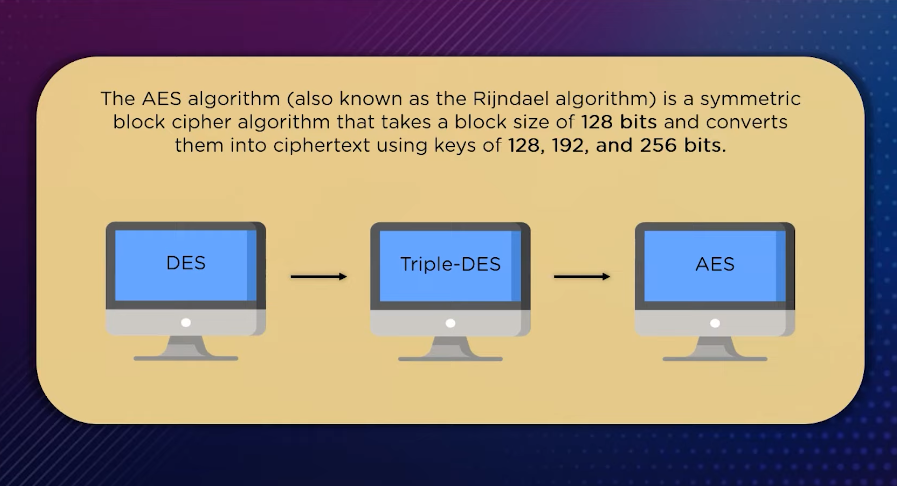
Use of Digital Signature with Diffie Hellman Key Exchange and AES Encryption Algorithm to Enhance Data Security in Cloud Computing | Semantic Scholar
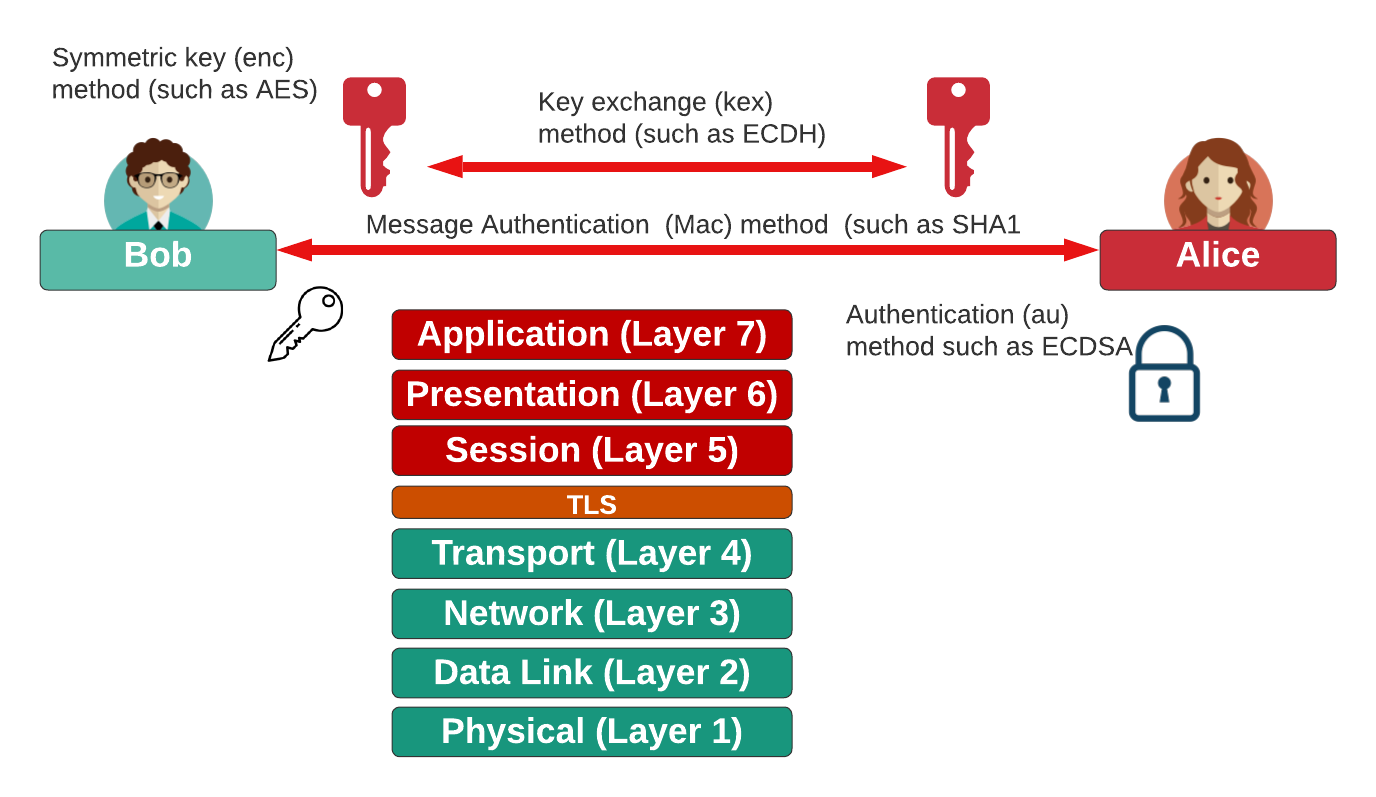
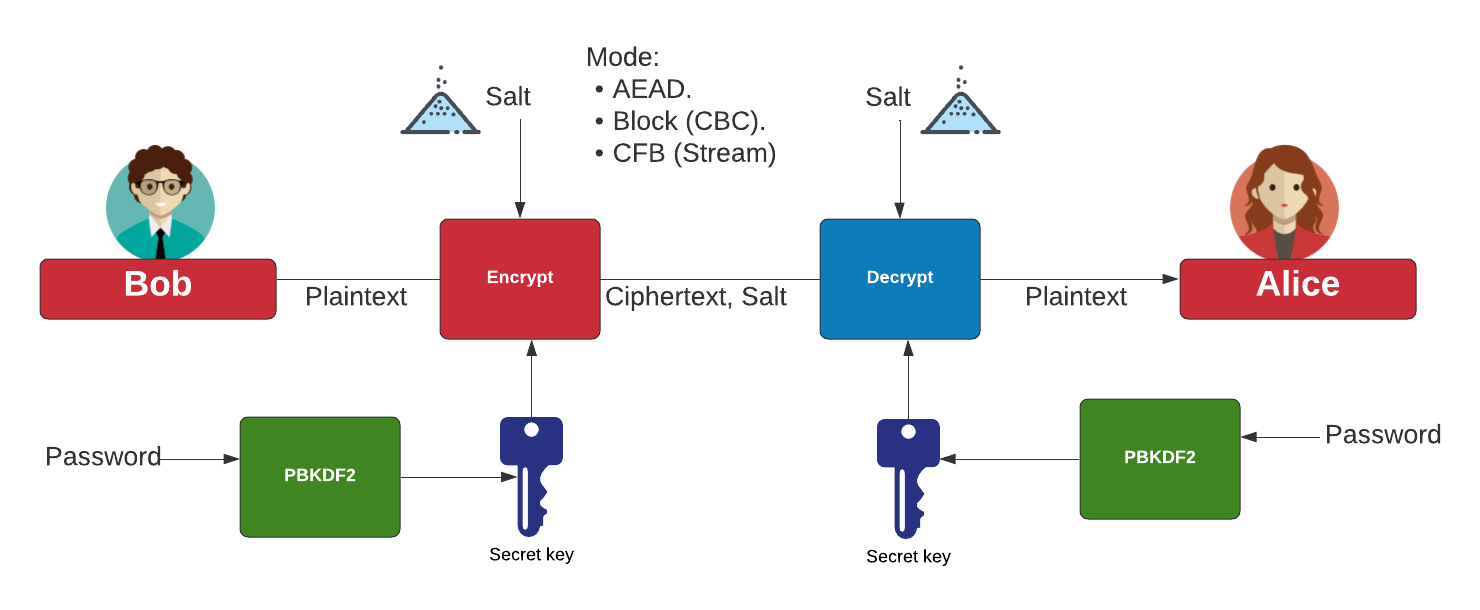
What's a Cipher Suite in TLS?. Like it or not, our online privacy and… | by Prof Bill Buchanan OBE | ASecuritySite: When Bob Met Alice | Medium
GitHub - patmull/diffie-hellman-aes-sha: Code used for demonstrating the principle of Diffie-Hellman key exchange alghorithm with AES and SHA256.
