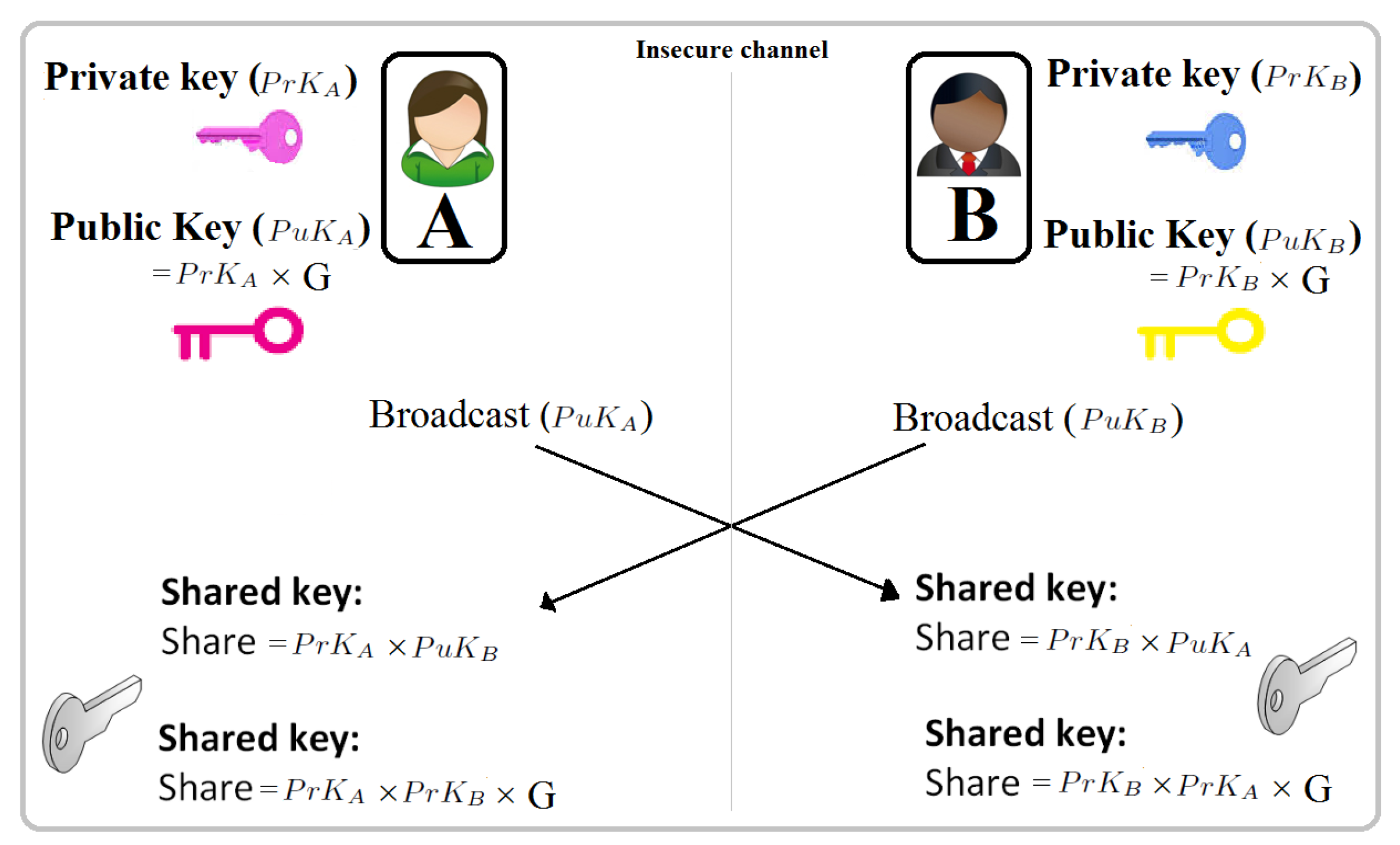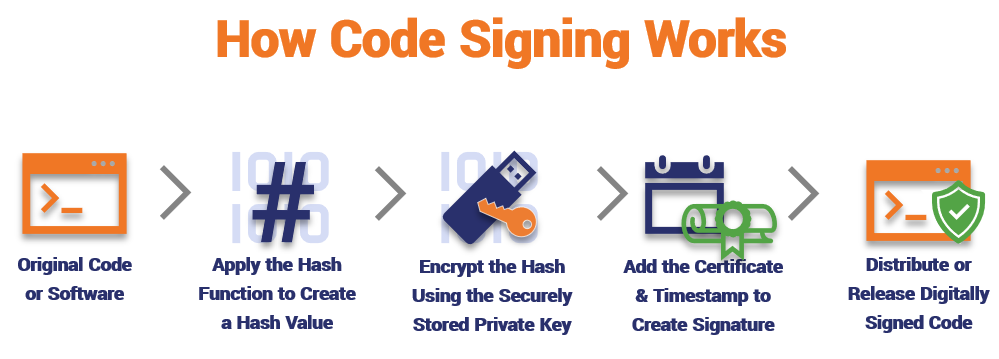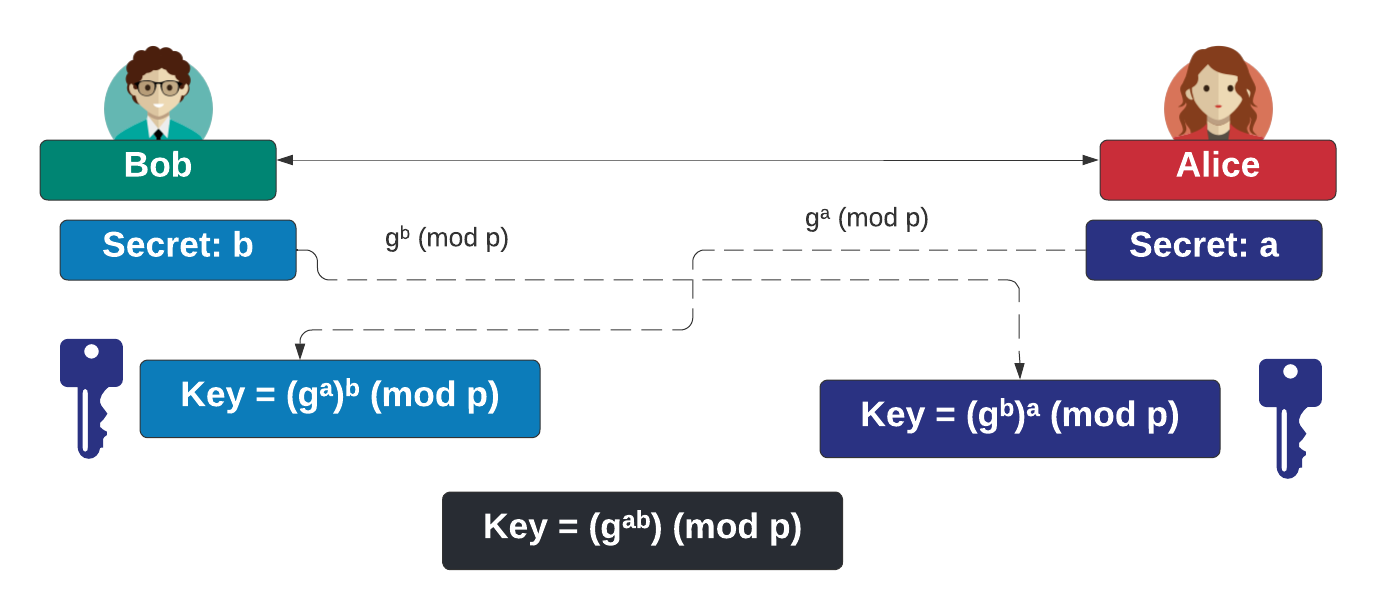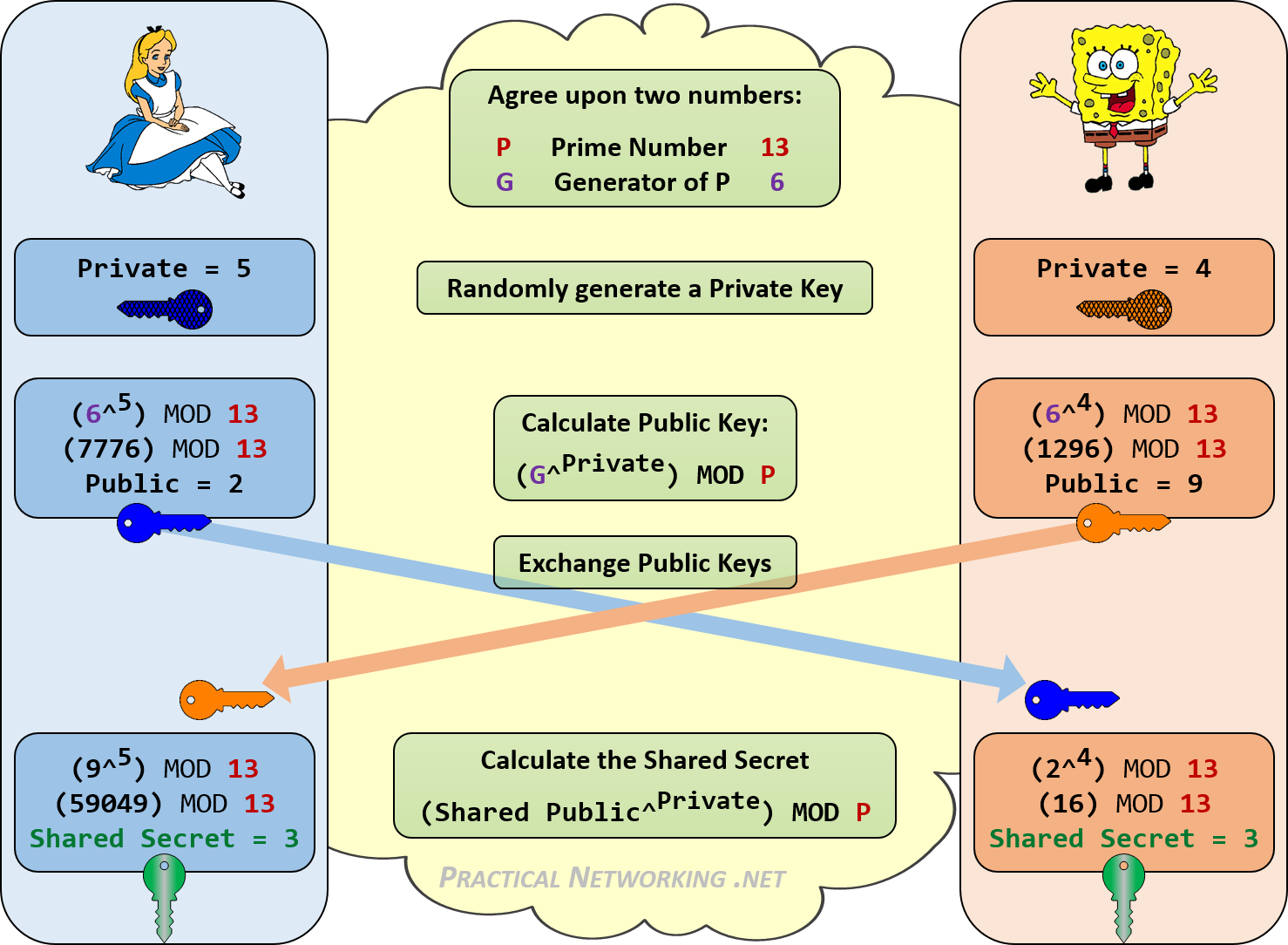