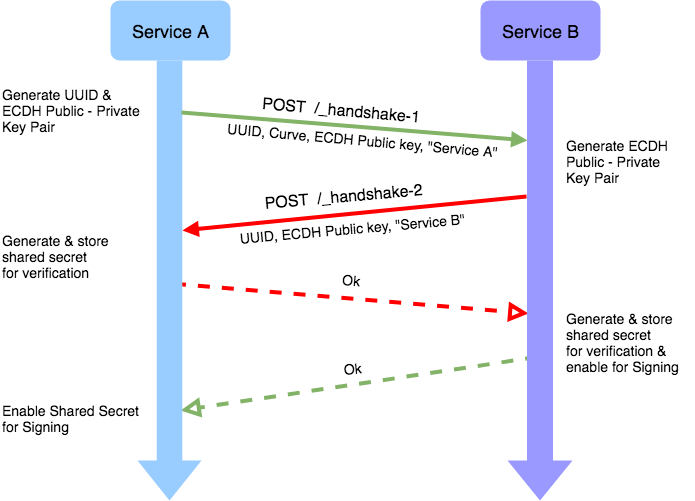
Inter-service authentication and the need for decentralised shared key exchange | by Krupa Sagar | Practo Engineering | Medium
ECDH P-256: Exporting public key to 'spki' format produces an invalid result · Issue #15523 · denoland/deno · GitHub
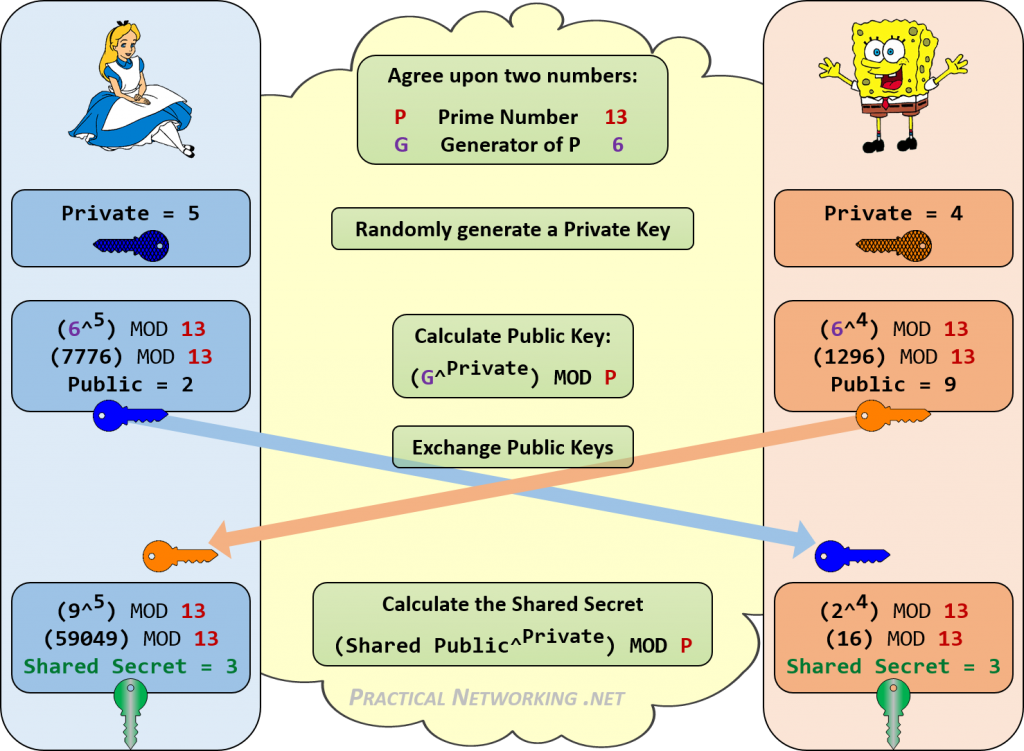
Implementing Elliptic-curve Diffie–Hellman Key Exchange Algorithm using C# (cross-platform) | David Tavarez
libp11 does not support ECDH key derivation is OpenSSL versions < 1.1 · Issue #49 · OpenSC/libp11 · GitHub

Where Would You Find Both ECC and RSA Working Well Together? Well, In Virtually Every Web Connection | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium

