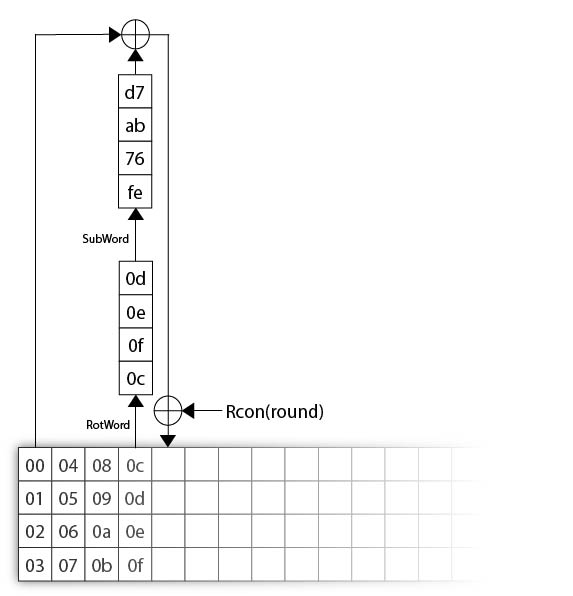
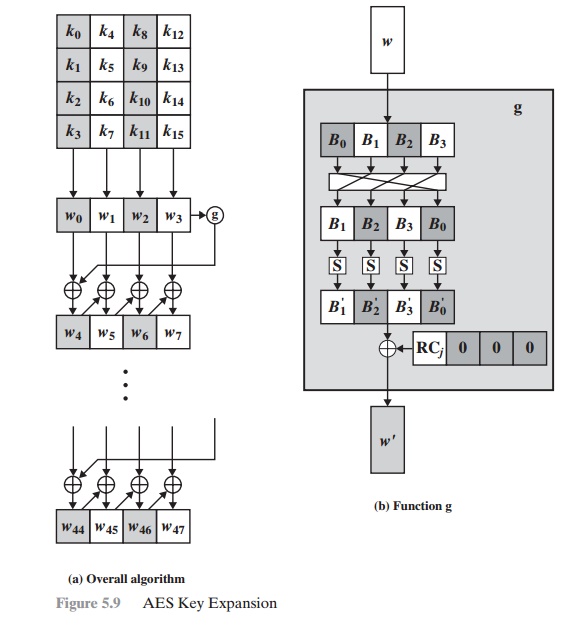
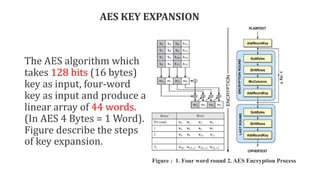
![PDF] Enhanced Key Expansion Algorithm for Advanced Encryption Standard using Different S-Box Implementation on FPGA | Semantic Scholar PDF] Enhanced Key Expansion Algorithm for Advanced Encryption Standard using Different S-Box Implementation on FPGA | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/5e2b3c1a6c6ad19203b878fa05fed089543a5998/2-Figure1-1.png)
PDF] Enhanced Key Expansion Algorithm for Advanced Encryption Standard using Different S-Box Implementation on FPGA | Semantic Scholar

FPGA based fast and high-throughput 2-slow retiming 128-bit AES encryption algorithm - ScienceDirect

A novel differential fault analysis using two‐byte fault model on AES Key schedule - Zhang - 2019 - IET Circuits, Devices & Systems - Wiley Online Library