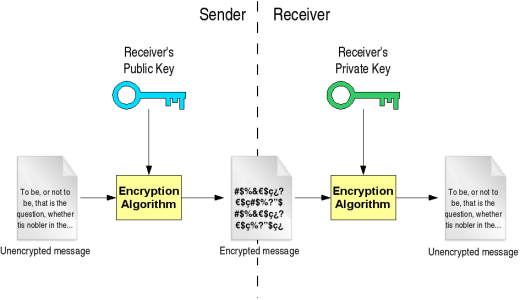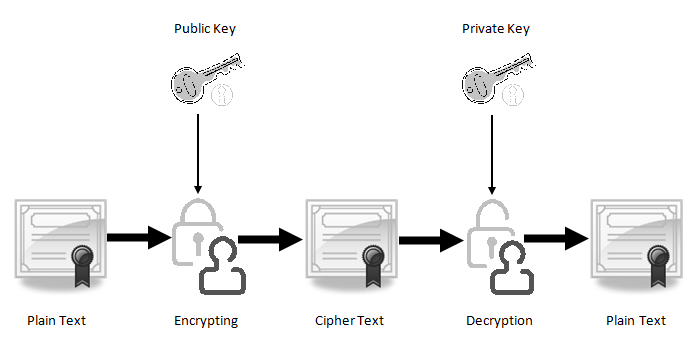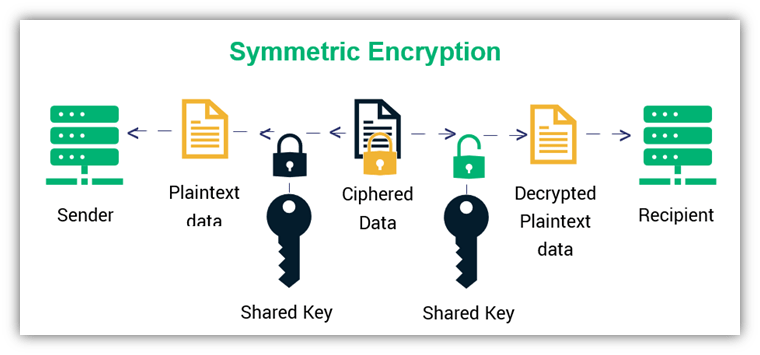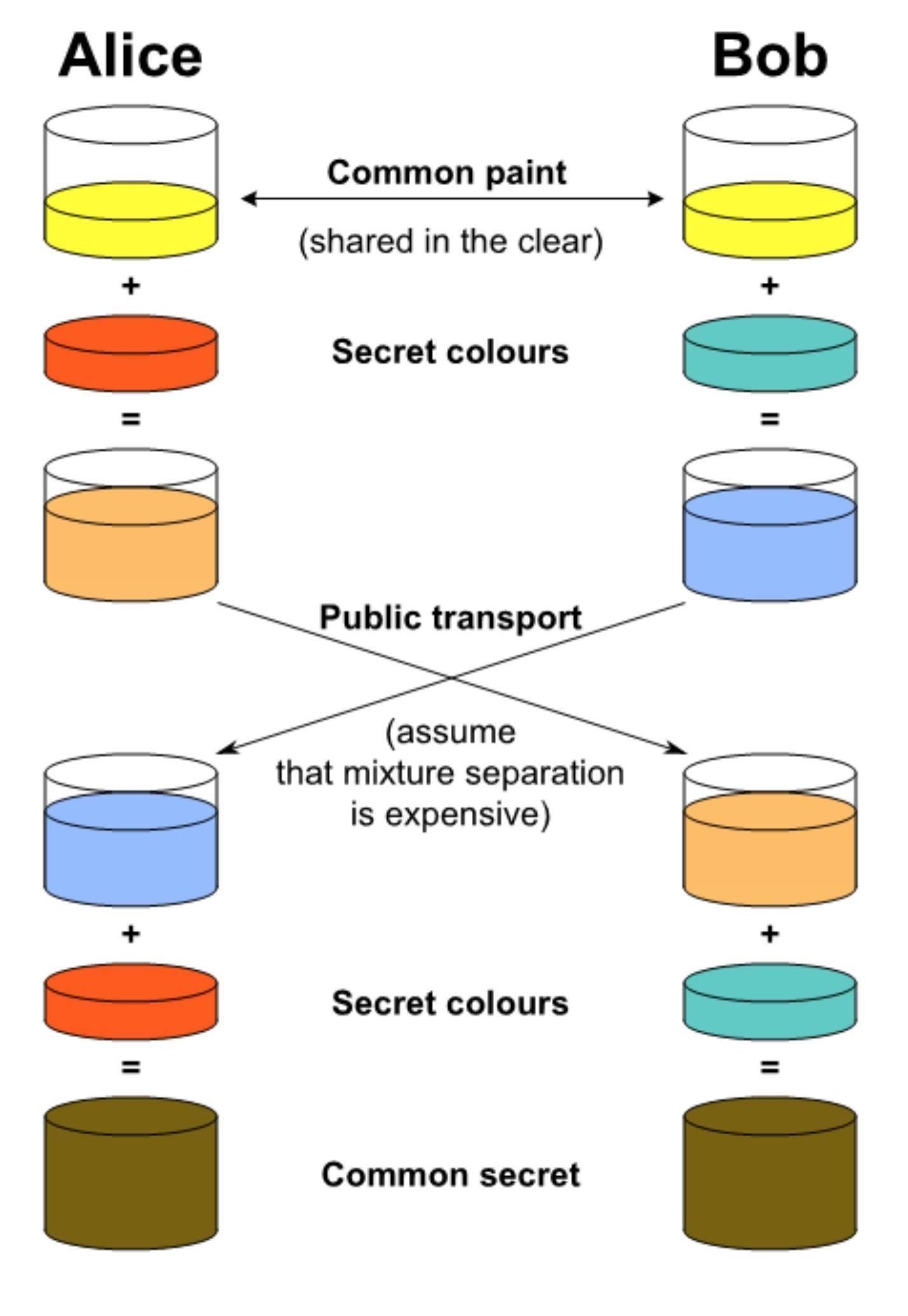
