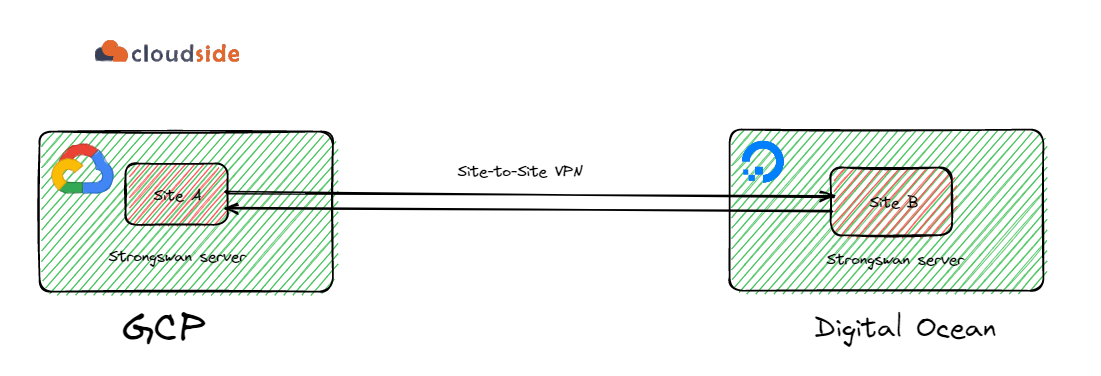
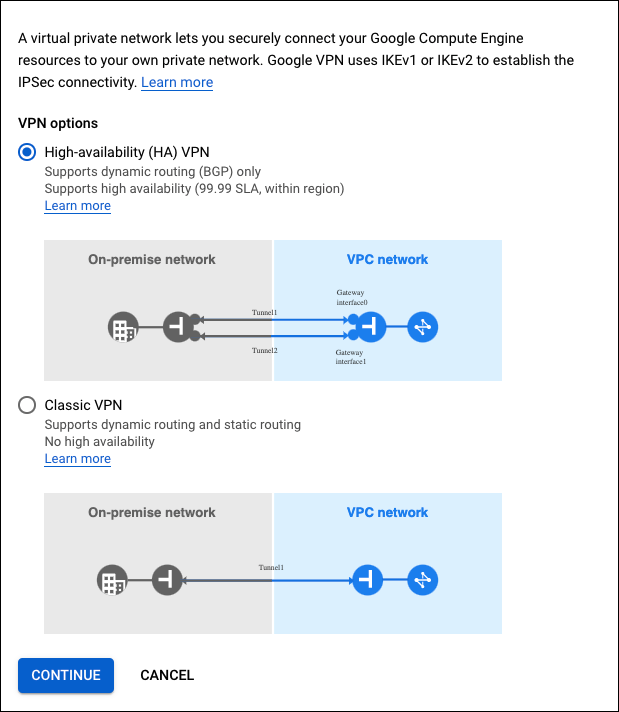
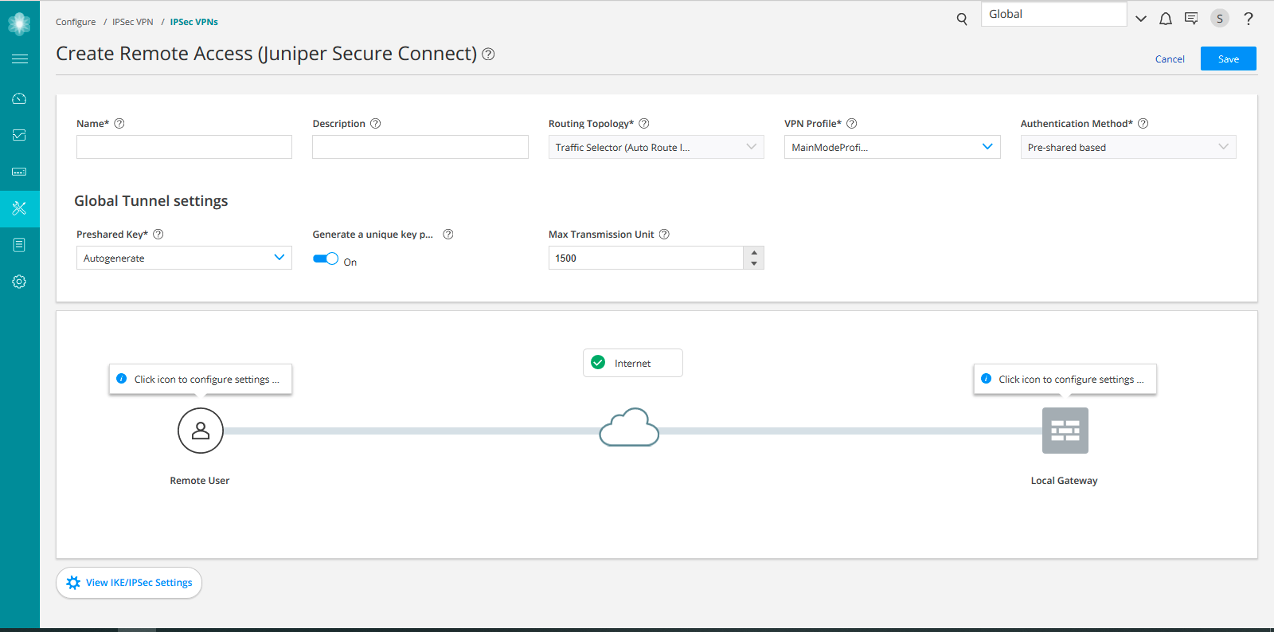
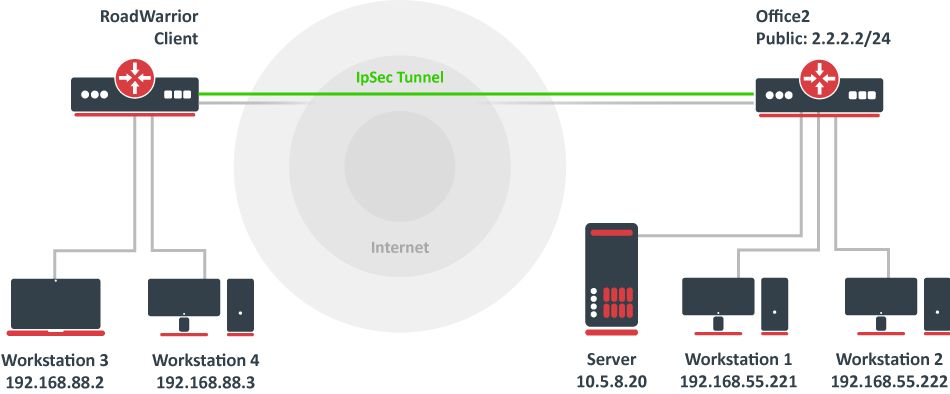
Using Strongswan to setup site to site IPsec VPN between GCP and Digital Ocean | by harsh | The Cloudside View