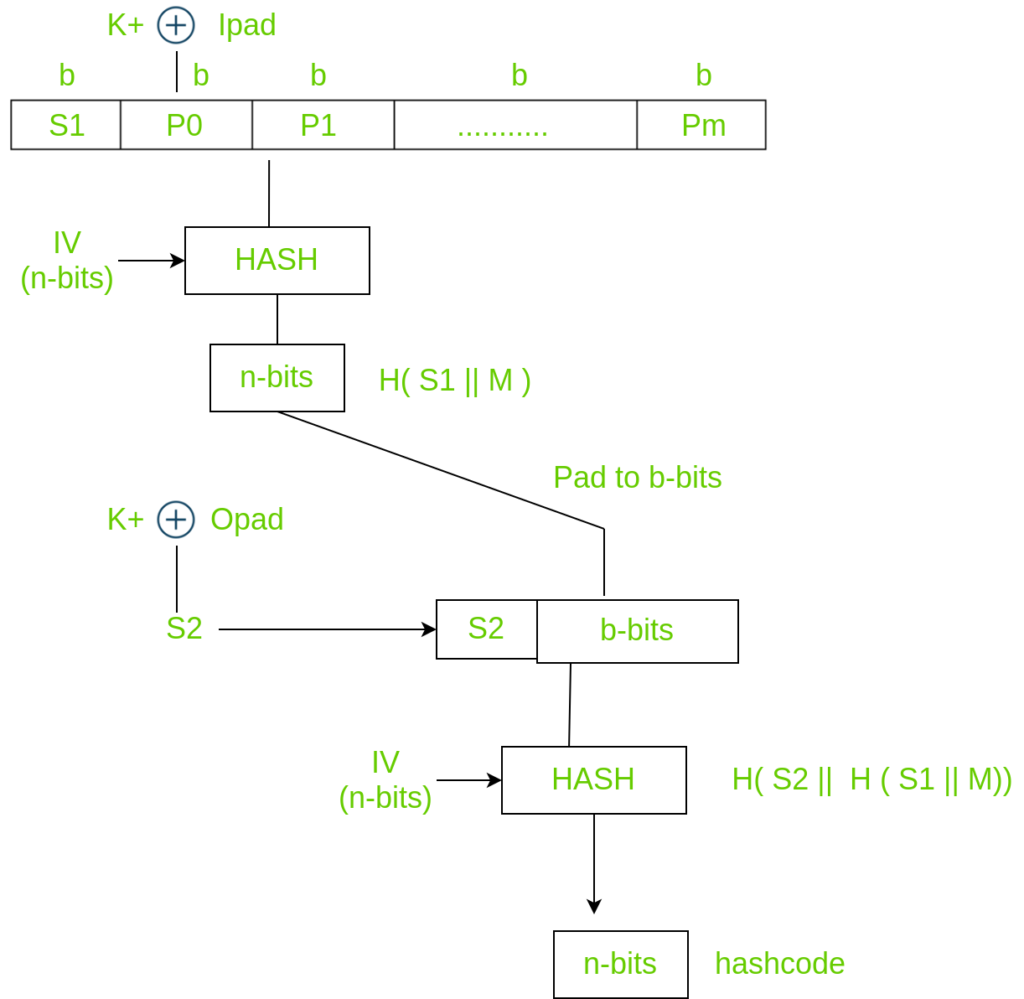
Sensors | Free Full-Text | Centralized Threshold Key Generation Protocol Based on Shamir Secret Sharing and HMAC Authentication

