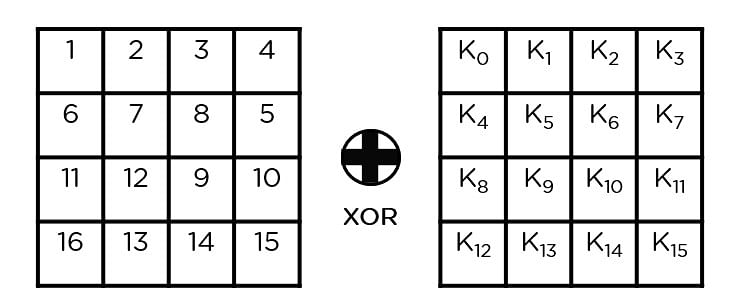
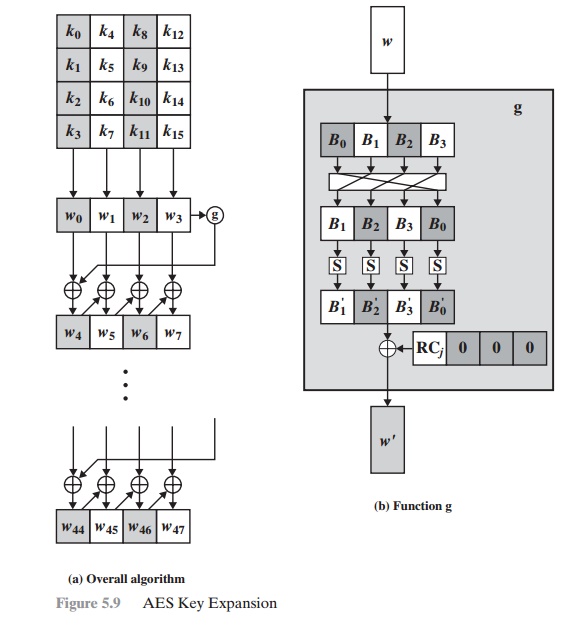
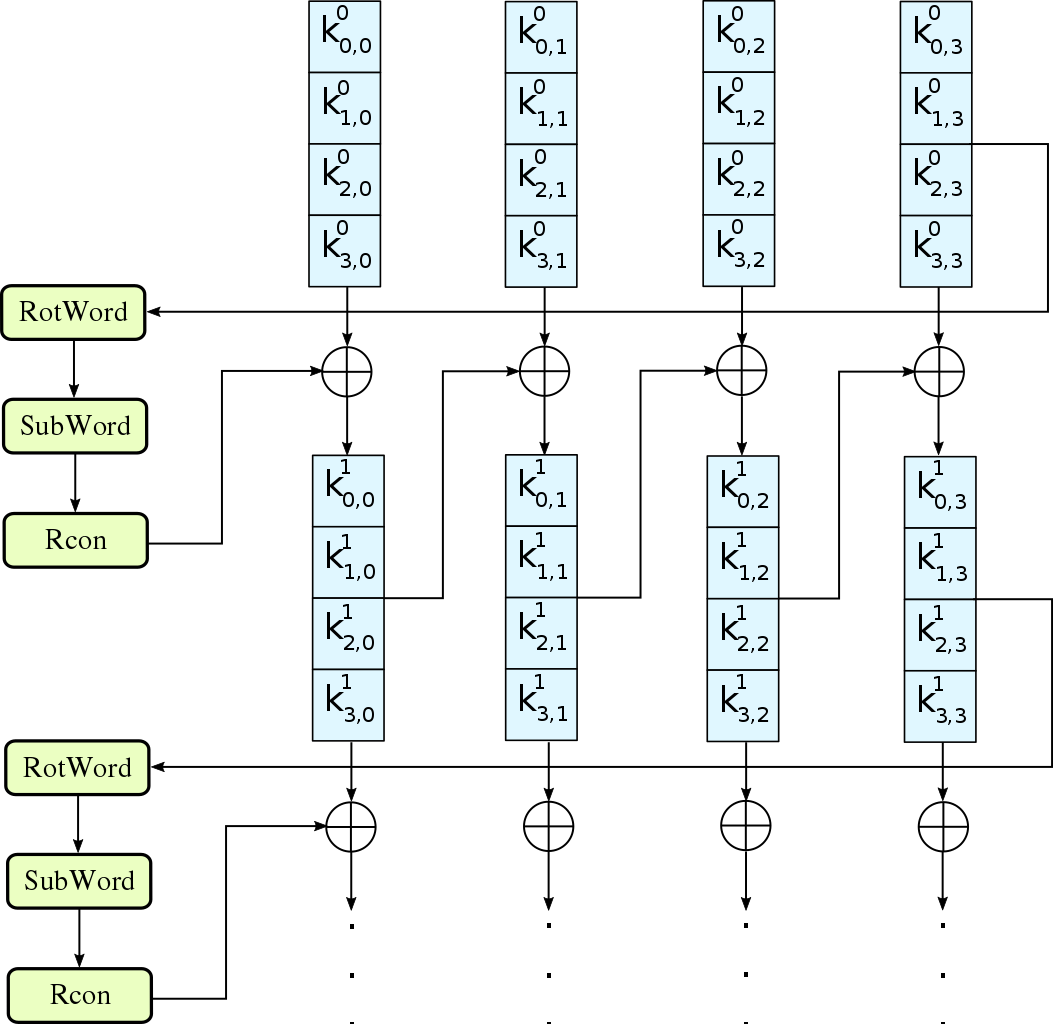
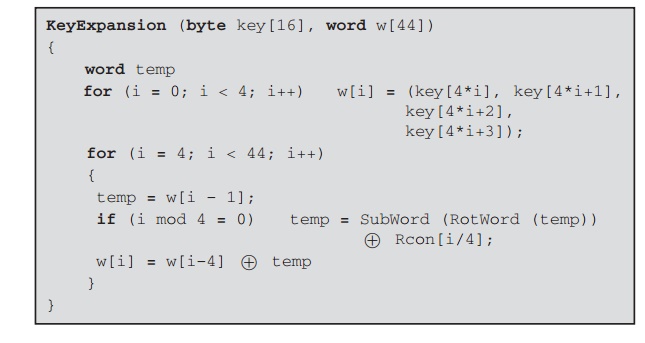
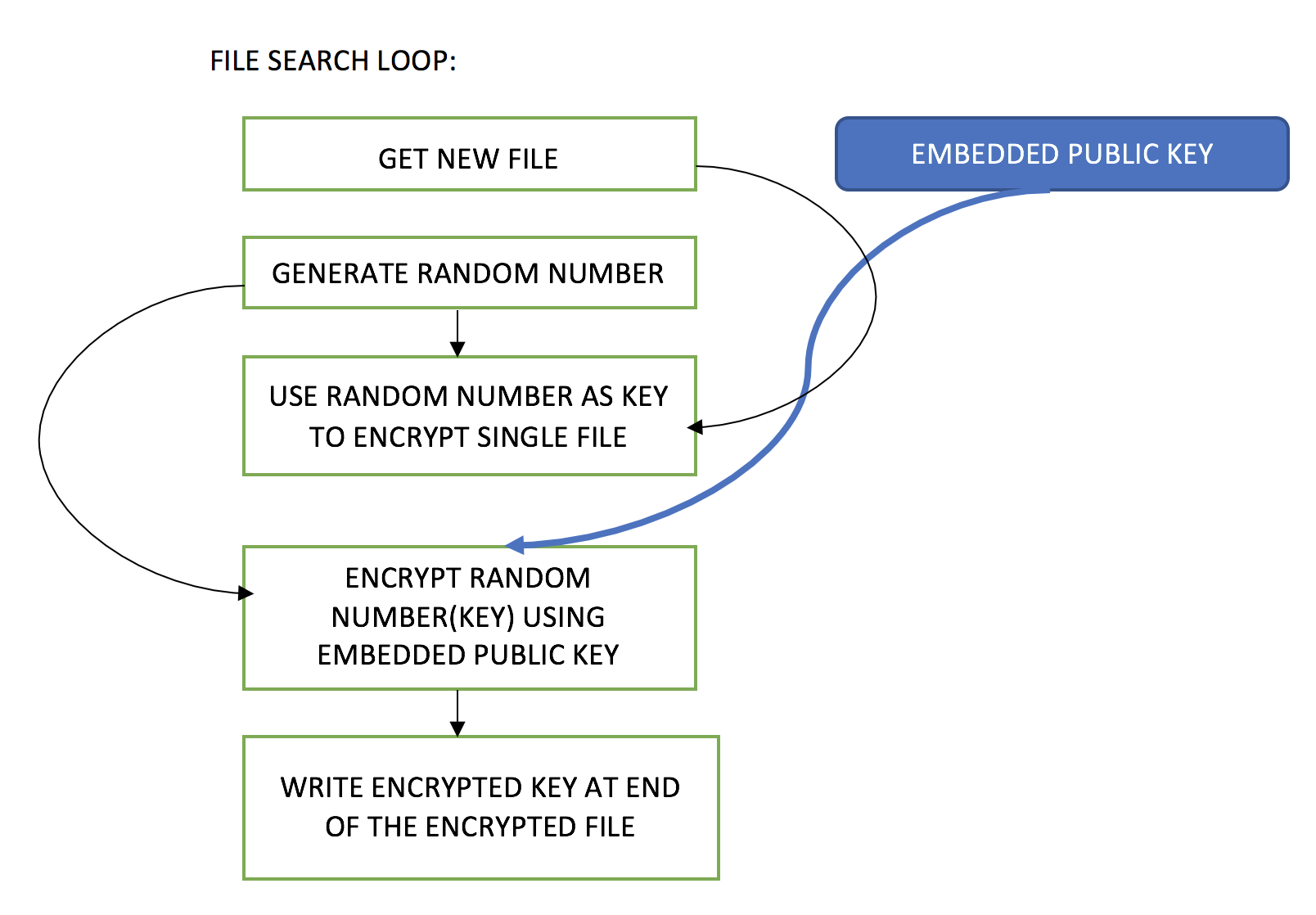
security - how to using Custom Master