
Known Plaintext attack vs Chosen plaintext attack - Blog on Information Security and other technical topics

PDF) Related-Key and Slide Attacks: Analysis Connections and Improvements | Jean-jacques Quisquater - Academia.edu

Wonk post: chosen ciphertext security in public-key encryption (Part 1) – A Few Thoughts on Cryptographic Engineering

An adversary's chosen plaintext attack for key recovery against our... | Download Scientific Diagram
GitHub - dj311/rc4-key-recovery-attacks: Exploits weaknesses in RC4 to mount a chosen-plaintext attack and recover the private key. The vulnerability is similar to the one used to crack WEP, but it targets schemes

PDF) Chosen Ciphertext Attacks Against Protocols Based on the RSA Encryption Standard PKCS #1 | Aji Setiyo - Academia.edu

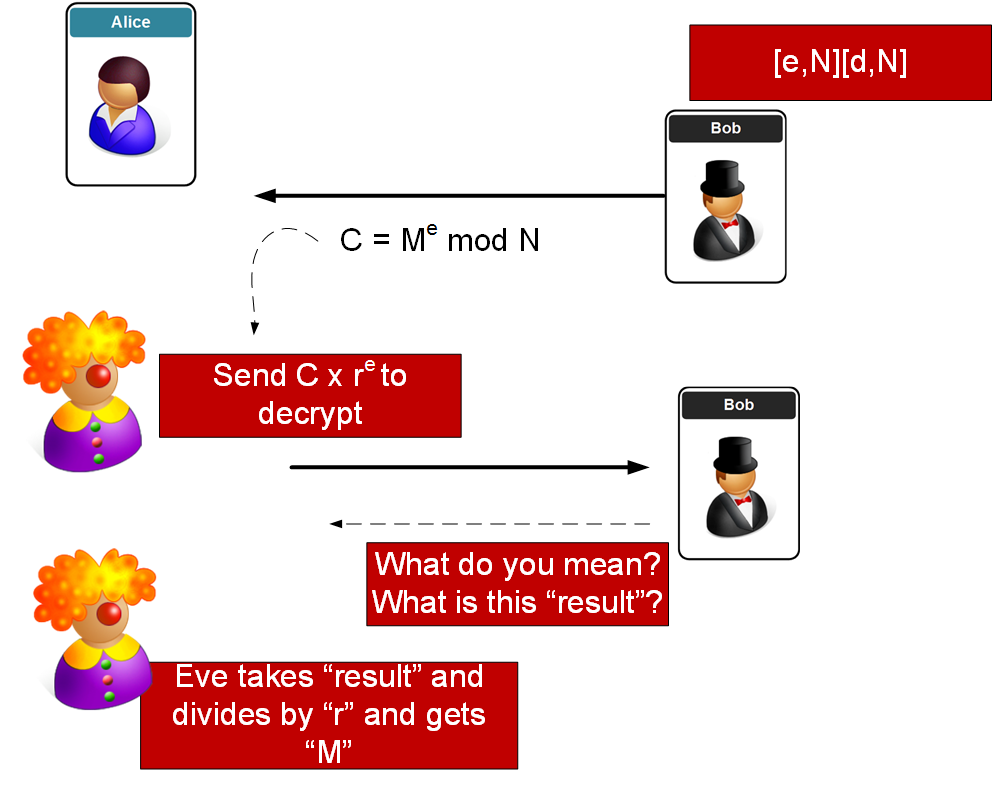






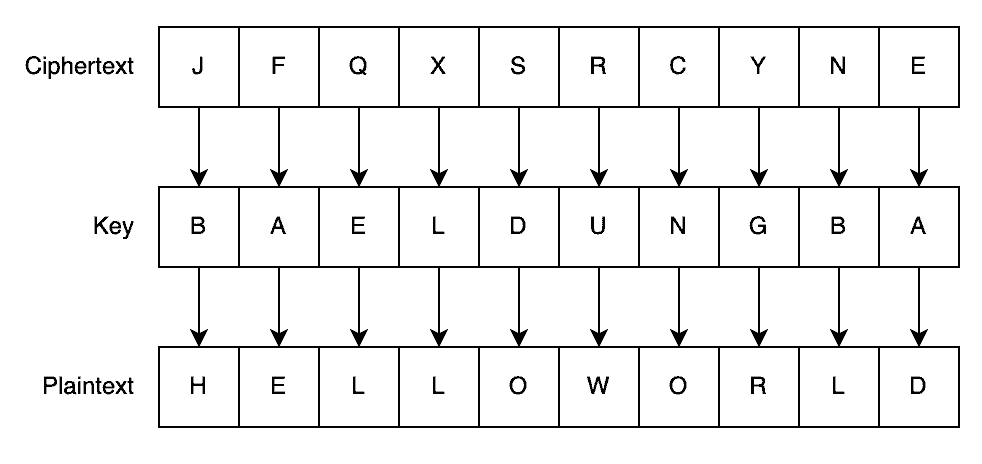
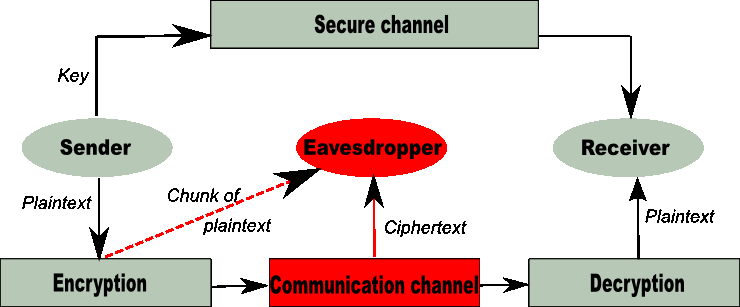




![PDF] A chosen key attack against the secret S-boxes of GOST | Semantic Scholar PDF] A chosen key attack against the secret S-boxes of GOST | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/6576224b8438e79bafc85bfb7da561dfa12bc822/3-Figure1-1.png)

