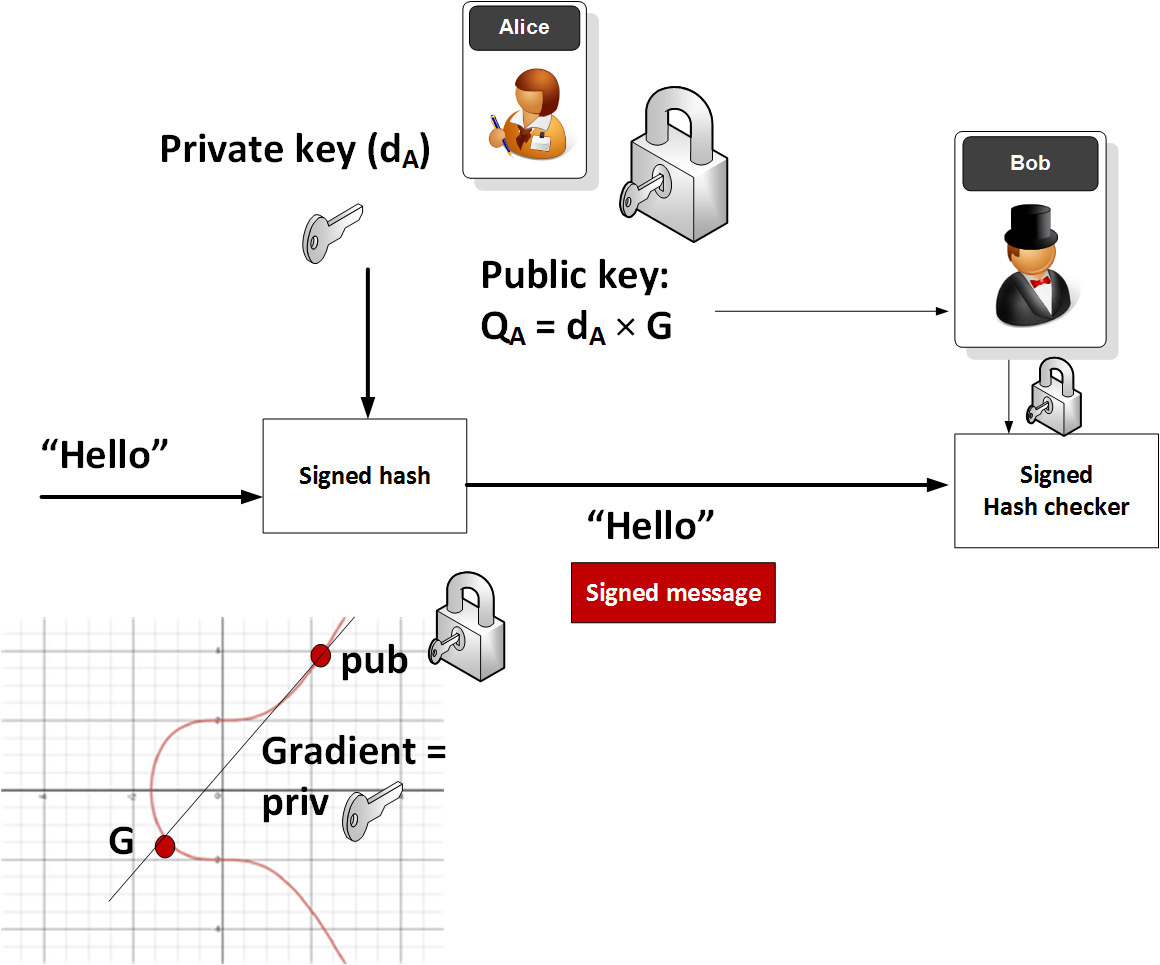
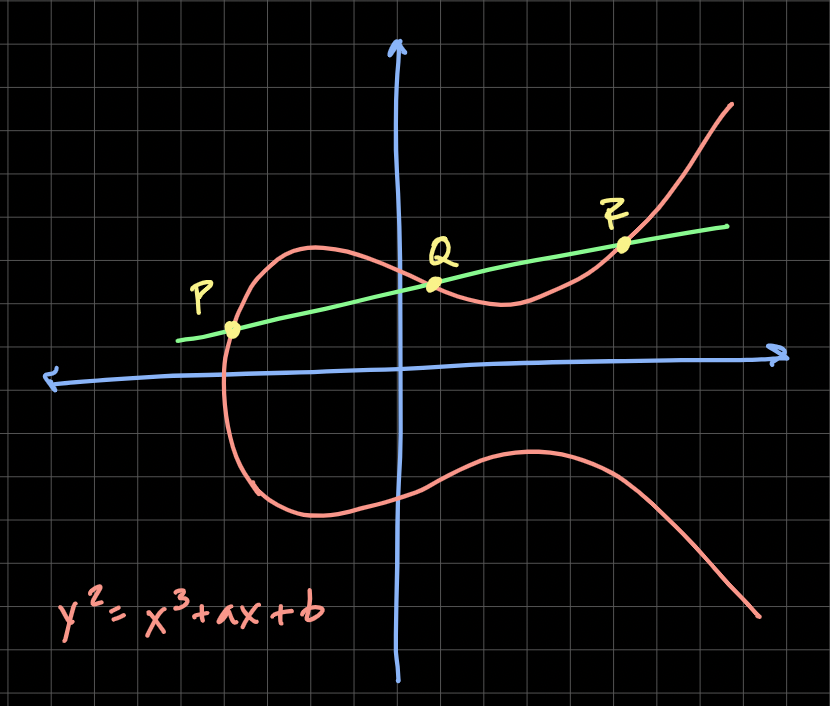
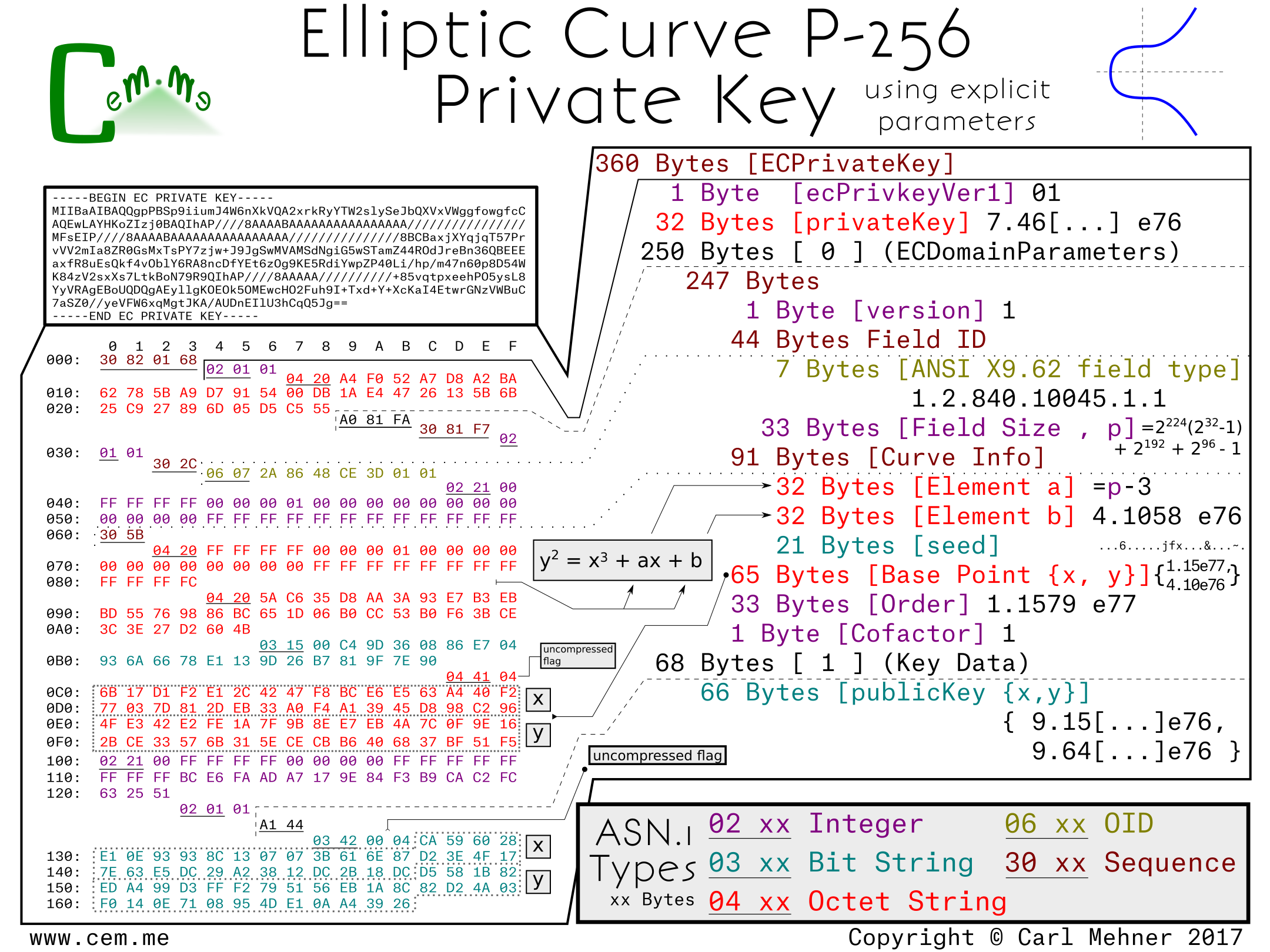
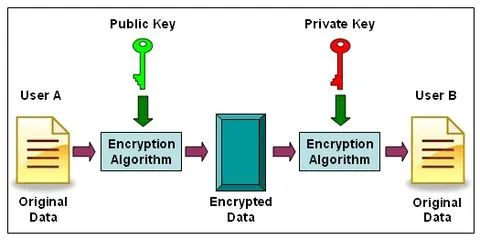