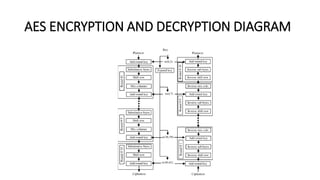
Figure: Structure of AES III. Implementation The AES algorithm is based... | Download Scientific Diagram
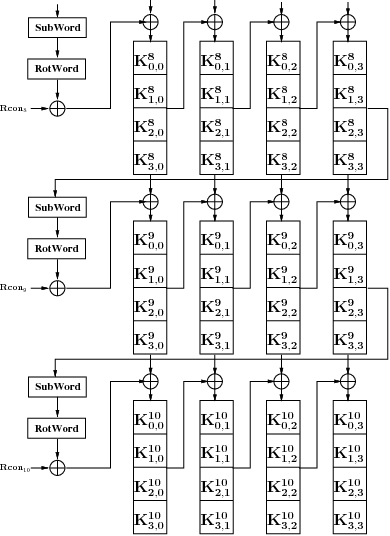


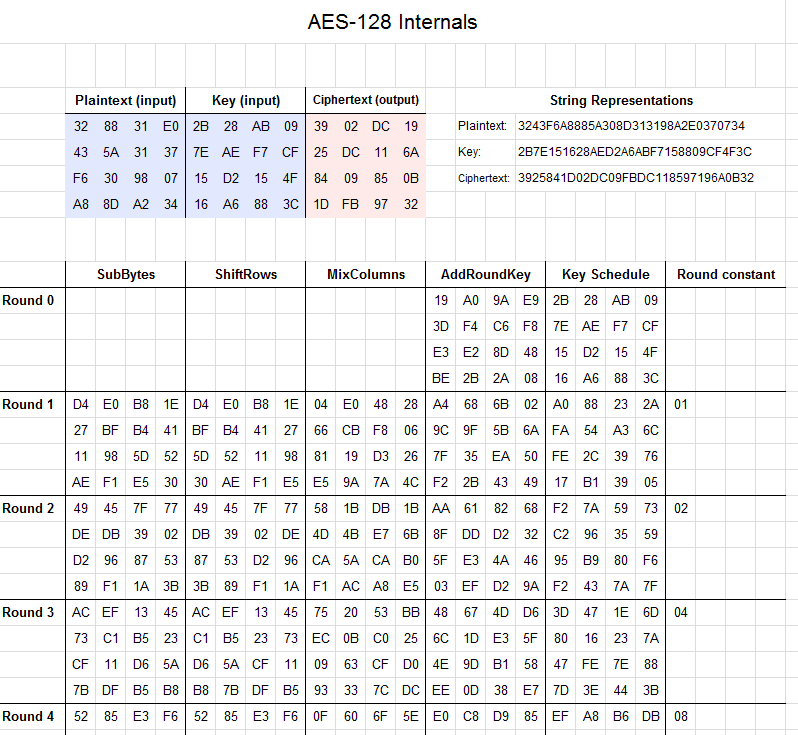

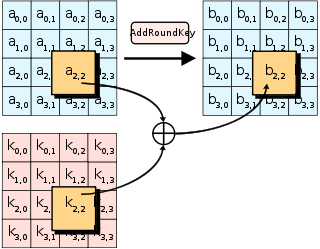
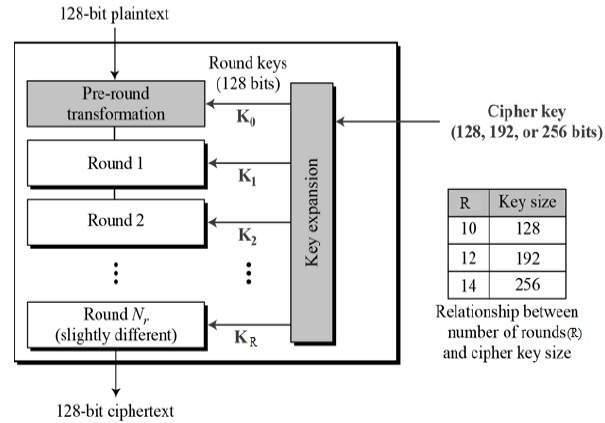
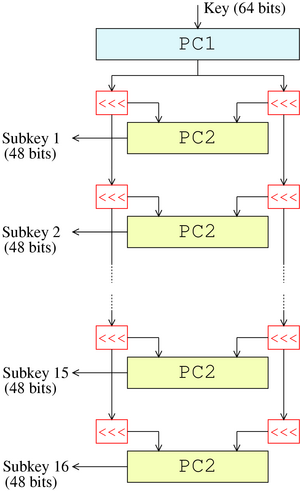