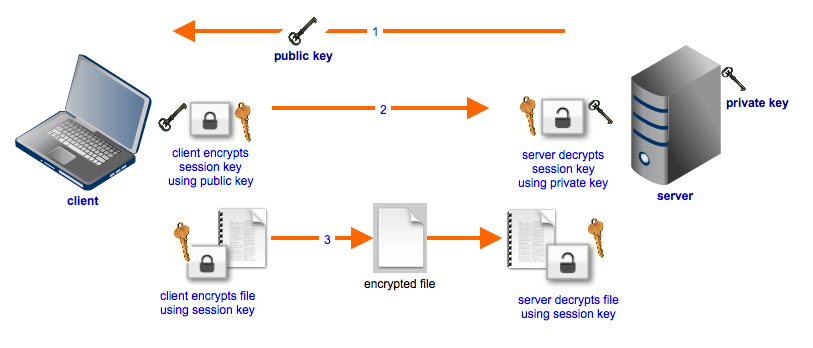
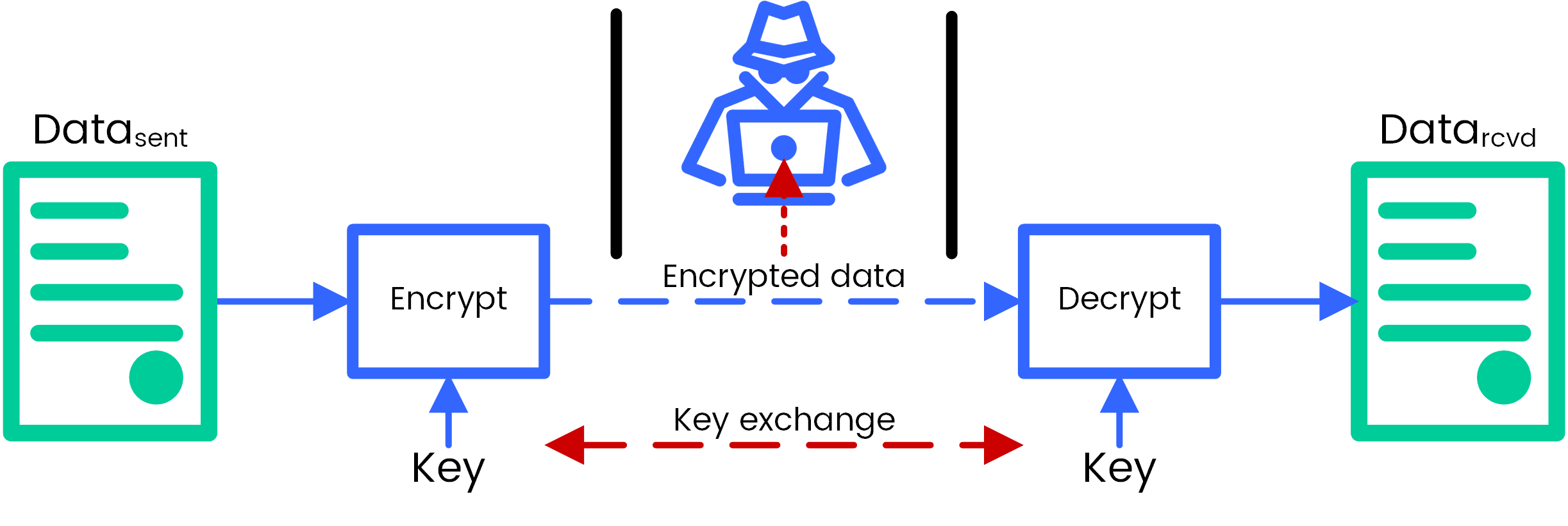
How to securely exchange encryption & decryption keys over a public communication network? | by Dasitha Abeysinghe | Medium

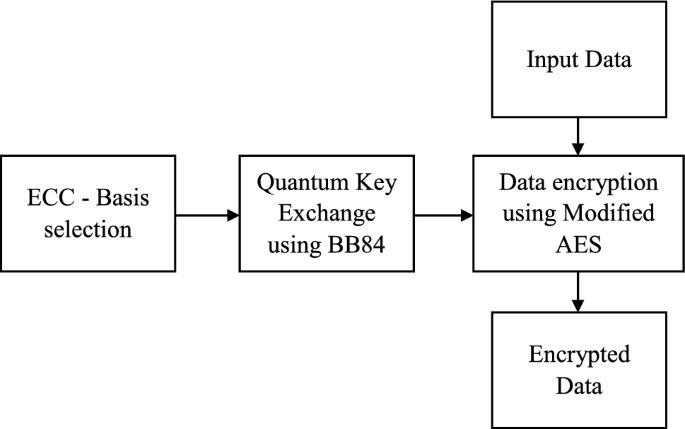
Key Management Using Combination of Diffie–Hellman Key Exchange with AES Encryption | Semantic Scholar