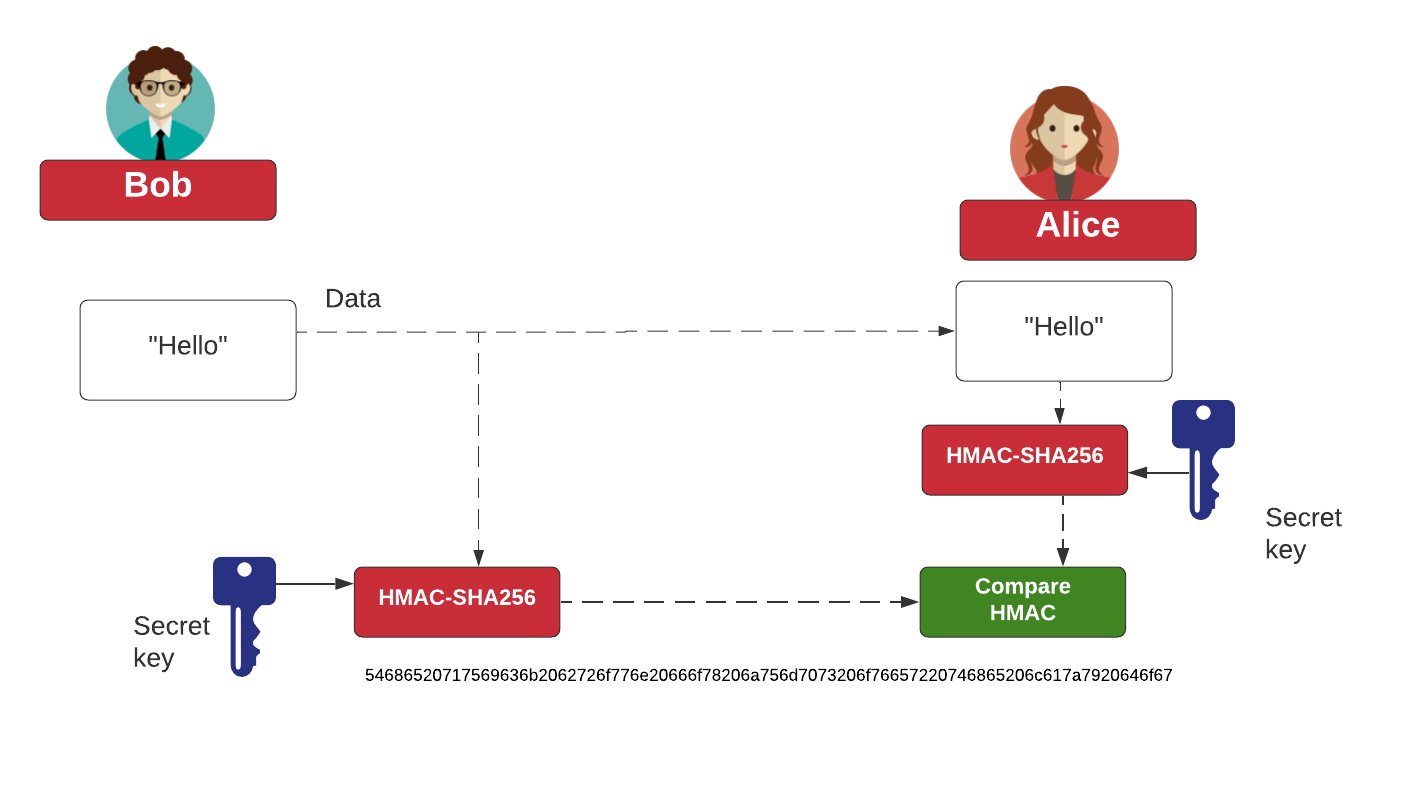
HMAC and HKDF. What's the right way to correct an… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

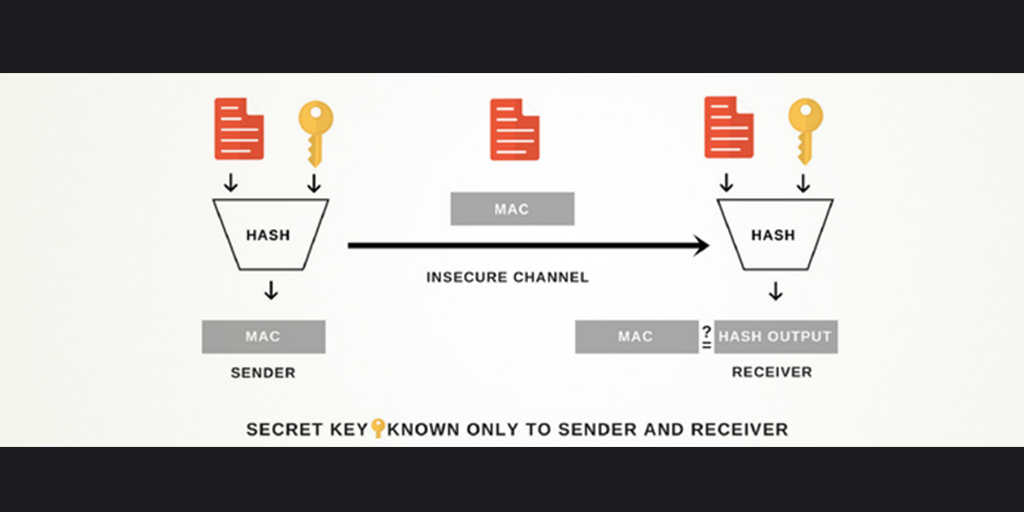
Overview of HMAC usage when sender and receiver rely on a message being... | Download Scientific Diagram

Alex Xu on X: "𝐇𝐌𝐀𝐂 𝐛𝐚𝐬𝐞𝐝 This mechanism generates a Message Authentication Code (signature) by using a hash function (SHA256 or MD5). Steps 1 and 2 - the server generates two keys,


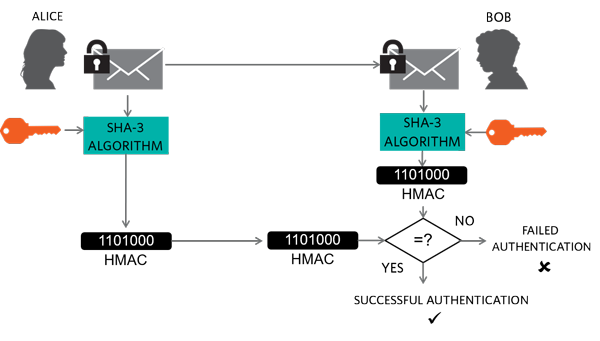






![7: HMAC-based Authentication Process [Ass07]. | Download Scientific Diagram 7: HMAC-based Authentication Process [Ass07]. | Download Scientific Diagram](https://www.researchgate.net/publication/301879544/figure/fig4/AS:359824912076805@1462800352140/HMAC-based-Authentication-Process-Ass07.png)