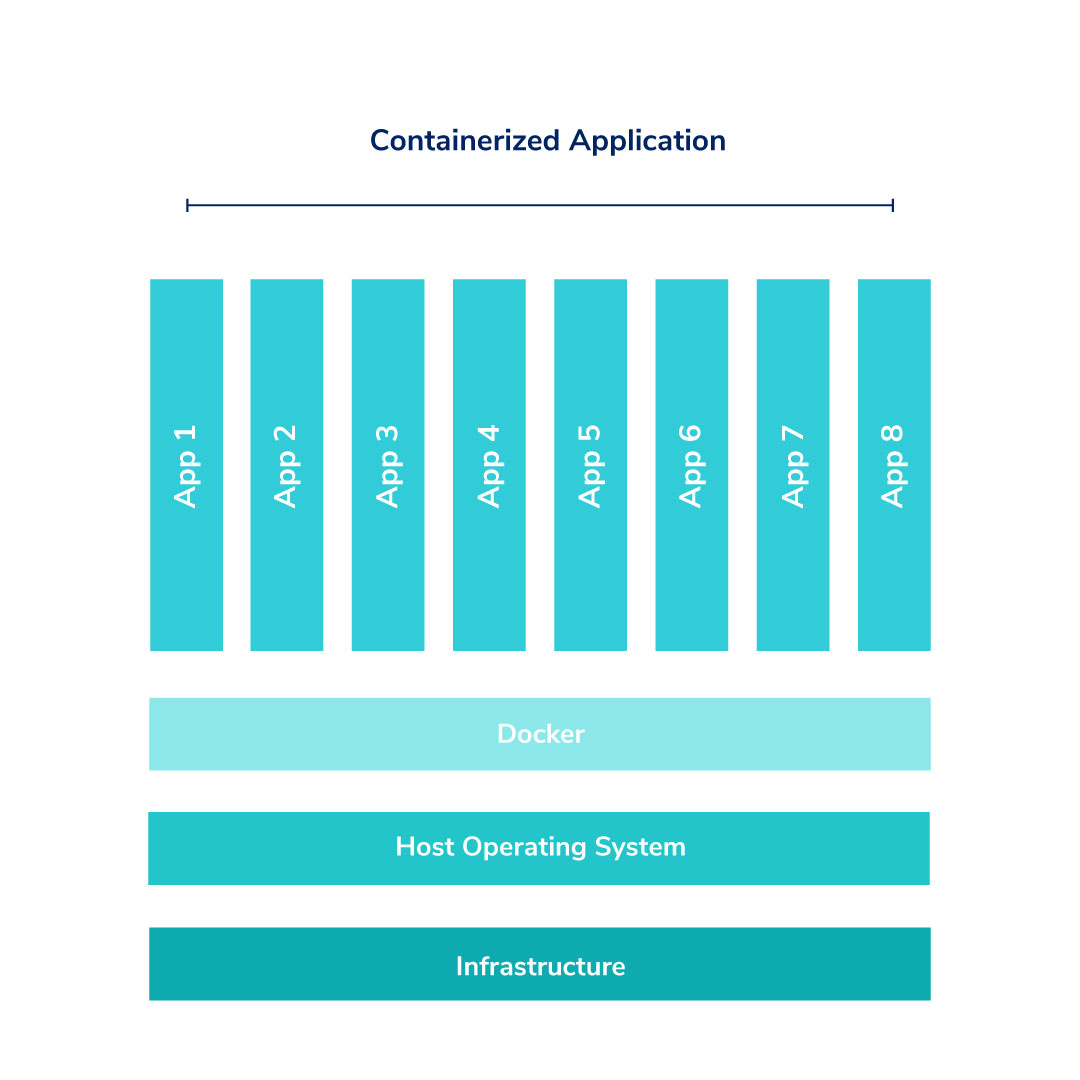
Evolving Container Security With Linux User Namespaces | by Netflix Technology Blog | Netflix TechBlog
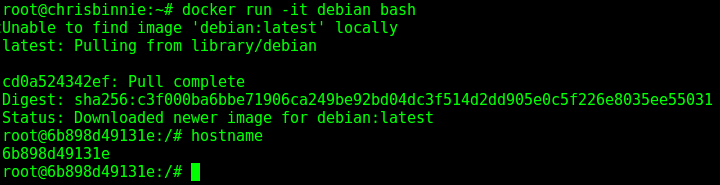