How to Generate Private Encryption Keys with the Diffie-Hellman Key Exchange « Null Byte :: WonderHowTo
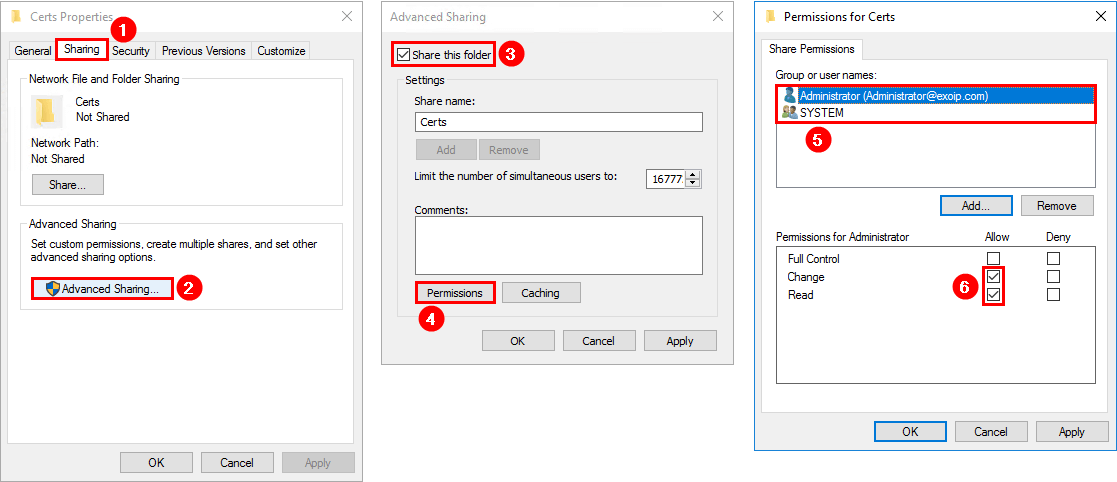
How-To: Sichere E-Mail Verschlüsselung in Office 365 - S/MIME Zertifikate in Outlook, OWA und Exchange Online - aConTech GmbH – Weil IT durch Menschen wirkt

Alex Xu on X: "Step 3 - After validating the SSL certificate, the client generates a session key and encrypts it using the public key. The server receives the encrypted session key