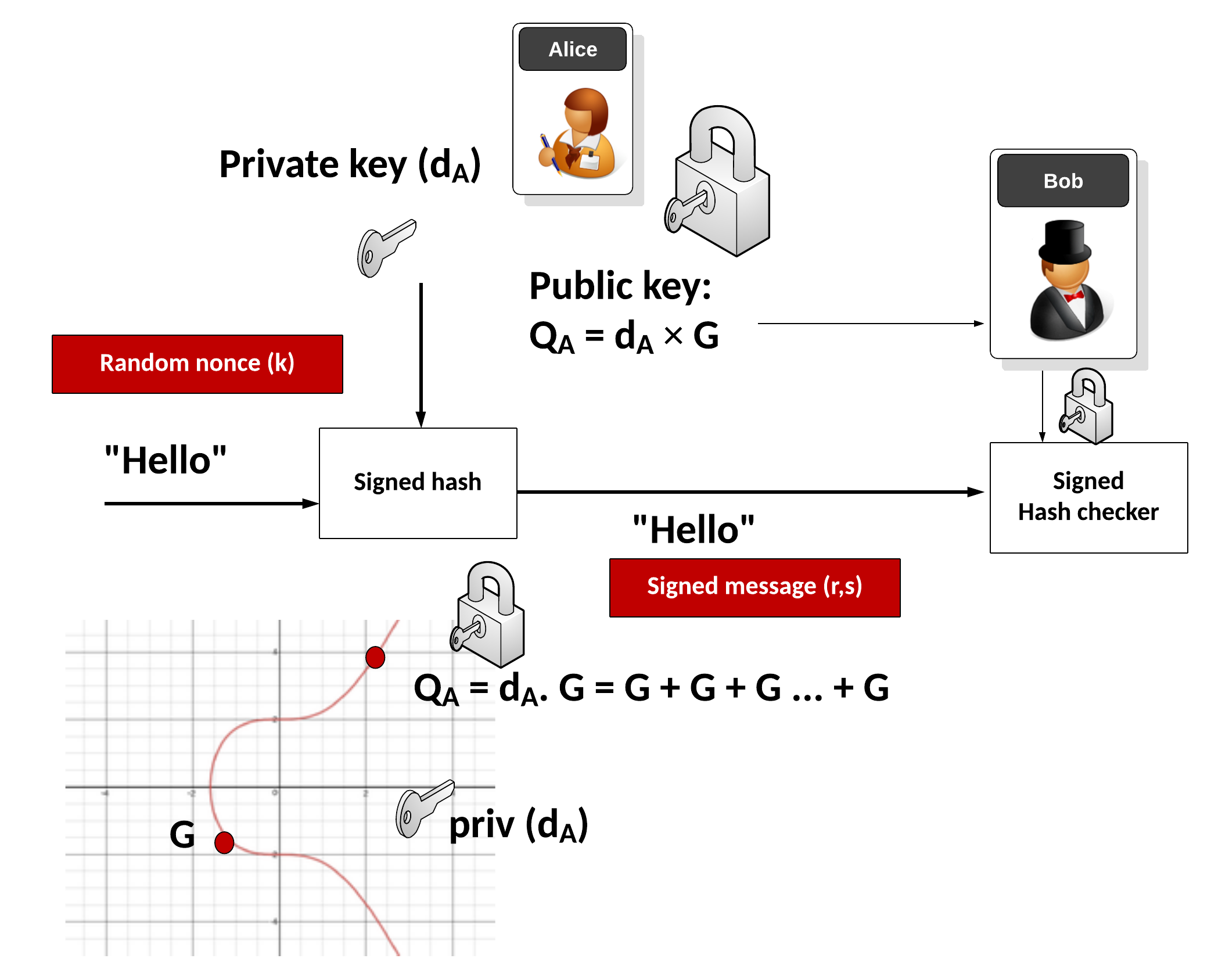

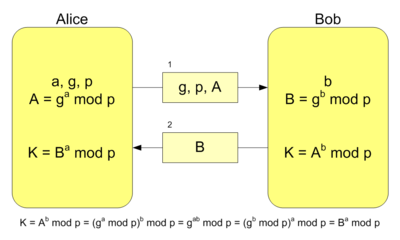










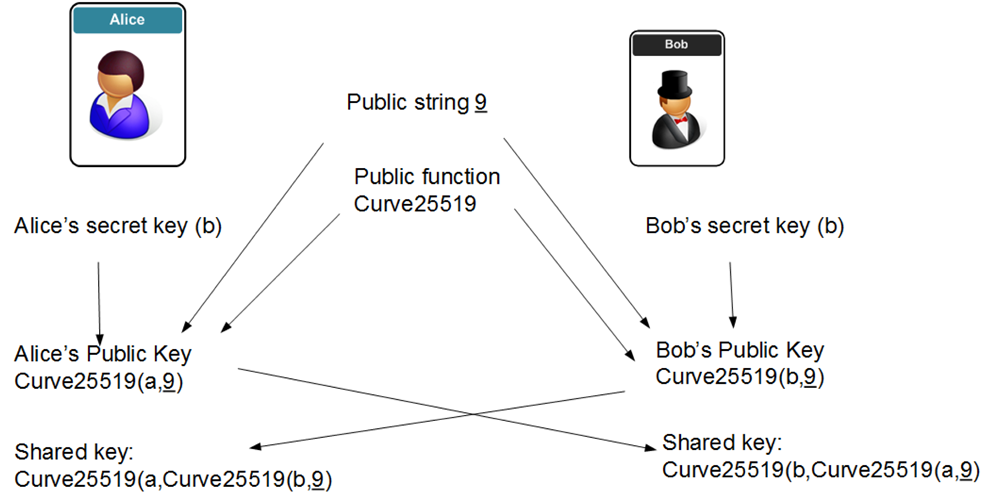

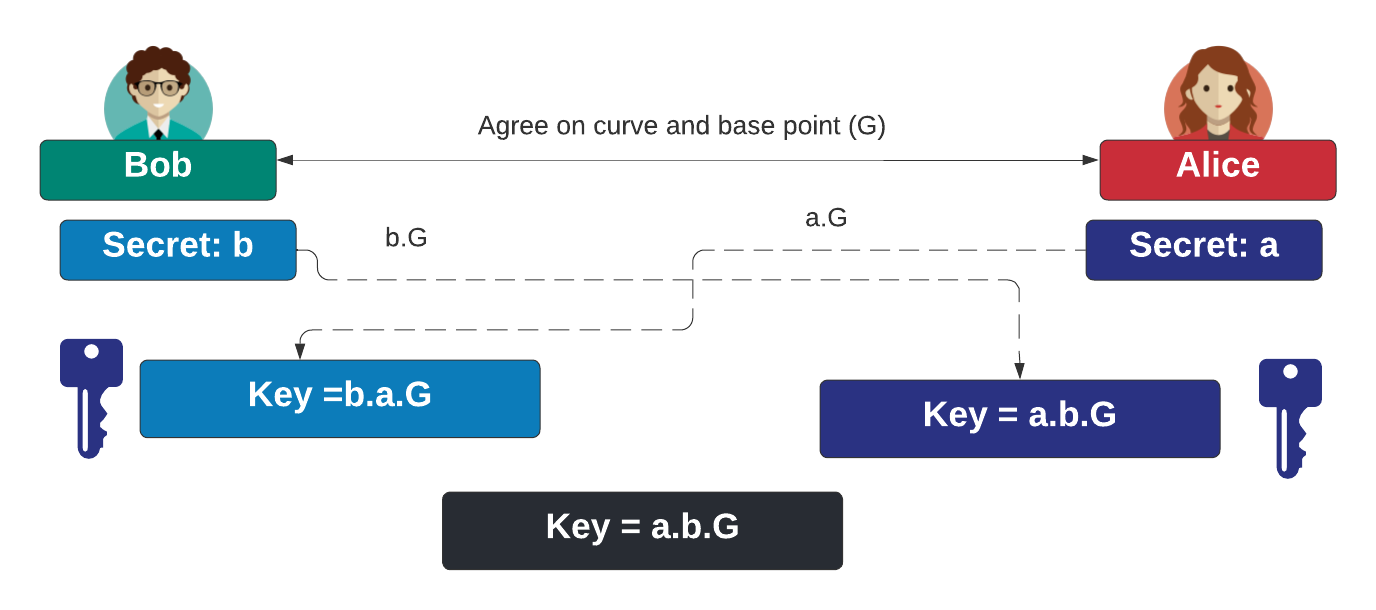
![PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar PDF] The Elliptic Curve Diffie-Hellman (ECDH) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/de032e79b6116aeb3efc26de258903d6fdc24a08/1-Figure1-1.png)