Why am I able to bind a privileged port in my container without the NET_BIND_SERVICE capability? | by Olivier Gaumond | Medium

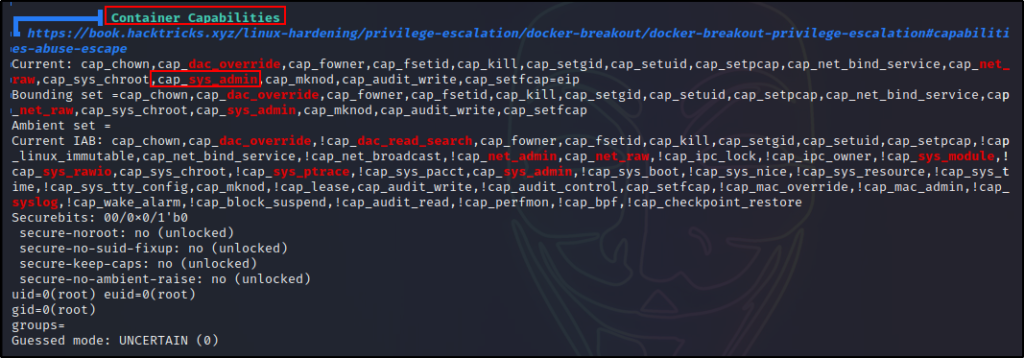