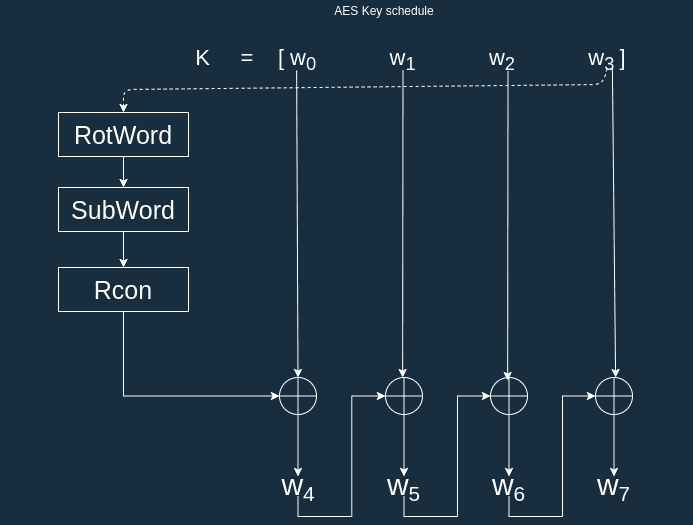
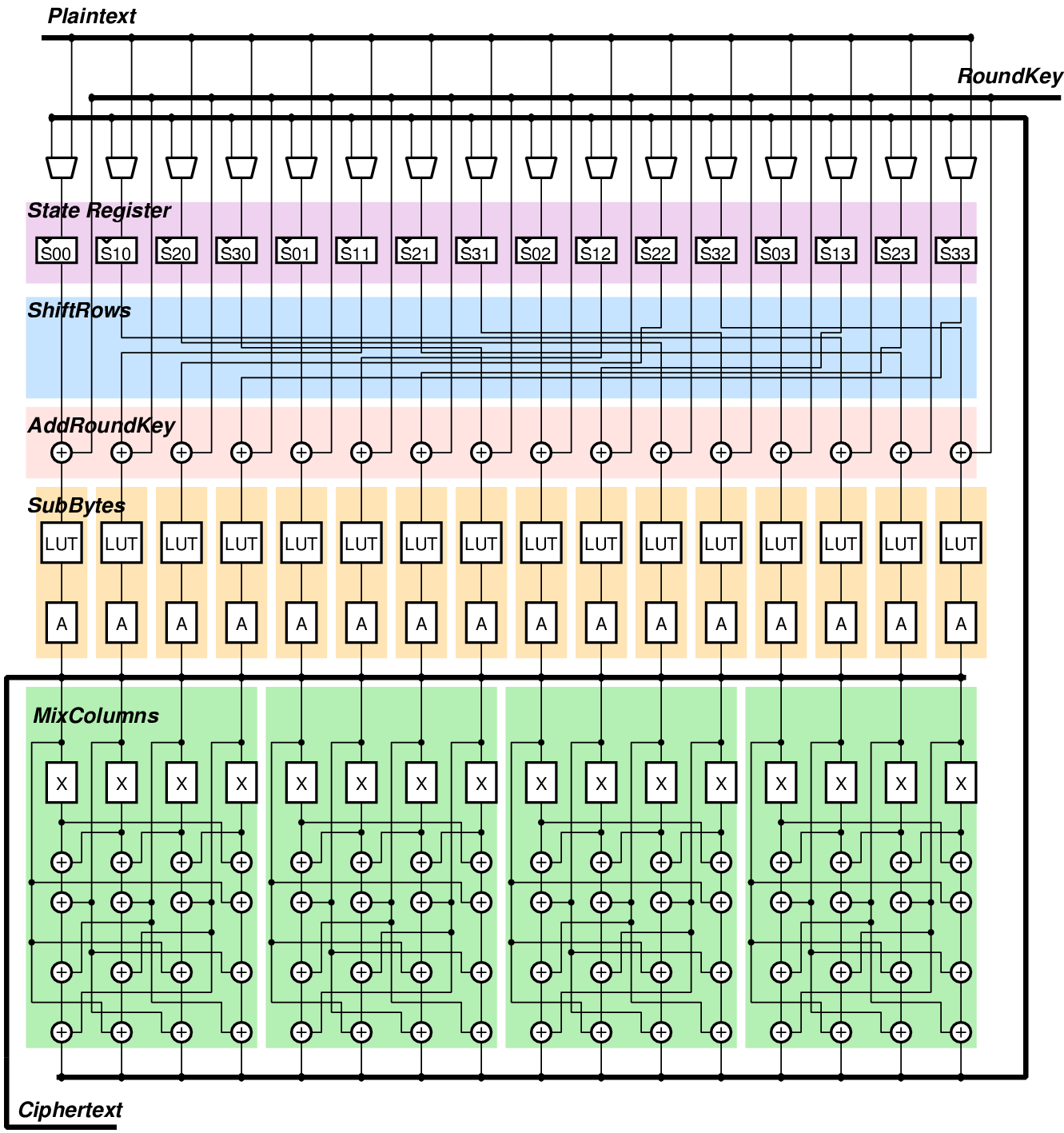