Key to generate plain key and encrypt key with java - Stack Overflow

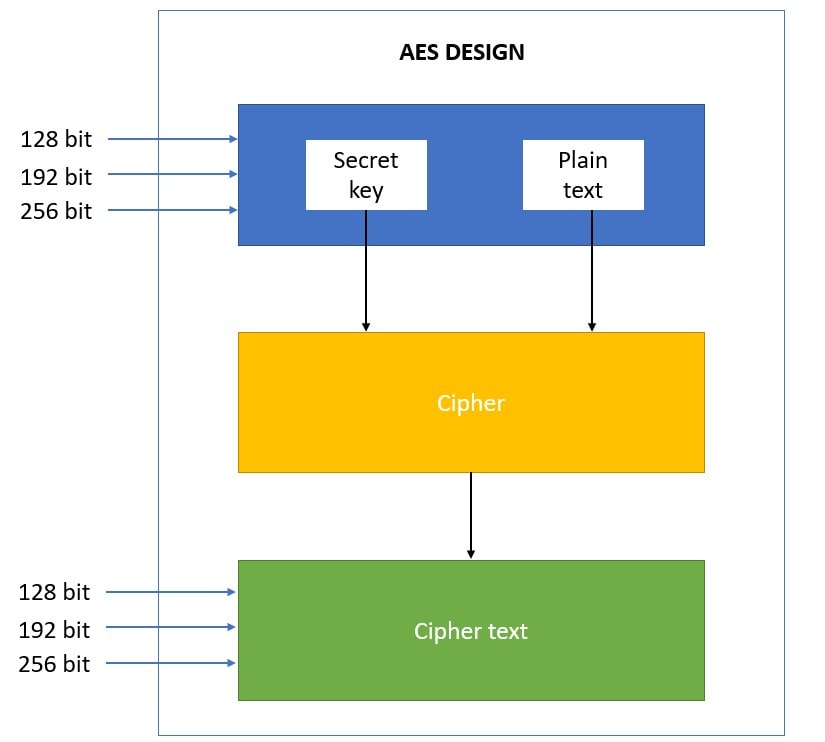
Figure: Structure of AES III. Implementation The AES algorithm is based... | Download Scientific Diagram