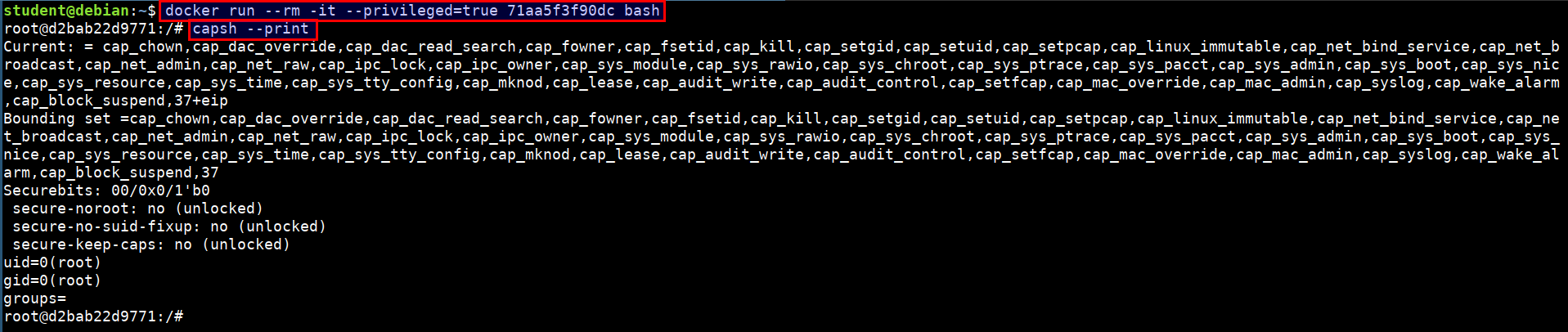
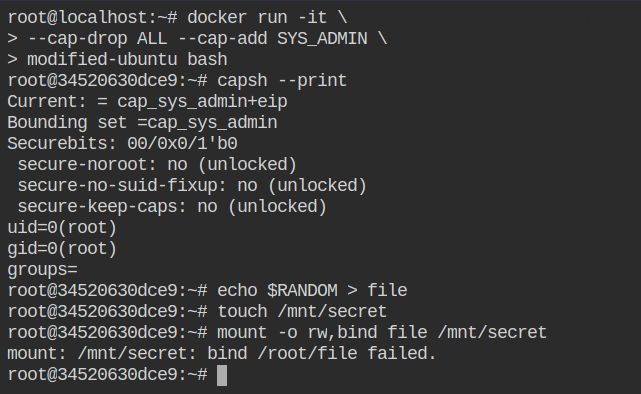
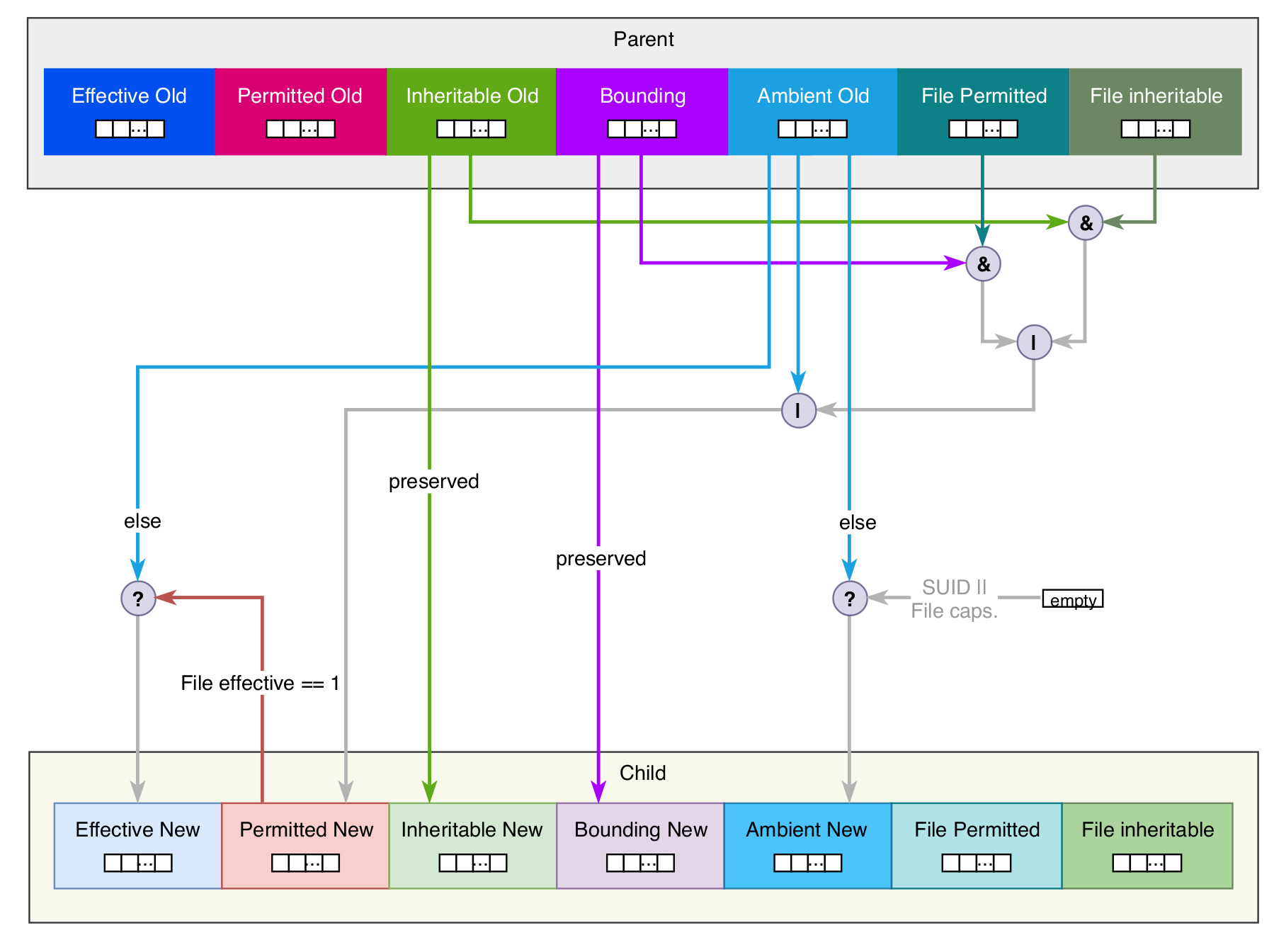
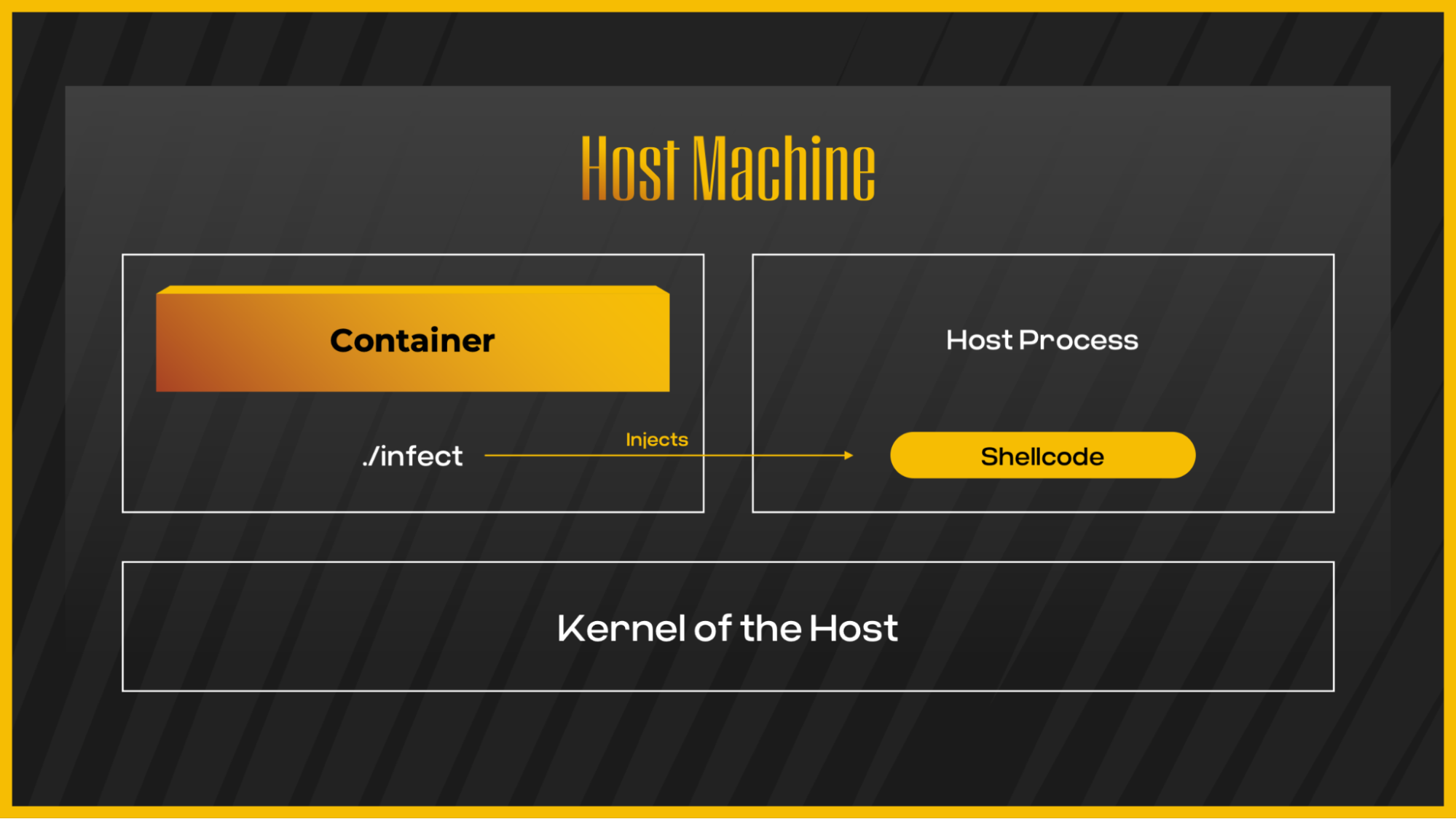