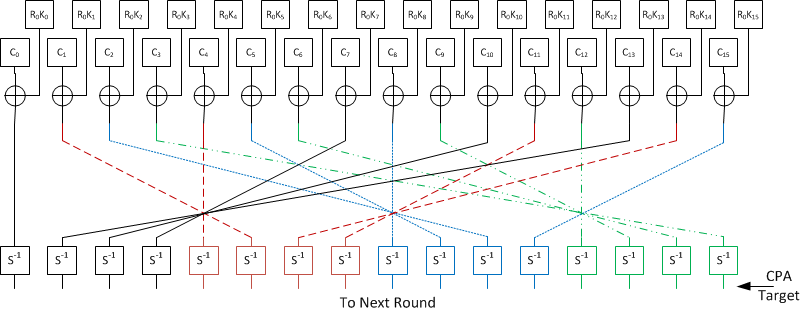
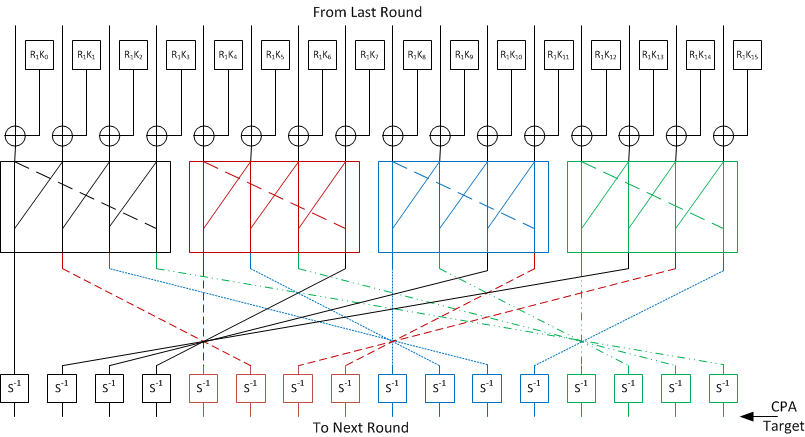
![PDF] Combined Attacks on the AES Key Schedule | Semantic Scholar PDF] Combined Attacks on the AES Key Schedule | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/a44f9ea37b8b50d2fbaeb5ad7c0df33031422a2c/3-Figure1-1.png)