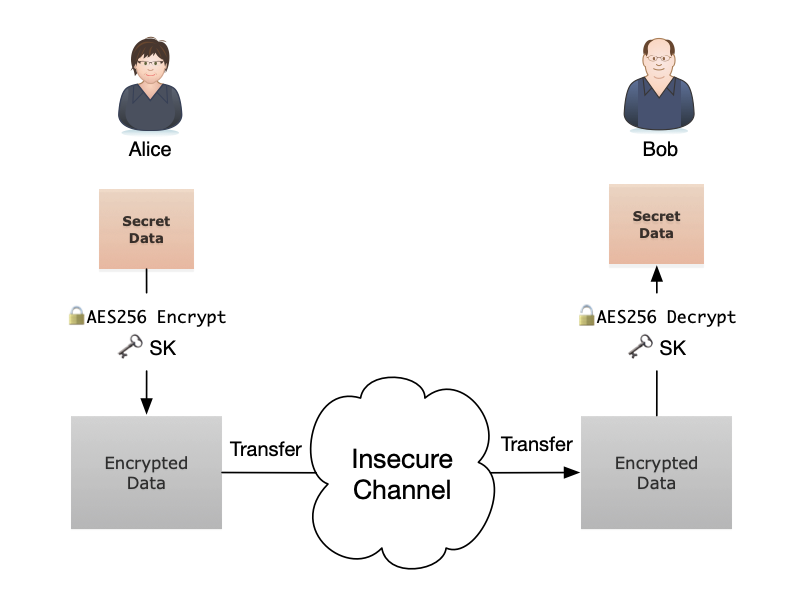
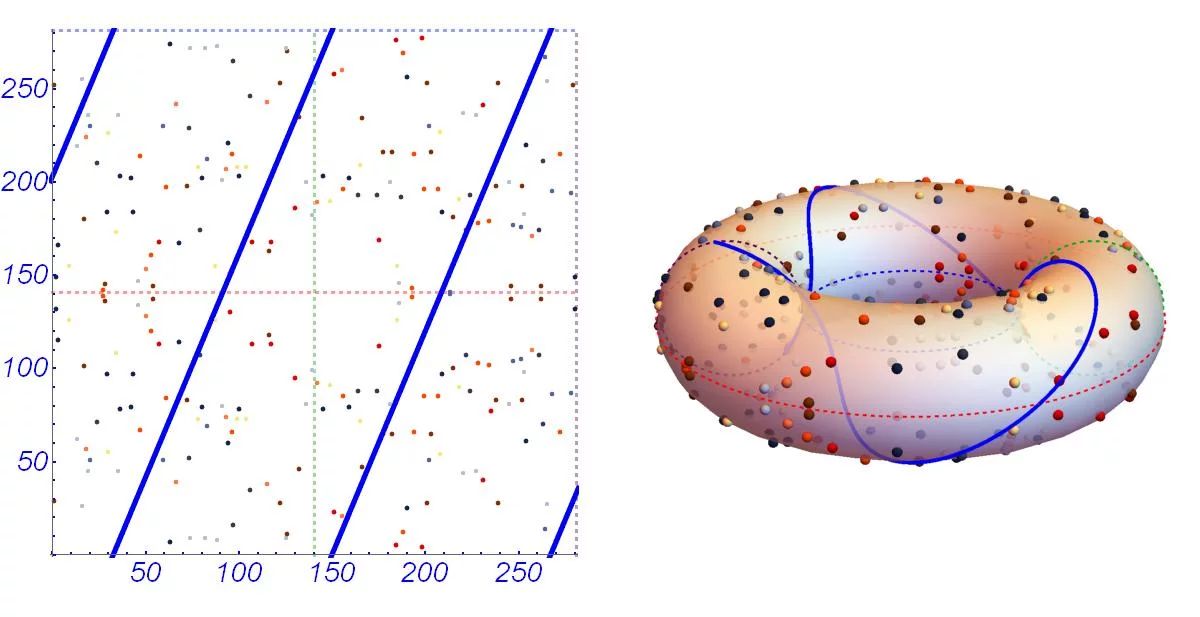
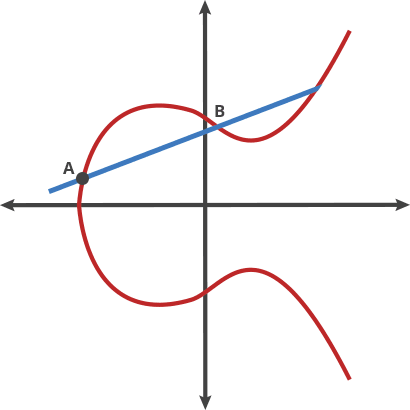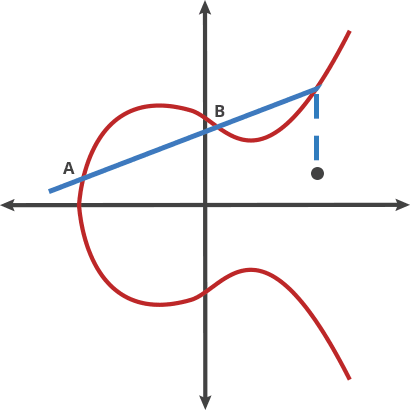