Accuracy w/r/t https://github.com/docker/labs/tree/master/security/capabilities · Issue #469 · docker/labs · GitHub

Accuracy w/r/t https://github.com/docker/labs/tree/master/security/capabilities · Issue #469 · docker/labs · GitHub

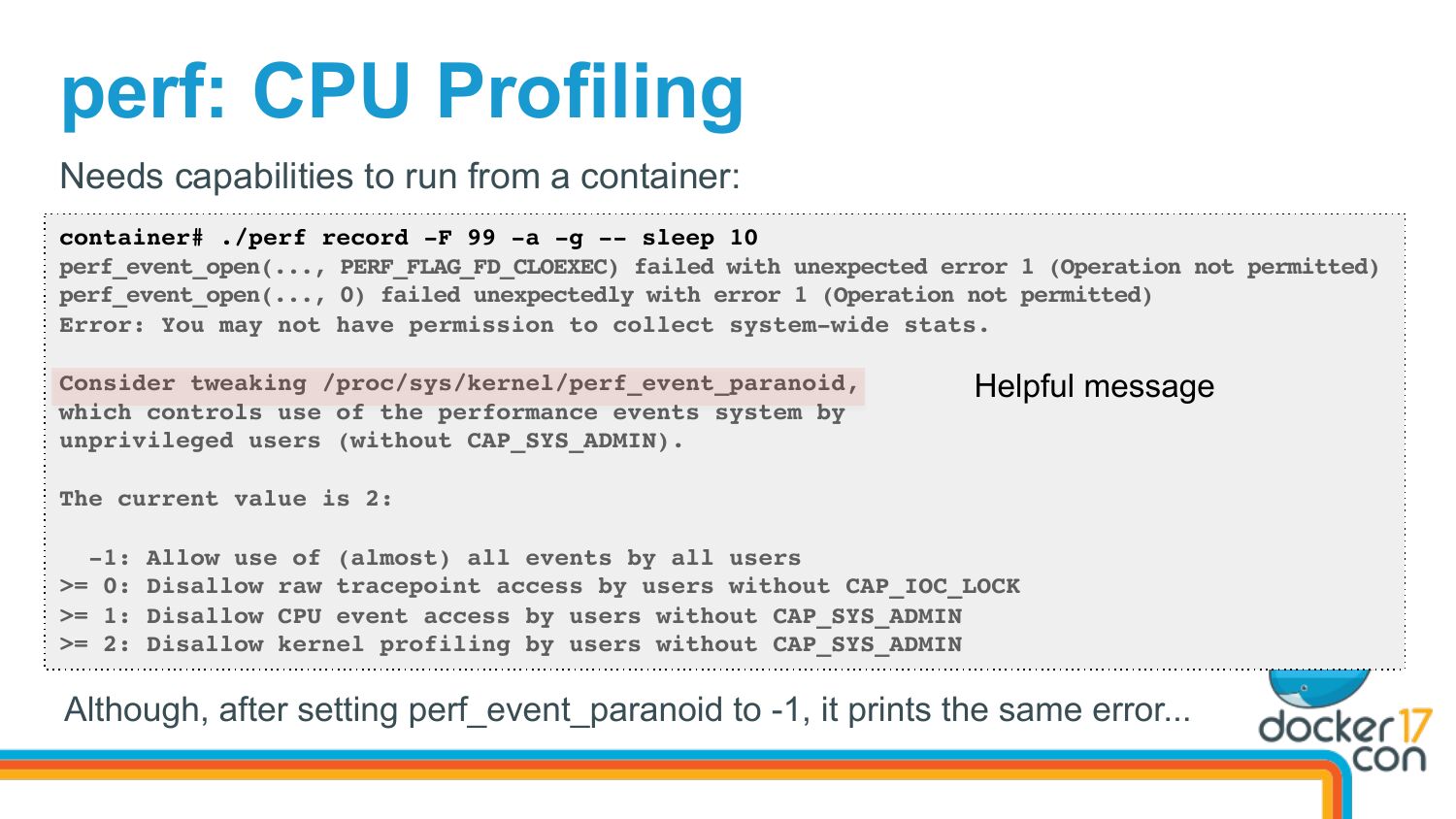
Profiling application running on 2 different docker containers using Intel® VTune™ Profiler - Stack Overflow