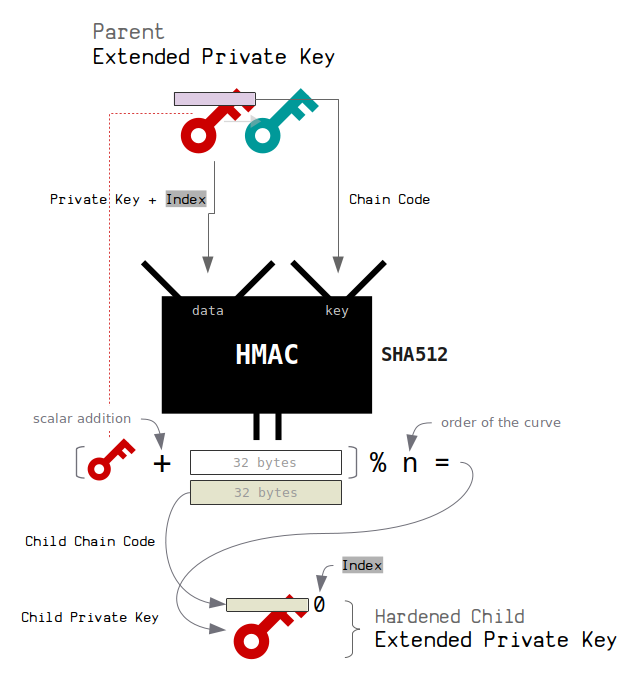
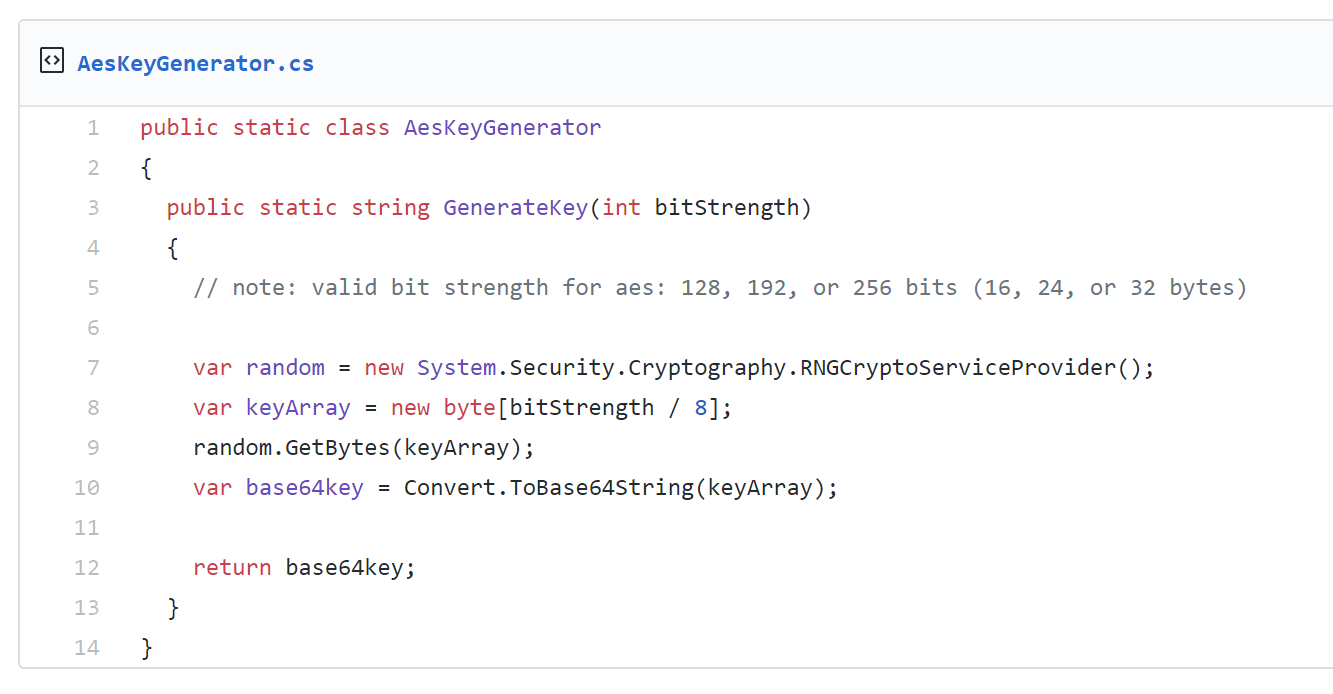
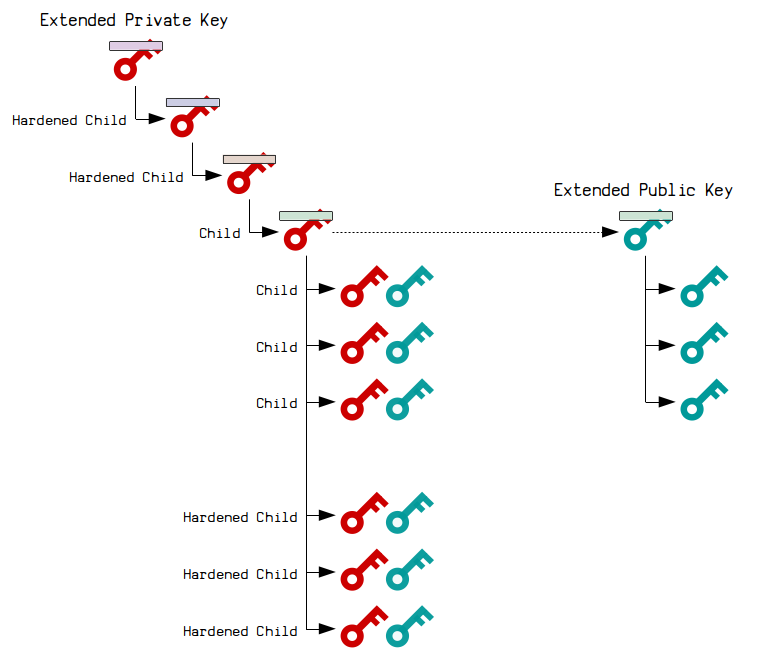
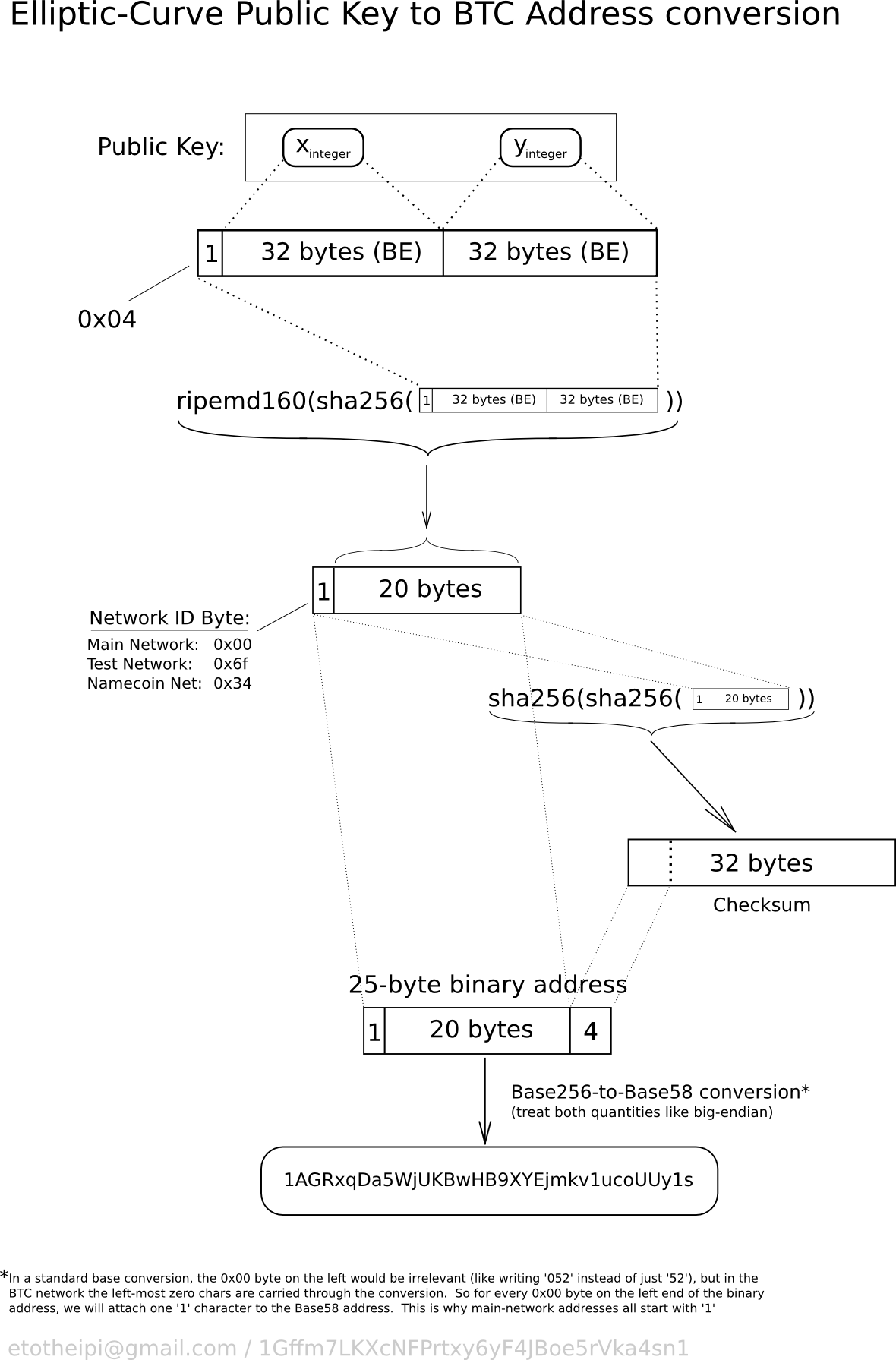
A Novice Mistake: Meet Milk Sad … And The 32-bit Key!!!!!! | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

Gary Clarke on X: "Generate a 256 bit secret, encoded in base 64 openssl rand -base64 32 I used this to generate a secret key to sign my JWT. Learn more about

A Novice Mistake: Meet Milk Sad … And The 32-bit Key!!!!!! | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

LightWeight energy-efficient Block Cipher based on DNA cryptography to secure data in internet of medical things devices | International Journal of Information Technology