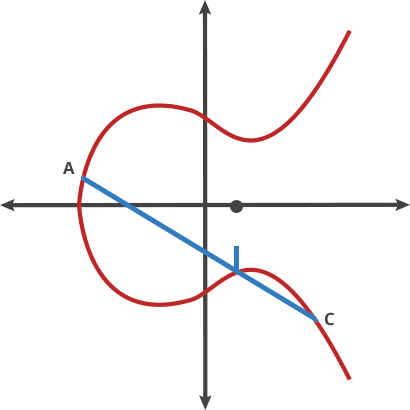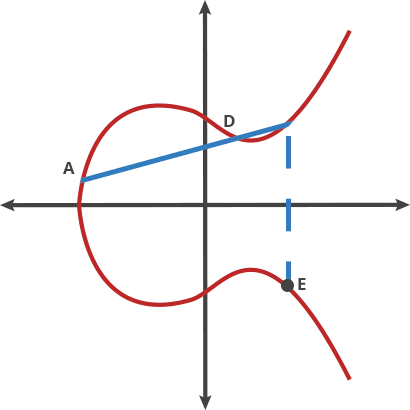
Public-Private Keys Generation & Signature Verification using ECDSA Algorithm. | by Sasha Flores | Medium
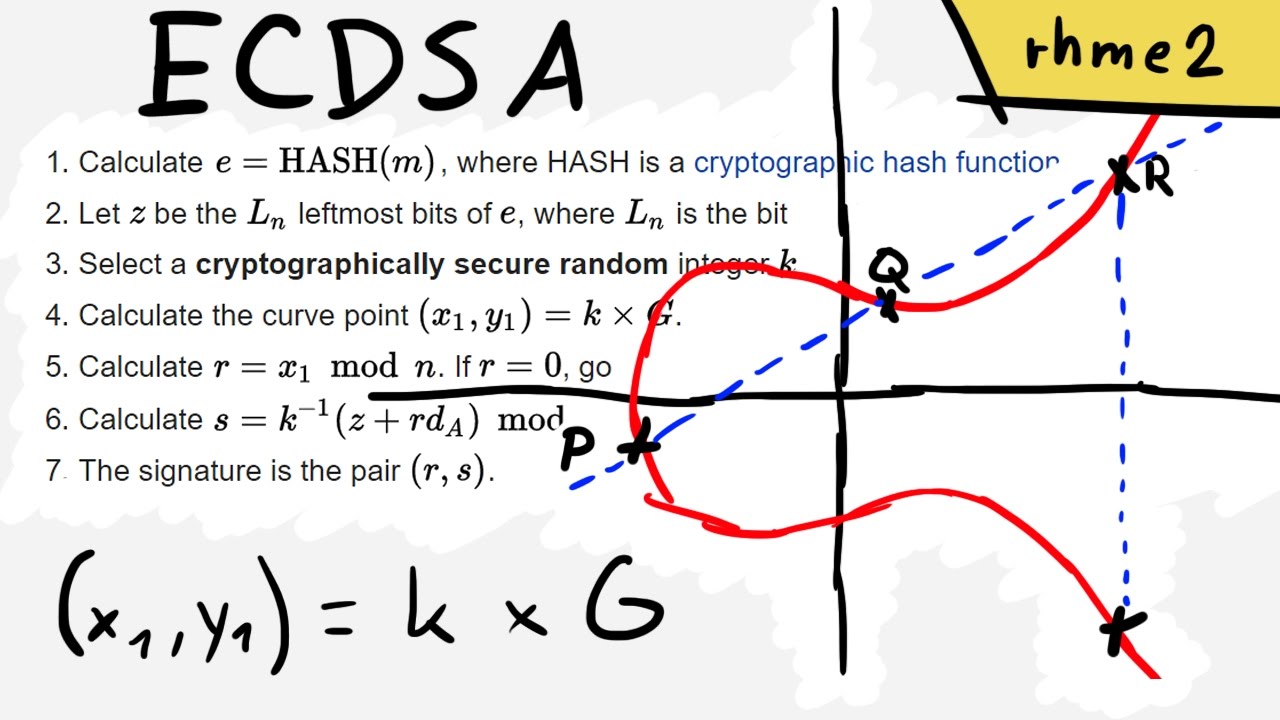
Breaking ECDSA (Elliptic Curve Cryptography) - rhme2 Secure Filesystem v1.92r1 (crypto 150) - YouTube
