SOLID CONFIG: Cisco DHCP Snooping and IP Device Tracking for IOS-XE Devices (SISF based) — WIRES AND WI.FI
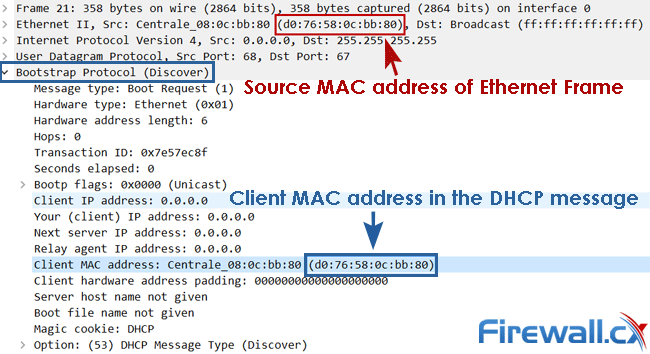
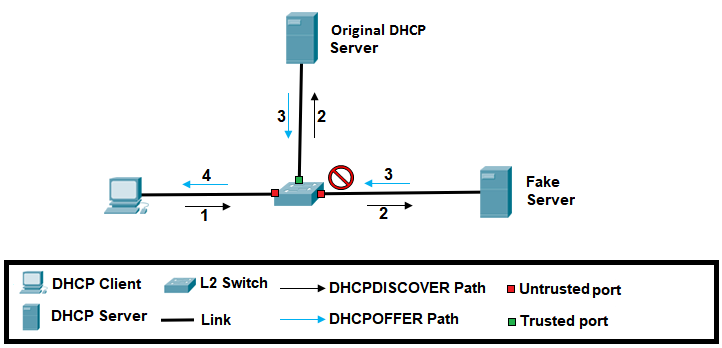
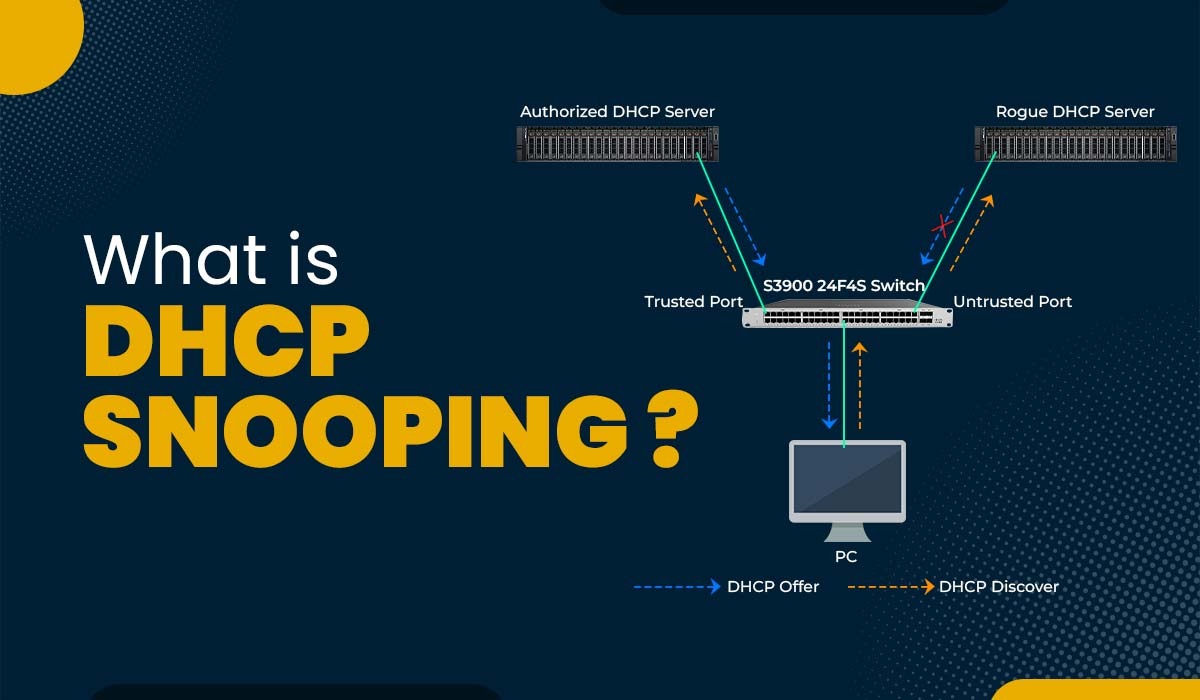
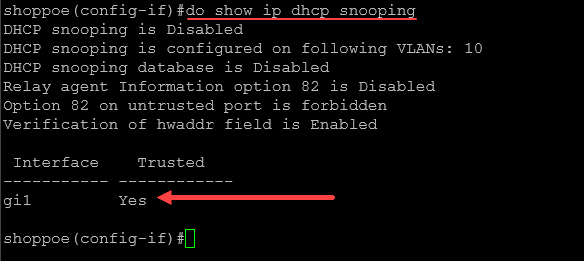
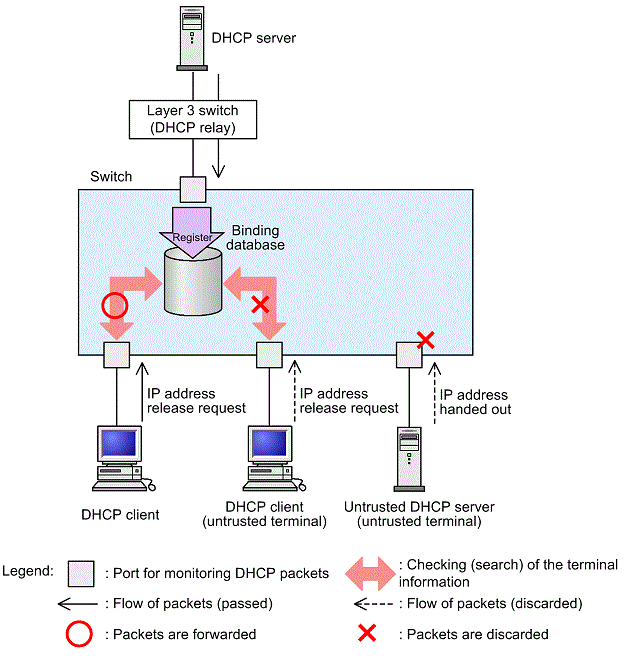
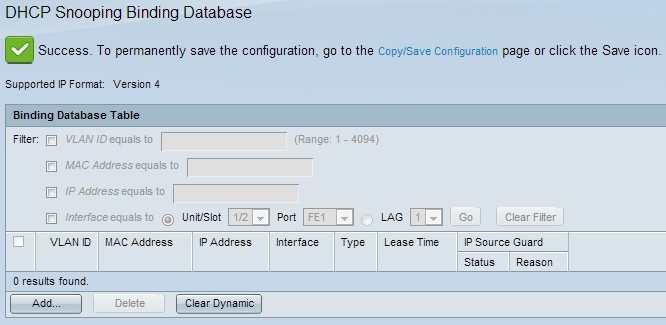