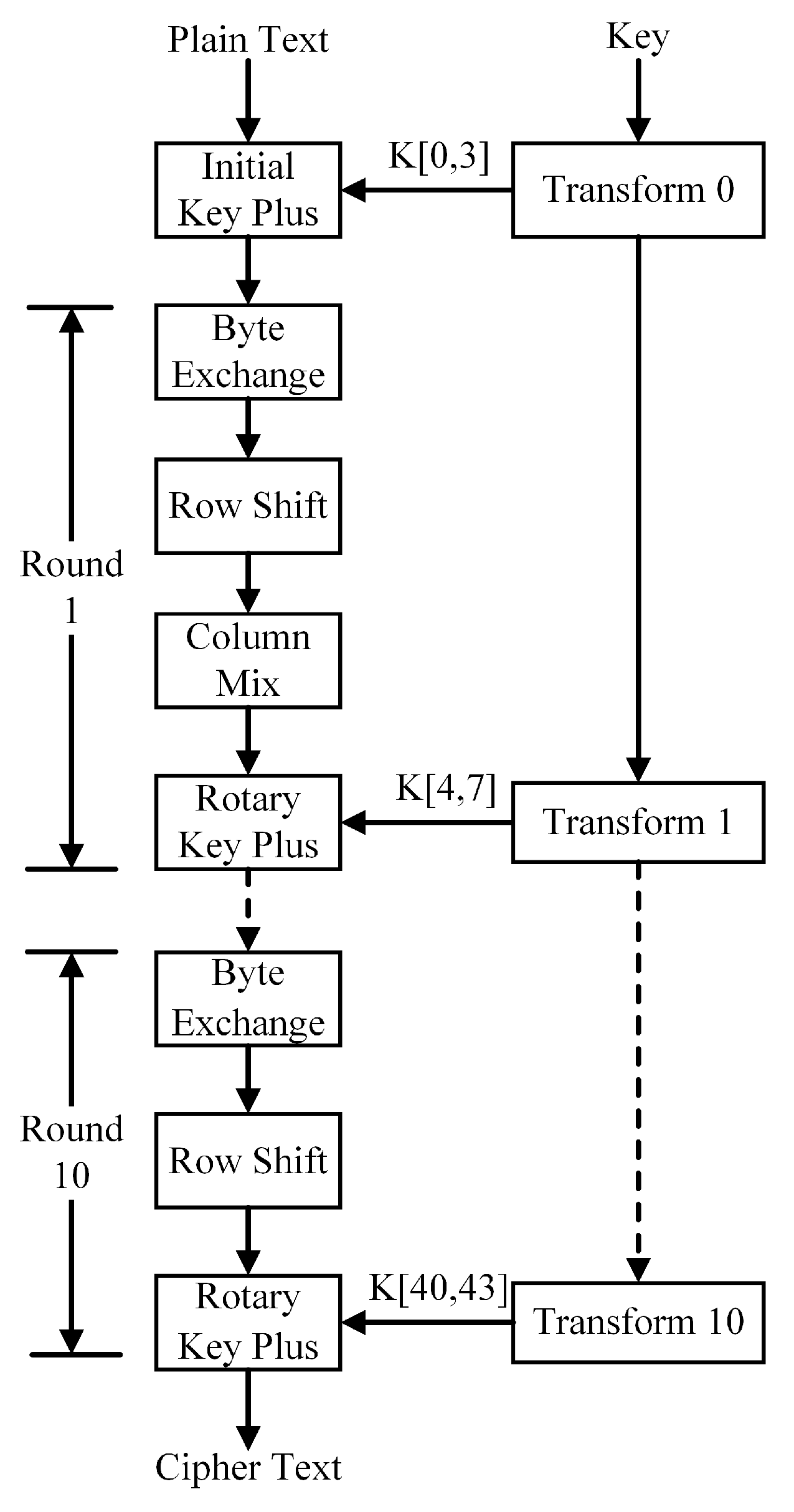
Applied Sciences | Free Full-Text | HAE: A Hybrid Cryptographic Algorithm for Blockchain Medical Scenario Applications

Key Management Using Combination of Diffie–Hellman Key Exchange with AES Encryption | Semantic Scholar