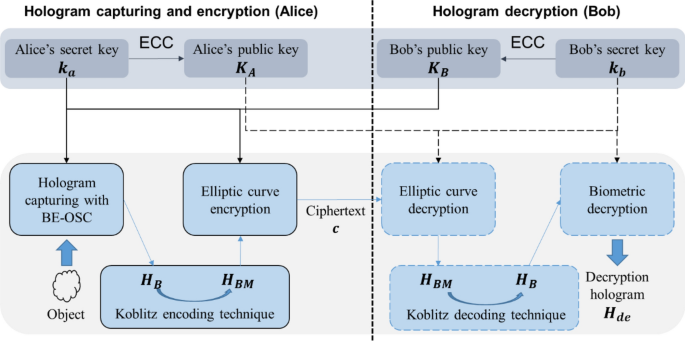
Asymmetric cryptosystem based on optical scanning cryptography and elliptic curve algorithm | Scientific Reports
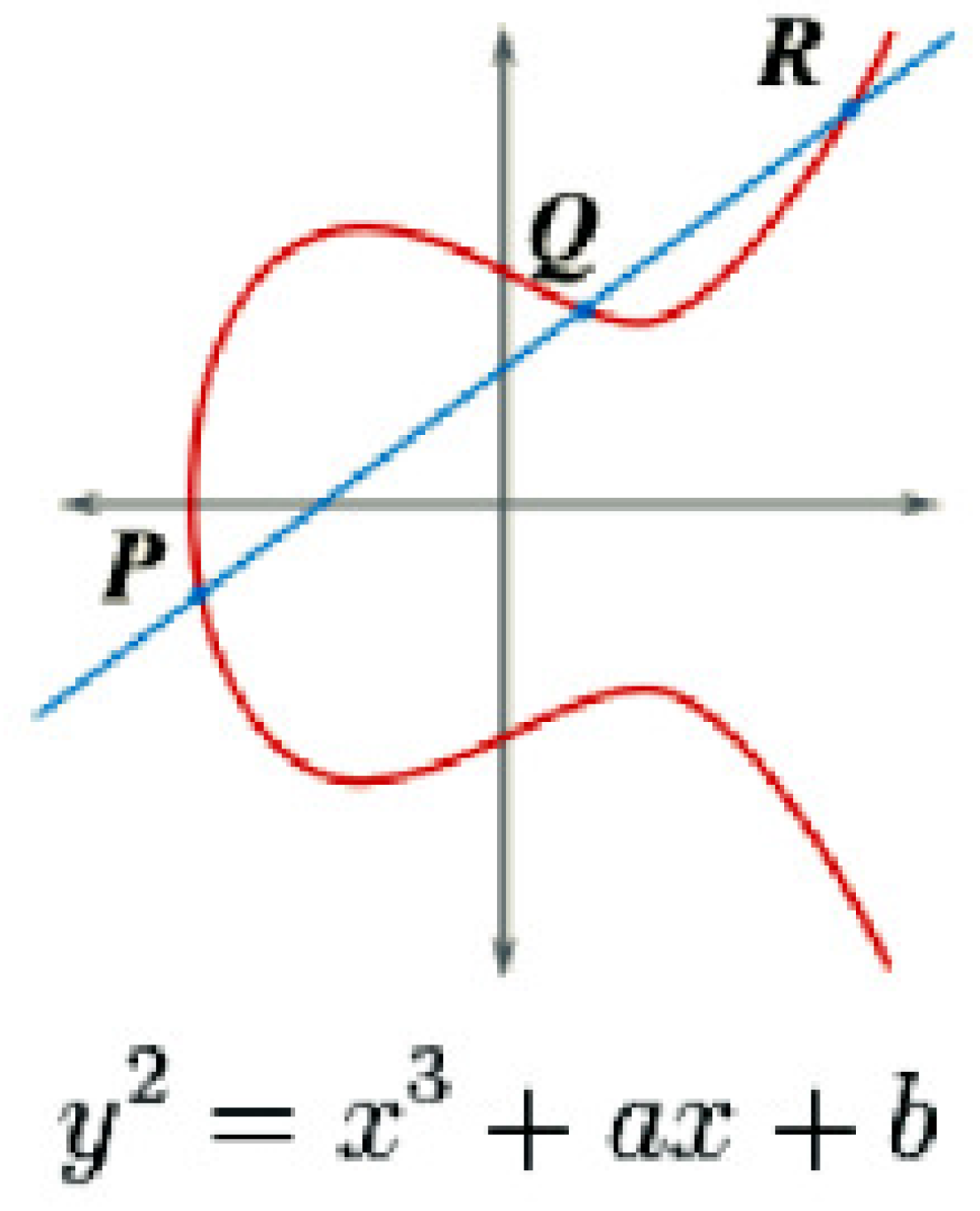
Cryptography | Free Full-Text | Cryptanalysis and Improvement of ECC Based Authentication and Key Exchanging Protocols