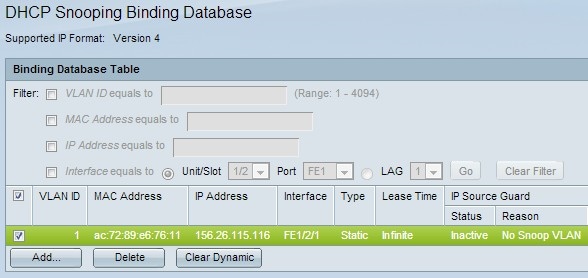
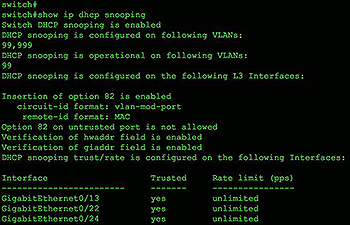
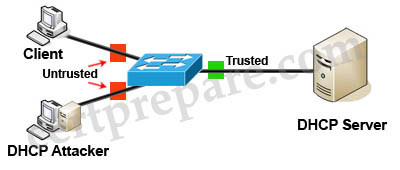
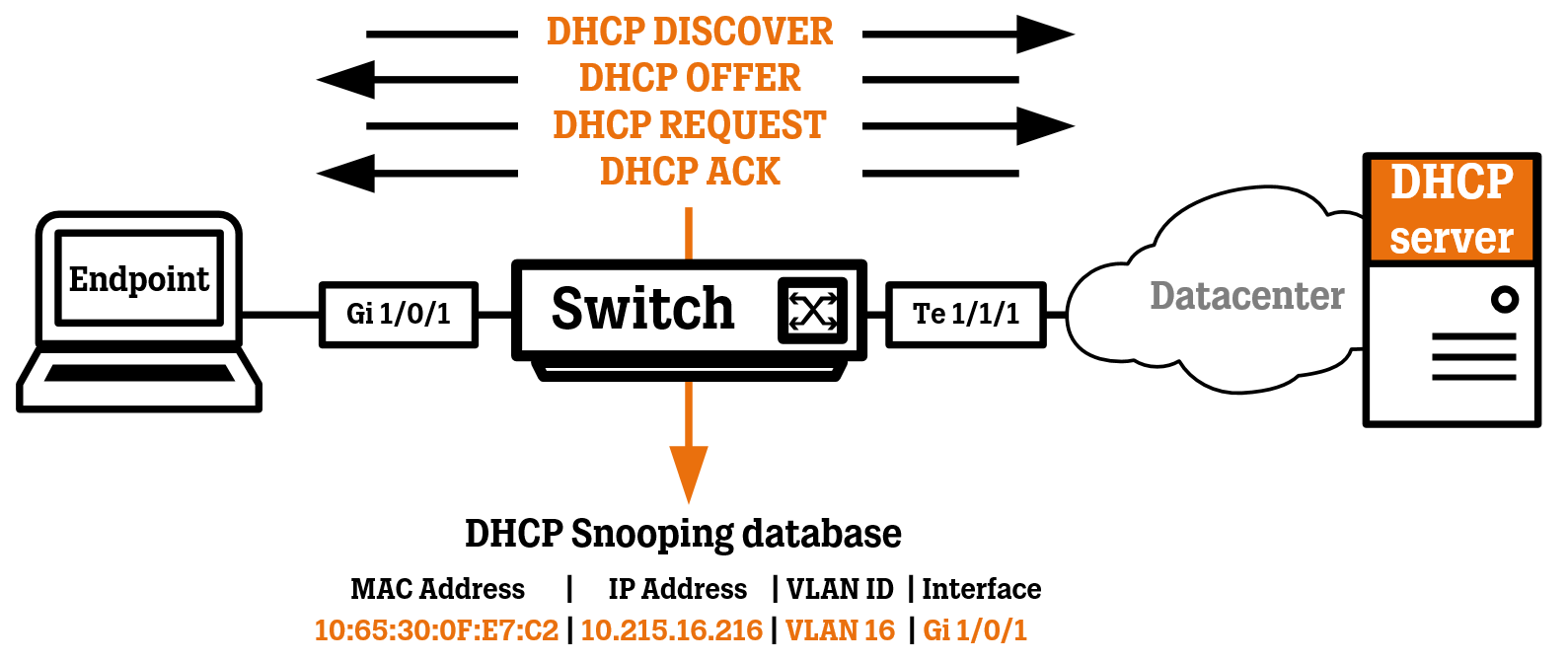
Complete Guide to DHCP Snooping, How it Works, Concepts, DHCP Snooping Database, DHCP Option 82, Mitigating DHCP Starvation Attacks, DHCP Hijacking, Man-in-the-Middle Attacks & Rogue DHCP Servers
SOLID CONFIG: Cisco DHCP Snooping and IP Device Tracking for IOS-XE Devices (SISF based) — WIRES AND WI.FI
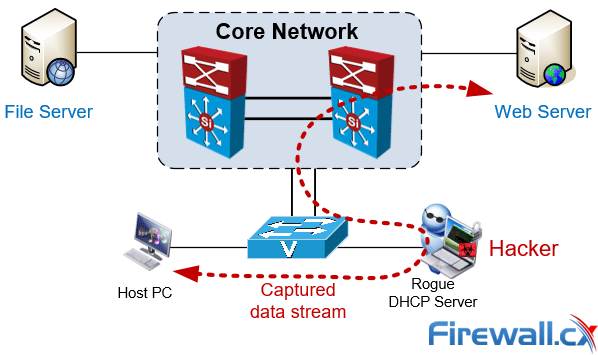
Complete Guide to DHCP Snooping, How it Works, Concepts, DHCP Snooping Database, DHCP Option 82, Mitigating DHCP Starvation Attacks, DHCP Hijacking, Man-in-the-Middle Attacks & Rogue DHCP Servers