Hardware Software Co-Simulation of Obfuscated 128-Bit AES Algorithm for Image Processing Applications | Semantic Scholar
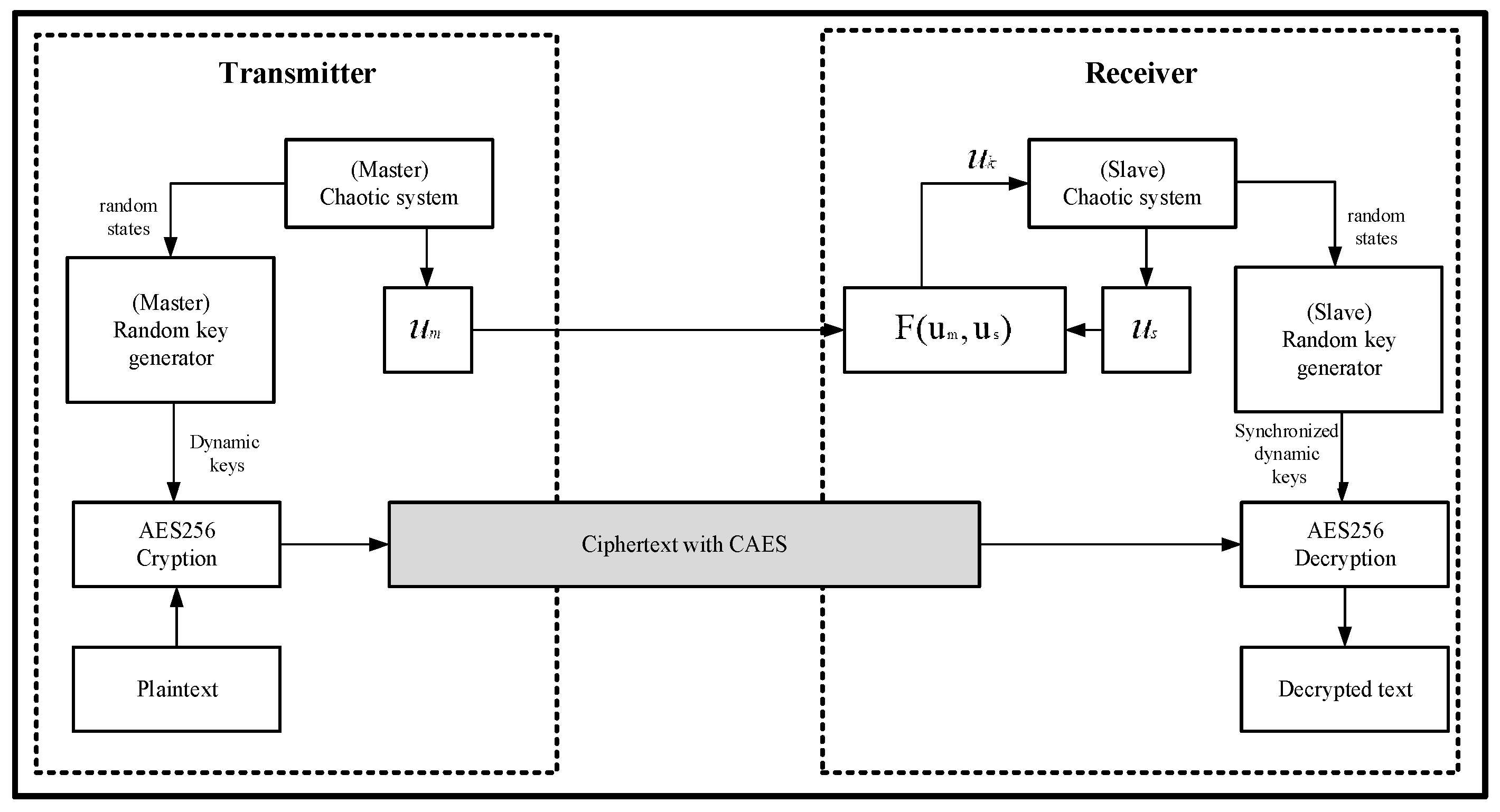
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm
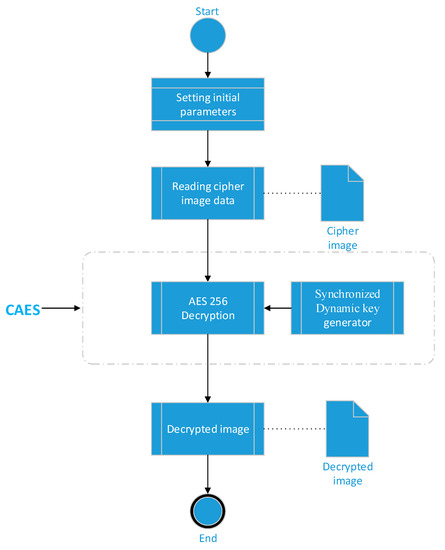
Applied Sciences | Free Full-Text | Chaos-Based Synchronized Dynamic Keys and Their Application to Image Encryption with an Improved AES Algorithm

Security aspects of removing a user from an organization or collection - Vaultwarden Forum (formerly Bitwarden_RS)